Security researcher Bobby Gould has released a complete exploit chain for CVE-2025-20281, a critical unauthenticated RCE vulnerability in Cisco ISE actively exploited in the wild. The demonstration includes container escape techniques, escalating threats for unpatched networks managing identity and access controls.
Exploit Published for Critical Cisco ISE Vulnerability Amid Active Attacks

Security researcher Bobby Gould has published a full technical breakdown of an exploit chain targeting CVE-2025-20281—a critical vulnerability in Cisco's Identity Services Engine (ISE) already under active exploitation. The flaw allows unauthenticated attackers to execute arbitrary code with root privileges, putting enterprise networks at risk of complete compromise.
Anatomy of a Critical Threat
Cisco initially disclosed the vulnerability on June 25, 2025, warning it impacts ISE and ISE-PIC versions 3.3 and 3.4. The flaw originates from unsafe deserialization and command injection in the enableStrongSwanTunnel() method. Later, Cisco expanded the advisory to include CVE-2025-20337, splitting the issue into two distinct CVEs:
- CVE-2025-20281: Command injection enabling arbitrary file uploads
- CVE-2025-20337: Unsafe deserialization flaw
Despite releasing hotfixes, Cisco confirmed active exploitation on July 22 and urged immediate upgrades to ISE 3.3 Patch 7 or 3.4 Patch 2.
The Exploit Chain Unveiled
Gould's technical write-up demonstrates how attackers can weaponize these flaws:
- Trigger command injection via a serialized Java
String[]payload - Bypass argument tokenization using
${IFS}(Internal Field Separator) with Java'sRuntime.exec() - Achieve root-level code execution inside a privileged Docker container
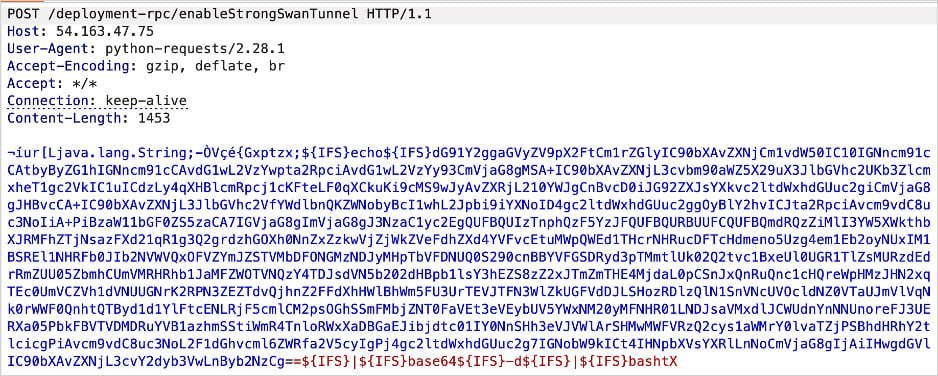
Malicious request triggering the exploit (Source: ZDI)
Critically, Gould details escaping the container to gain host system root access using a cgroups-based escape technique leveraging release_agent—a known but potent container breakout method.
Escalating Risk Landscape
While not a plug-and-play exploit script, Gould's research provides all necessary technical details for skilled threat actors to replicate the attack. With Cisco confirming active exploitation and no viable workarounds, unpatched systems face imminent threats.
"There are no workarounds for this vulnerability," Cisco reiterated, emphasizing patching as the only mitigation.
As ISE often sits at the core of network access control systems, compromises could enable credential theft, lateral movement, and persistent backdoors. Organizations must prioritize patching and monitor for anomalous authentication attempts. The public exploit’s release marks a critical inflection point—defenders must outpace attackers now armed with a roadmap to exploitation.
Source: BleepingComputer

Comments
Please log in or register to join the discussion