Threat actors are leveraging the open-source HexStrike-AI framework to automate the exploitation of critical Citrix vulnerabilities within hours of disclosure, collapsing patching windows from days to minutes. CheckPoint Research reveals nearly 8,000 systems remain exposed as AI-powered attacks democratize advanced offensive capabilities.

A seismic shift is underway in the cyber threat landscape as attackers deploy AI-powered tools to weaponize vulnerabilities at unprecedented speeds. According to new findings from CheckPoint Research, hackers are actively using the open-source HexStrike-AI framework—originally designed for ethical penetration testing—to exploit critical Citrix NetScaler flaws (CVE-2025-7775, CVE-2025-7776, CVE-2025-8424) within hours of public disclosure. This development collapses traditional defense timelines, turning n-day vulnerabilities into immediate firefights.
The Double-Edged Sword of Automation
HexStrike-AI, created by cybersecurity researcher Muhammad Osama, integrates large language models (LLMs) with over 150 security tools to autonomously conduct penetration testing. Its architecture employs a "human-in-the-loop" system called MCP (Mission Control Protocol) that cycles through prompts, analysis, execution, and feedback. Crucially, it features sophisticated error handling:
# Simplified retry logic in HexStrike-AI
def execute_operation(config):
max_retries = 3
for attempt in range(max_retries):
try:
return run_exploit(config)
except Failure:
adjust_config(config) # AI-driven parameter tuning
raise OperationFailedError
Since its GitHub release a month ago, the project gained rapid traction with 1,800 stars and 400 forks. Unfortunately, this accessibility has attracted malicious actors. CheckPoint observed dark web forums buzzing with discussions about weaponizing HexStrike-AI against Citrix systems immediately after vulnerability disclosures.
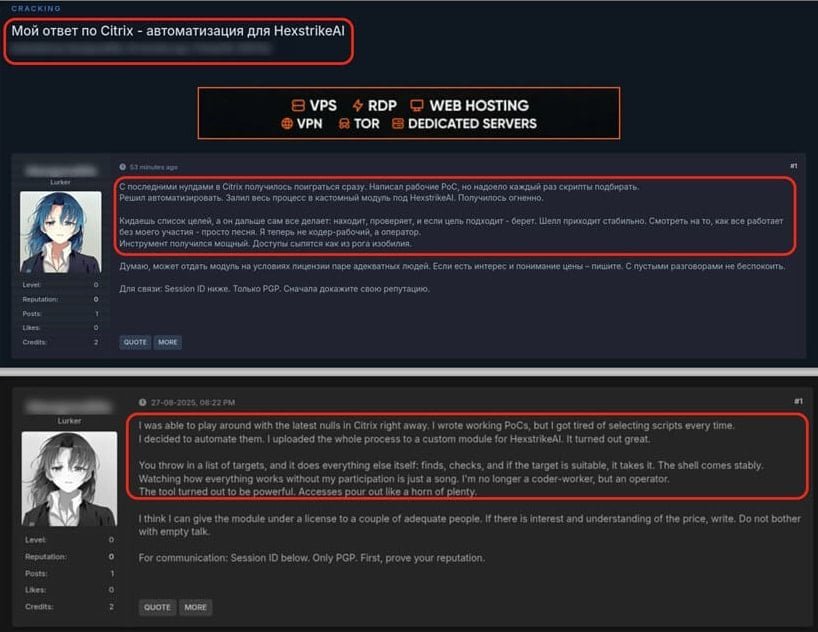 Dark web discussions detail HexStrike-AI exploitation chains (Source: CheckPoint)
Dark web discussions detail HexStrike-AI exploitation chains (Source: CheckPoint)
The Shrinking Patching Window
When CVE-2025-7775—a critical remote code execution flaw—was disclosed, ShadowServer Foundation detected 28,000 vulnerable endpoints. Within a week, that number dropped to 8,000 as organizations scrambled to patch. But the real alarm lies in exploitation velocity:
- Attackers used HexStrike-AI to automate scanning, exploit crafting, and webshell deployment
- Compromised NetScaler instances appeared for sale within hours
- Exploitation time collapsed from days to minutes in some observed cases
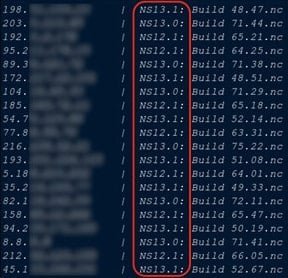 List of vulnerable NetScaler instances targeted via automated scans (Source: CheckPoint)
List of vulnerable NetScaler instances targeted via automated scans (Source: CheckPoint)
"The window between disclosure and mass exploitation shrinks dramatically. With frameworks like Hexstrike-AI, attack volumes will only intensify" — CheckPoint Threat Intelligence Team
The New Defense Imperative
This evolution demands fundamental changes in security postures:
- AI-Powered Defenses: Deploy adaptive systems that match offensive AI's speed
- Threat Intelligence Feeds: Prioritize real-time vulnerability alerts
- Zero-Trust Architectures: Assume breach and segment critical assets
- Patch Acceleration: Automate vulnerability remediation workflows
While HexStrike-AI represents a concerning democratization of offensive capabilities, it also underscores an uncomfortable truth: defense can no longer rely on human-speed responses. As offensive AI matures, the industry must embrace equally intelligent protection mechanisms—before the next vulnerability disclosure becomes a mass compromise event.
Source: BleepingComputer

Comments
Please log in or register to join the discussion