Apple has quietly turned the U.S. passport into a cryptographic anchor for a new Digital ID in Wallet, now rolling out nationwide. Beyond convenience at TSA, this move sketches an ecosystem where identity becomes an API—raising big opportunities for developers and serious questions for regulators and rivals.
 )
)
Source: 9to5Mac
A New Identity Primitive Lands in Your Pocket
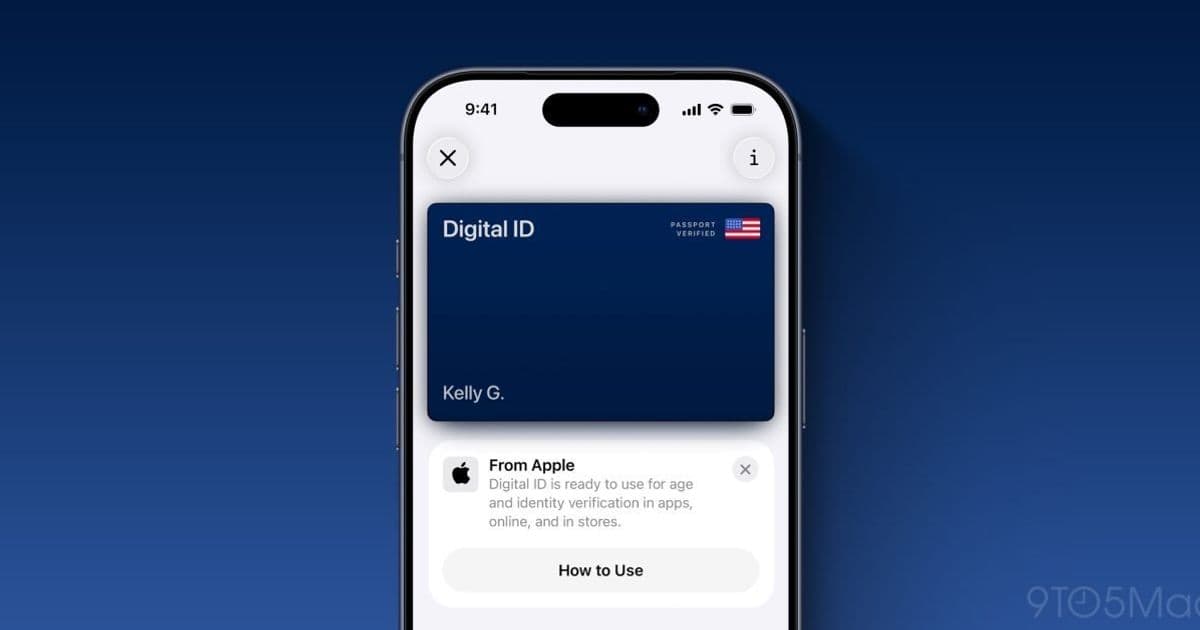
Apple’s long-teased Digital ID for Wallet has officially launched in the United States—and this time it’s not gated by state-by-state bureaucracy. By anchoring verification to the U.S. passport, Apple has effectively shipped a nationally portable, device-bound identity credential that works today at hundreds of TSA checkpoints for domestic travel, with a clear roadmap into apps, websites, and physical venues.
For developers, security architects, and product teams, this is not just a UX nicety. It’s the emergence of a hardware-backed, privacy-preserving identity layer that Apple controls end-to-end. And it’s one API integration away from reshaping how we do age checks, KYC, account verification, and fraud prevention.
How Apple’s Digital ID Actually Works
Digital ID in Wallet is not a raw digital passport nor a simple photo of your document. It’s a derived, cryptographically bound credential created via an on-device enrollment flow:
- Open Wallet on iPhone.
- Tap the + button.
- Select “Driver’s License or ID Cards.”
- Choose “Digital ID” and follow the prompts.
The setup pipeline:
- The user scans their U.S. passport, including reading the embedded NFC chip on the back.
- They capture a selfie and perform guided facial/head movements.
- On-device biometrics (Face ID/Touch ID) are tied into the verification flow.
- Within minutes, a Digital ID appears in Wallet, resident on that device.
This is a derived identity: your passport is the trust anchor, but Digital ID is its own credential. Apple explicitly notes this is not a full digital passport replacement, especially for international travel.
Security and Privacy Engineering Under the Hood
Apple is leaning hard on a familiar combination of the Secure Enclave, local-only data, and selective disclosure:
- Data residency: Passport-derived data is stored on-device, not in an Apple identity cloud.
- Encryption: Digital ID data is encrypted at rest and bound to the device’s secure hardware.
- Local control: Apple says it cannot see when, where, or how you present your ID, nor what subset of data you share.
- Biometric gatekeeping: Presenting the Digital ID requires Face ID or Touch ID—no casual or coerced hand-over of the whole device.
- Selective disclosure: Relying parties can request specific attributes (e.g., “21+?”, “name + photo”), and the user must approve exactly what’s shared.
In other words, Apple is shipping a practical implementation of least-privilege identity verification. Instead of flashing your home address to buy a beer, you present a cryptographic yes/no or a minimal field set.
This aligns with broader trends in decentralized identity and verifiable credentials, but with a crucial twist: Apple is not pitching this as DID/VC per se. It’s Apple’s vertically integrated, highly curated version—familiar to anyone who’s watched them do payments, passkeys, and health data.
