Over 48,800 internet-exposed Cisco ASA and FTD firewalls remain vulnerable to two critical flaws enabling remote code execution and VPN compromise. Despite weeks of active exploitation and government emergency directives, organizations globally have failed to patch, leaving networks open to attacks deploying sophisticated malware. U.S. and U.K. cybersecurity agencies confirm hackers are weaponizing these vulnerabilities to implant persistent bootkits.
Critical Cisco Firewall Flaws Exploited Amid Slow Patching Response

Nearly 50,000 Cisco Adaptive Security Appliance (ASA) and Firewall Threat Defense (FTD) devices remain exposed to two actively exploited vulnerabilities (CVE-2025-20333 and CVE-2025-20362), despite warnings from Cisco and emergency directives from governments. These unauthenticated remote code execution flaws allow attackers to bypass security controls and compromise VPN access points—putting corporate networks at severe risk.
The Anatomy of the Threat
The vulnerabilities enable attackers to:
- Execute arbitrary code without authentication
- Access restricted VPN configuration endpoints
- Deploy malware implants for persistent access
Cisco confirmed active exploitation began before patches were available, with threat actors scanning for vulnerable devices as early as late August. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) responded with an unprecedented 24-hour mitigation deadline for federal agencies, noting:
"These flaws pose such critical risks that end-of-life devices must be immediately disconnected from federal networks."
Global Exposure: A Patching Crisis
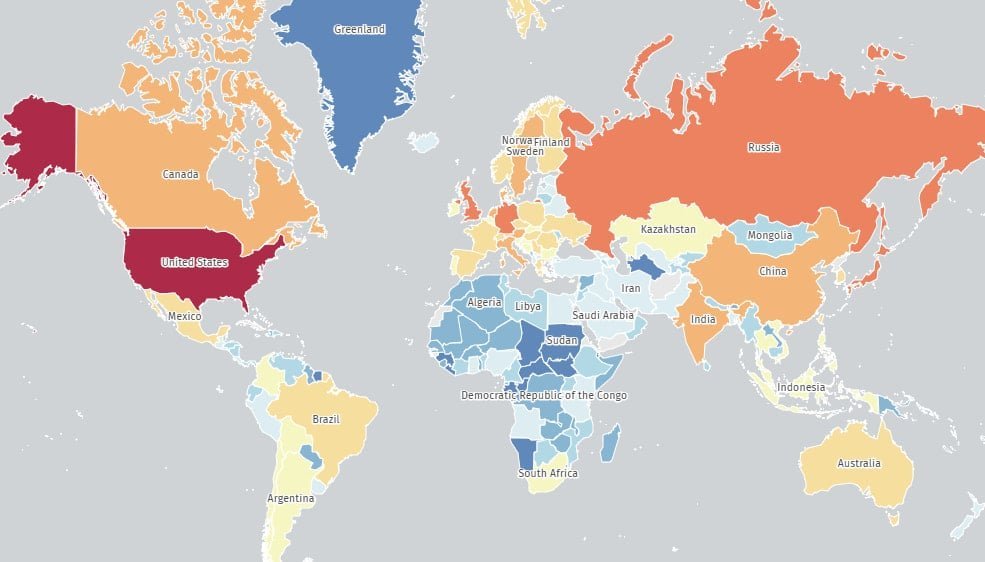
Shadowserver Foundation scans reveal alarming exposure levels:
- 48,800+ vulnerable devices internet-facing
- 19,200 in the United States (highest concentration)
- 2,800 in the United Kingdom
- Thousands more across Japan, Germany, Russia, and Canada
This massive attack surface persists despite:
- Cisco's September 25th confirmation of active exploits
- CISA's emergency directive for federal networks
- The U.K.'s NCSC disclosing attackers deploy 'Line Viper' shellcode loaders and 'RayInitiator' GRUB bootkits
Why This Matters for Security Teams
These firewalls often protect network perimeters and VPN gateways—making compromise catastrophic. Successful attacks enable:
- Lateral movement into internal networks
- Credential harvesting from VPN portals
- Persistent backdoors surviving reboots via bootkits
With no workarounds available, Cisco's guidance is unambiguous: Patch immediately. Temporary mitigations include:
1. Restrict VPN web interface exposure
2. Enhance monitoring for suspicious VPN login patterns
3. Audit HTTP requests for exploitation patterns
The Urgent Call to Action
Security teams must prioritize:
- Verifying ASA/FTD patch status using Cisco's advisories (CVE-2025-20333, CVE-2025-20362)
- Isolating non-patchable end-of-life devices
- Treating unpatched firewalls as actively compromised
As one cybersecurity analyst noted: "When state agencies issue 24-hour directives and bootkits enter the equation, we're beyond theoretical risk—this is battlefield triage for network defenses."
Source: BleepingComputer

Comments
Please log in or register to join the discussion