In October, DoorDash fell victim to a social‑engineering scam that exposed personal data for millions of users across North America and Australasia. The incident, the company’s delayed notification, and the legal fallout underscore how even large tech firms can be blindsided by human‑factor attacks.
DoorDash’s Latest Breach: A Social‑Engineering Slip‑Up with Global Fallout

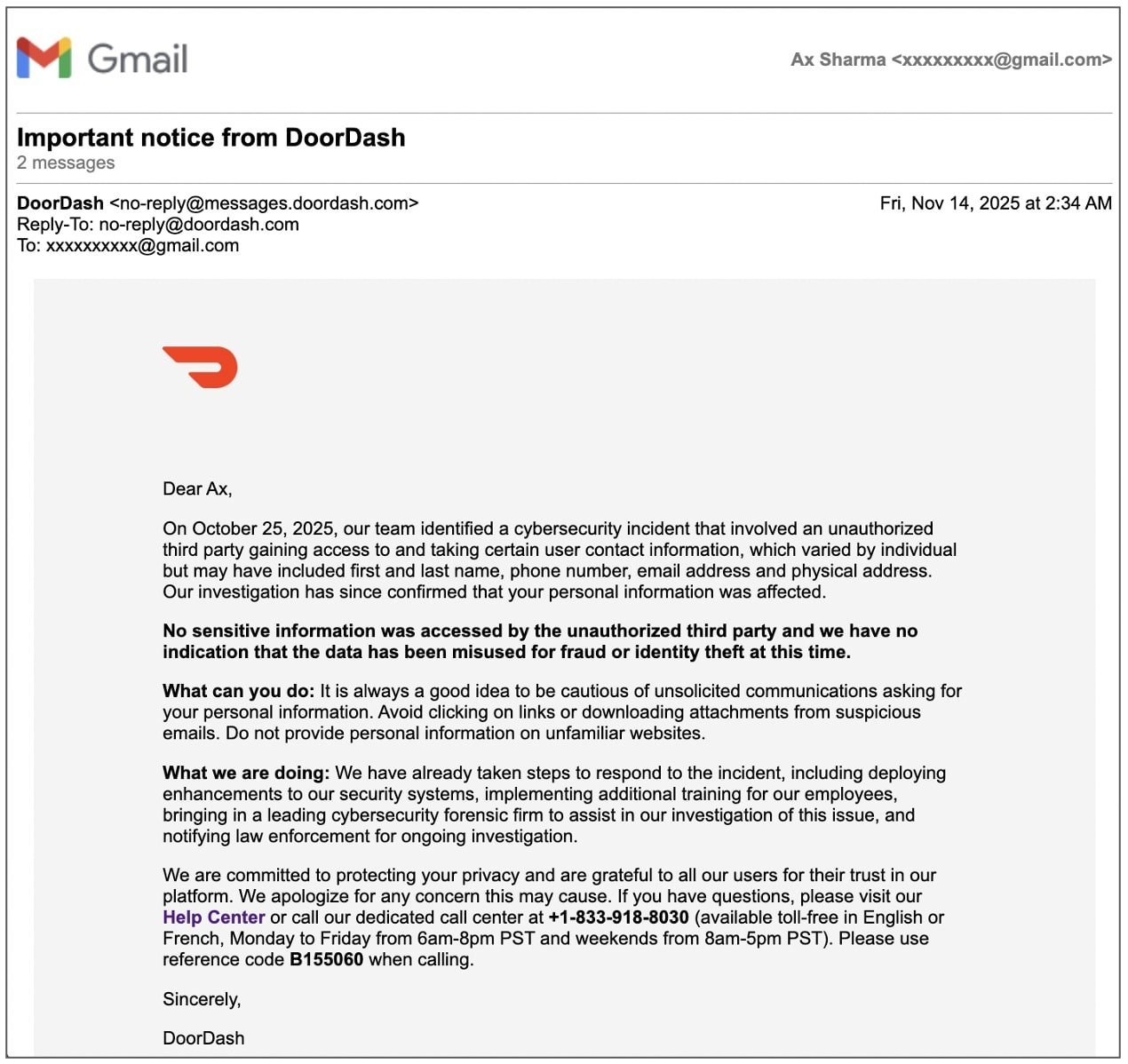
On October 25, 2025, DoorDash’s security team identified an unauthorized third‑party intrusion that compromised user contact information—first and last names, addresses, phone numbers, and email addresses. The breach, traced back to a single employee who fell for a social‑engineering scam, is the company’s third major data incident in six years.
The Human Factor Behind the Numbers
Unlike the 2019 breach that exposed data for roughly five million customers and the 2022 incident linked to the Twilio attack, this October event was initiated by an employee’s credentials being compromised. The perpetrator exploited a phishing email that convinced the employee to reveal login details. Once the attacker had access, DoorDash’s incident‑response team shut down the breach, launched an investigation, and involved law enforcement.
"Our investigation has since confirmed that your personal information was affected," DoorDash wrote in an email sent to impacted users.
The company’s notification, however, sparked criticism for its 19‑day delay. Users on social media expressed frustration:
"DoorDash took 19 whole days to notify me of a data breach that has leaked my personal information…" – X user Ohqay
This delay raises questions about compliance with Canadian privacy law, which requires notification within 72 hours of a breach that could cause harm.
Scope and International Reach
While the breach was initially reported to affect Canadian users, an undated advisory on DoorDash’s website hinted at a broader reach. The advisory referenced U.S. data types such as Social Security Numbers (SSNs) and noted that Canada’s equivalent, Social Insurance Numbers (SINs), were not accessed.
"At this time, it appears that the emails primarily went to DoorDash Canada users…" – BleepingComputer
BleepingComputer has reached out to DoorDash’s press team for clarification on whether U.S. or other international users were affected.
The Aftermath: Legal Implications and Consumer Trust
The breach’s fallout extends beyond immediate data exposure. A Canadian privacy commissioner may investigate potential violations, and users are considering legal action in small‑claims court. DoorDash’s response includes:
- Deployment of enhanced security systems
- Additional employee training
- Engagement of a leading cybersecurity forensic firm
- Ongoing law‑enforcement collaboration
Despite these measures, the incident underscores a persistent industry problem: social engineering remains the most effective vector for credential theft.
What Developers and Security Teams Should Take Away
- Zero‑Trust for Employees – Treat every login attempt as potentially malicious, regardless of the user’s role.
- Continuous Phishing Simulations – Regular, realistic training can reduce click‑through rates on malicious links.
- Rapid Notification Protocols – Automate breach detection and notification workflows to meet legal thresholds.
- Transparent Communication – Clear, timely updates preserve trust and mitigate reputational damage.
DoorDash’s latest breach serves as a stark reminder that even the most sophisticated platforms can be undone by a single weak link. The industry must prioritize human‑factor defenses as much as technical safeguards.
"Users should be wary of unsolicited communications or targeted phishing emails appearing to originate from DoorDash…" – BleepingComputer
For more details, see the full report on BleepingComputer.
{{IMAGE:4}}

Comments
Please log in or register to join the discussion