Where You Can Use It Today (and Why TSA Is Just the Start)
At launch, Digital ID is supported at TSA checkpoints across more than 250 U.S. airports for domestic travel. The flow is tellingly "no-hand-over":
- Double-click the side or Home button.
- Select Digital ID in Wallet.
- Hold iPhone or Apple Watch near an identity reader.
- Review requested data.
- Approve via Face ID or Touch ID.
Critically, you never unlock your phone for an agent, and they never get to scan everything on your card.
Apple says “additional Digital ID acceptance use cases” are coming soon:
- Select businesses and organizations.
- Online age verification and identity checks in apps.
- Example teased: verifying age in Uber Eats for alcohol purchases.
This is where it gets strategically important. Once major platforms and merchants can call a standardized, high-assurance, hardware-secured identity signal from Wallet, Digital ID stops being a travel perk and starts becoming an infrastructure primitive.
Apple’s Workaround for America’s Identity Fragmentation
The cleverness here is political as much as technical.
Mobile driver’s licenses in Wallet launched in 2022 but have been throttled by state-by-state negotiations, vendor lock-in concerns, and uneven governance models. As of now, only a small set of states and Puerto Rico support Apple Wallet IDs.
By using the U.S. passport—a federal document Apple doesn’t issue but can cryptographically verify—Apple sidesteps that gridlock. Anyone with a passport can now create a Digital ID, regardless of:
- Whether their state supports mobile IDs.
- Whether their plastic license is REAL ID-compliant.
This dramatically broadens Apple’s addressable user base and gives relying parties a single, predictable integration path instead of 50+ regulatory snowflakes.
From an ecosystem standpoint, Apple has:
- Reduced dependency on state-level timelines.
- Anchored Digital ID in an already trusted federal credential.
- Tightened the loop between hardware, OS, Wallet, and identity verification.
Implications for Developers and Security Teams
If you build products that care about who a user is—not just that they control an email or phone number—this announcement should be on your roadmap.
Key implications:
High-assurance identity as a platform primitive
- Today: Payment tokens (Apple Pay), passkeys, app attestation.
- Now: Device-bound, passport-backed Digital ID.
- Soon: A developer-facing identity signal that could rival traditional KYC vendors for consumer scenarios.
Selective disclosure as a UX and compliance win
- Age-gated commerce (alcohol, tobacco, restricted content).
- Mobility and gig services (ridesharing drivers/riders, delivery couriers).
- Access control (co-working, campuses, events).
- Each can request only the minimum attributes needed, reducing overcollection risks that regulators increasingly target.
Fraud reduction, if implemented well
- Device + biometric + cryptographically bound ID is materially harder to fake than a JPEG of a license.
- This could pressure legacy “upload your ID” workflows to modernize—and deprecate data-leaky, phishing-prone flows.
Integration and lock-in dynamics
- Expect Apple to expose tightly controlled APIs and frameworks (similar to Tap to Present ID at TSA) for third-party apps and web.
- That will make onboarding flows smoother on iOS—but may deepen concerns about platform lock-in and competitive neutrality.
For now, developers should be watching for:
- Documentation on accepted relying-party use cases.
- Attribute schemas (age, name, photo, ID validity, etc.).
- Consent UX patterns mandated by Apple’s HIG and review guidelines.
- Any hints of cross-platform standardization versus Apple-only design.
Trust, Governance, and the Quiet Power Grab
Digital ID systems are never purely technical. They encode power structures: who can verify, who can revoke, who can observe.
Apple stresses three pillars:
- Users stay in control.
- Minimal data shared per transaction.
- Apple can’t see when or how IDs are used.
On paper, this is strong—and significantly better than today’s physical ID overexposure model.
Still, critical questions for the technical and policy community remain:
- Revocation and lifecycle: What happens if your passport expires, is revoked, or compromised? How fast and transparent is the unlinking of your Digital ID?
- Cross-jurisdiction risk: Could future regulations compel Apple or partners to alter what data is exposed or logged?
- Interoperability: Will this plug cleanly into open identity standards (W3C Verifiable Credentials, ISO 18013-5/7 for mDL), or remain a premium Apple-only credential?
- Market power: As Apple accumulates payments, credentials, and identity, where is the line between user security and ecosystem dominance?
These aren’t reasons to dismiss the feature. They are reasons for security engineers, policymakers, and standards bodies to be at the table now, while Digital ID adoption is still in its formative stage.
Why This Launch Matters More Than It Looks
Strip away the glossy Wallet animations and TSA convenience, and Apple’s Digital ID is something bigger: a production-scale experiment in making strong, privacy-preserving identity native to consumer devices.
If it works—technically, politically, and commercially—it will:
- Normalize selective disclosure over data sprawl.
- Reduce reliance on brittle document-scan workflows.
- Give developers a secure identity primitive that feels as seamless as Apple Pay.
If it doesn’t, we’ll learn a lot about the boundaries of platform power and the public’s appetite for letting a private company mediate something as fundamental as legal identity.
But make no mistake: for the first time, anyone in the U.S. with a passport and an iPhone can carry a device-bound, cryptographically verified ID that’s already accepted at scale.
For a world increasingly built on APIs, that’s not a side story. That’s infrastructure.
Comments
Please log in or register to join the discussion