DoorDash's latest data breach, stemming from a social engineering attack on an employee, highlights the persistent security challenges facing major digital platforms. The incident, the third for the company since 2019, raises critical questions about employee training and incident response protocols in high-volume tech services.
DoorDash's Third Breach in Six Years Exposes Persistent Security Vulnerabilities
DoorDash has disclosed yet another data breach, this time occurring in October 2025, affecting millions of customers across its global operations. The incident, which stemmed from a social engineering attack targeting an employee, has reignited concerns about security practices at major gig economy platforms and the adequacy of their incident response protocols.
The October 2025 Incident
According to DoorDash's notification, the breach was identified on October 25, 2025, when an unauthorized third party gained access to and exfiltrated user contact information. The compromised data varied by individual but potentially included:
- First and last name
- Physical address
- Phone number
- Email address
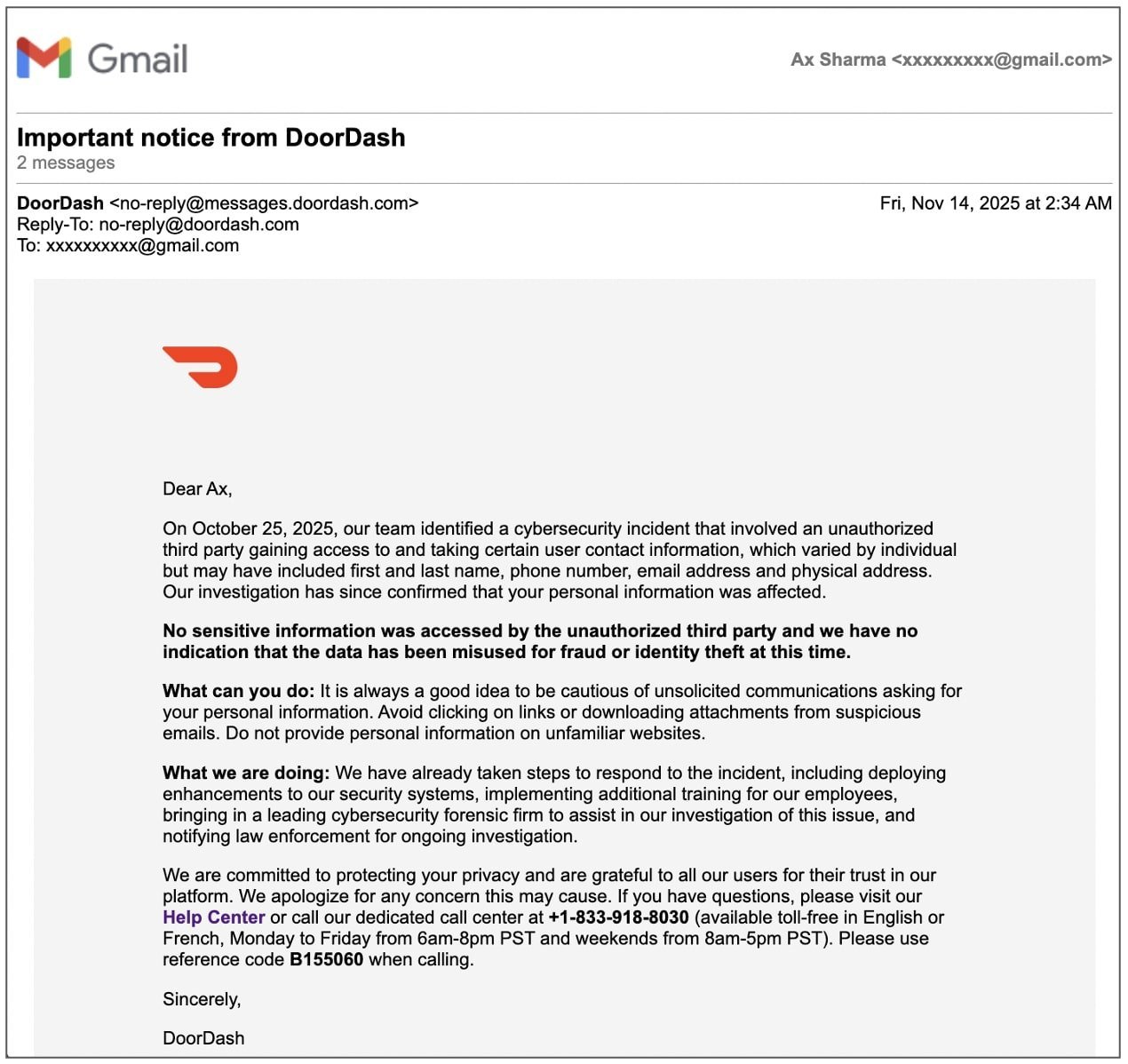
The company began notifying affected users via email on November 12, 2025, approximately 19 days after discovering the breach. This delay has already drawn criticism from security professionals and affected users.
