Gladinet has released emergency updates for CentreStack to address a critical local file inclusion vulnerability (CVE-2025-11371) exploited as a zero-day since September. The flaw bypassed previous mitigations for a remote code execution weakness, enabling full system compromise. Security teams must immediately upgrade to version 16.10.10408.56683.

Enterprise security teams are scrambling to patch a critical vulnerability in Gladinet's CentreStack file-sharing software after researchers uncovered active in-the-wild exploitation. The local file inclusion (LFI) flaw, tracked as CVE-2025-11371, served as a bypass for prior mitigations against a severe remote code execution (RCE) vulnerability (CVE-2025-30406), creating a perfect storm for attackers targeting unpatched systems.
The Vulnerability Chain
According to Huntress researchers, the LFI flaw resided in CentreStack's temp-download handler (/storage/t.dn), which improperly sanitized the s= parameter. This allowed directory traversal attacks enabling unauthorized file reads:
GET /storage/t.dn?s=..\\..\\web.config HTTP/1.1
Host: [target]
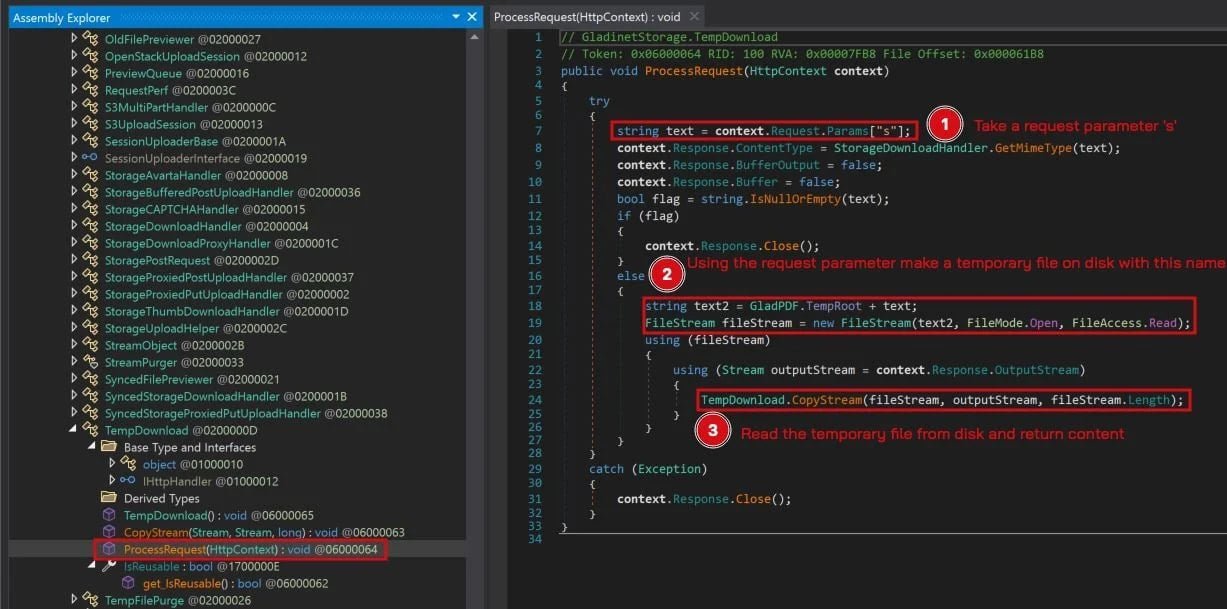 The vulnerable temp-download handler in CentreStack (Source: Huntress)
The vulnerable temp-download handler in CentreStack (Source: Huntress)
Since the service runs as NT AUTHORITY\SYSTEM, attackers could harvest the ASP.NET machine key from Web.config files. This cryptographic key became the linchpin for exploiting the previously patched deserialization flaw (CVE-2025-30406), allowing threat actors to forge malicious ViewState payloads and execute arbitrary commands on fully patched systems.
Exploitation in the Wild
Huntress observed attackers combining these techniques in a clear chain:
- Unauthenticated LFI requests to steal
Web.config - Extraction of machine keys
- Crafting of malicious ViewState payloads
- Remote code execution via deserialization attacks
"The attackers' HTTP requests showed precise sequencing—first harvesting configuration files, then delivering base64-encoded payloads to trigger command execution," Huntress noted in their technical analysis. Their published minimal PoC demonstrates the LFI exploit but deliberately omits the RCE components to prevent weaponization.
Mitigation Imperative
Gladinet's patched version (16.10.10408.56683) addresses the LFI flaw at its root. For organizations unable to immediately update, a temporary mitigation exists:
- Locate the
Web.configfor the UploadDownloadProxy component - Remove the handler definition for the temp-download endpoint
Given CentreStack's role in enterprise file collaboration, unpatched systems represent catastrophic risks. The SYSTEM-level access enables total compromise of Windows environments—a stark reminder that layered vulnerabilities demand defense-in-depth strategies beyond single patches. As file-sharing platforms increasingly bridge internal and external networks, this incident underscores the attack surface expansion that comes with convenience.

Comments
Please log in or register to join the discussion