A newly disclosed vulnerability in Cisco's IOS and IOS XE operating systems allows attackers to remotely execute code with root privileges or cause denial-of-service on affected devices. With evidence of active exploitation and millions of systems exposed via misconfigured SNMP protocols, this flaw demands urgent patching to prevent widespread network breaches. Security experts warn that compromised credentials could turn this into a supply-chain nightmare.

In a stark reminder of how foundational network infrastructure remains vulnerable, Cisco has disclosed a critical zero-day flaw affecting its IOS and IOS XE operating systems—software that underpins routers, switches, and other core networking devices globally. Tracked as CVE-2025-20352, this vulnerability is already being exploited in the wild, putting an estimated 2 million devices at risk of remote takeover or disruption, according to security researchers.
The Anatomy of the Vulnerability
The flaw stems from a stack overflow bug in the component handling SNMP (Simple Network Management Protocol), a standard tool for monitoring and managing network devices. Attackers can exploit it by sending maliciously crafted SNMP packets. Crucially, the impact varies based on attacker privileges:
- Remote Code Execution (RCE): With a valid read-only SNMP community string (often default or widely shared credentials) and administrative access, attackers can execute arbitrary code with root privileges, granting unfettered control over the device. As independent researcher Kevin Beaumont noted, "If you get RCE as root, you’re getting higher than admin privileges—you’re not supposed to be able to get root on those devices."
- Denial-of-Service (DoS): Even without high privileges, attackers can crash vulnerable devices using just a read-only string or SNMPv3 credentials, paralyzing network operations.
Cisco has assigned a severity rating of 7.7/10, emphasizing that the PSIRT team confirmed active exploitation after local administrator credentials were compromised. The vulnerability affects all supported IOS and IOS XE versions, with patches released in Cisco's September update alongside 13 other flaws, including several rated up to 8.8 in severity.
Why This Matters: Exposure and Implications
What amplifies the threat is the alarming number of devices exposed online. SNMP is typically intended for internal network use, but Shodan—a search engine for internet-connected devices—reveals over 2 million Cisco systems with SNMP interfaces publicly accessible. This misconfiguration, often due to oversight, creates a low-barrier entry point for attackers.
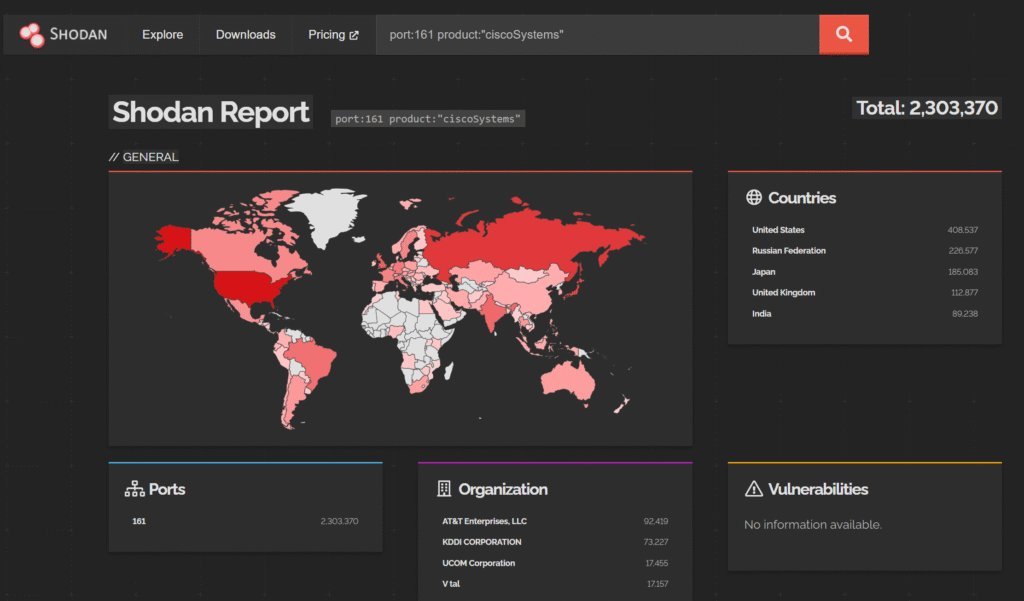 Credit: Kevin Beaumont
Credit: Kevin Beaumont
Beaumont's Shodan data visualization underscores the global scale of the risk, with hotspots in enterprise and service provider networks. For developers and network engineers, this isn't just a patching exercise—it's a wake-up call about supply-chain security. A single compromised device could serve as a springboard for lateral movement, data exfiltration, or ransomware deployment across interconnected systems.
Mitigation and the Path Forward
Cisco strongly recommends immediate patching as the only complete solution, with no viable workarounds. For teams unable to update swiftly, mitigating steps include:
- Restricting SNMP access to trusted users only.
- Monitoring devices using the
snmpcommand in terminal sessions to detect anomalies. - Auditing and hardening SNMP credentials to eliminate defaults.
This incident highlights broader industry challenges: the persistence of legacy protocols like SNMP in critical infrastructure and the cascading risks of credential mismanagement. As networks evolve toward zero-trust architectures, proactive vulnerability management isn't optional—it's existential. Failing to act could turn millions of devices into unwitting pawns in the next major cyber campaign.
Source: Based on reporting by Dan Goodin for Ars Technica.

Comments
Please log in or register to join the discussion