Root Cause: A Familiar Vulnerability
DoorDash's investigation traced the incident to an employee falling victim to a social engineering scam. This attack vector—manipulating individuals into divulging credentials or performing actions that compromise security—remains one of the most persistent threats in cybersecurity.
Upon discovering the unauthorized access, DoorDash's incident response team took immediate action by:
- Shutting down the unauthorized party's access
- Launching a comprehensive investigation
- Referring the matter to law enforcement
The company has since deployed additional security enhancements, implemented extra employee training, and brought in a third-party cybersecurity firm to assist with the investigation.
A Pattern of Breaches
This latest incident marks the third significant security breach for DoorDash in recent years:
- 2019: A data breach exposed the information of approximately 5 million customers, Dashers (delivery drivers), and merchants.
- August 2022: DoorDash suffered another breach as part of a broader attack that also targeted communications platform Twilio.

The recurrence of security incidents suggests systemic challenges that extend beyond isolated vulnerabilities. For security professionals, this pattern raises important questions about the effectiveness of DoorDash's security program and whether the company is adequately addressing root causes rather than just symptoms.
Geographic Scope and Notification Concerns
Initial reports indicate that email notifications primarily targeted DoorDash users in Canada. However, an undated security advisory on DoorDash's website references U.S.-specific data types like Social Security Numbers (SSNs), which the company claims were not accessed. This has led to speculation about whether the breach extends beyond Canada to other markets, including the United States.
The inconsistent messaging about the breach's geographic scope has further complicated the company's response. Security experts emphasize that transparency is critical during breach notifications to enable affected individuals to take appropriate protective measures.
User Reactions and Legal Implications
The breach has triggered significant backlash on social media, with users criticizing DoorDash's handling of the incident and the timing of notifications.
"I'm sorry - if this isn't sensitive information, what is? Don't downplay this just because they didn't get credit card or password information," posted Chris from Toronto.
Cybersecurity professional Kostas T. pointed out the contradiction in DoorDash's messaging: "The statement 'no sensitive information was accessed' conflicts with the personal information that the company acknowledged was accessed."
One user, itsohqay, expressed particular frustration: "DoorDash took 19 whole days to notify me of a data breach that has leaked my personal information. Thankfully I used a fake name and forwarded email address for my account, but my real phone number and physical address have been leaked."
This user further stated: "This is incredibly unprofessional, dangerous, and potentially illegal behaviour from DoorDash... This process violates Canadian data breach law. I'll be filing a case against DoorDash in provincial small claims court and making a complaint to the Office of the Privacy Commissioner of Canada."
Security Implications for the Industry
The DoorDash breach serves as a stark reminder that even well-funded technology companies can fall victim to basic security failures. For security professionals and developers, several key lessons emerge:
Social engineering remains a primary threat vector: Companies must invest in comprehensive security awareness training that goes beyond annual phishing simulations to create a culture of security vigilance.
Incident response timelines matter: The 19-day delay between discovery and notification potentially exposed users to increased risk of phishing attacks and identity theft. Organizations should establish clear SLAs for breach notifications.
Data minimization is critical: The fact that contact information was stored at all raises questions about data governance practices. Companies should regularly audit and reduce the data they collect and retain.
Third-party risks require management: As DoorDash demonstrated by bringing in external cybersecurity experts, organizations should have pre-vetted relationships with specialized incident response firms.
Recommendations for Affected Users
DoorDash has advised users to be cautious of potential phishing attempts following the breach:
- Avoid clicking on links or attachments in suspicious emails claiming to be from DoorDash
- Do not provide personal information to unfamiliar websites
- Monitor accounts for unusual activity
- Consider placing fraud alerts on credit reports
The company has established a toll-free number (+1-833-918-8030) with reference code B155060 for users with additional questions.
The Path Forward for DoorDash
For DoorDash, this incident represents another critical juncture in its security journey. The company must demonstrate that it has learned from previous breaches by implementing substantive security improvements rather than cosmetic changes.
Security professionals will be watching closely to see how DoorDash addresses the underlying issues that have allowed multiple breaches to occur. The company's response will not only impact its reputation but may also influence security practices across the broader gig economy sector.
As digital platforms continue to handle increasingly sensitive data, the DoorDash breach serves as a cautionary tale about the importance of security as a core business function rather than an afterthought. In an era where data breaches have become commonplace, organizations must move beyond breach response to true breach prevention.

Comments
Please log in or register to join the discussion