Threat actors are weaponizing iCloud Calendar invites to send convincing phishing emails directly from Apple's email servers, bypassing spam filters by exploiting legitimate infrastructure. The scams impersonate fraudulent PayPal charges to trick victims into calling attacker-controlled support numbers, enabling financial theft and malware deployment.
How Hackers Hijacked Apple's Email Servers for Phishing Attacks

Security researchers have uncovered a sophisticated phishing campaign exploiting iCloud Calendar's invitation system to send malicious emails directly from Apple's infrastructure. This technique allows attackers to bypass critical email security protocols like SPF, DKIM, and DMARC—normally trusted indicators of legitimacy—by weaponizing Apple's own [email protected] domain.
The Anatomy of the Scam
The attack begins with victims receiving emails disguised as PayPal purchase notifications for $599, complete with urgent instructions to call a support number. Unlike traditional phishing, these emails originate from Apple's servers because attackers embed their malicious content within Calendar invite notes. By inviting a Microsoft 365 mailing list they control (e.g., [email protected]), Apple's systems automatically generate and send the phishing email.
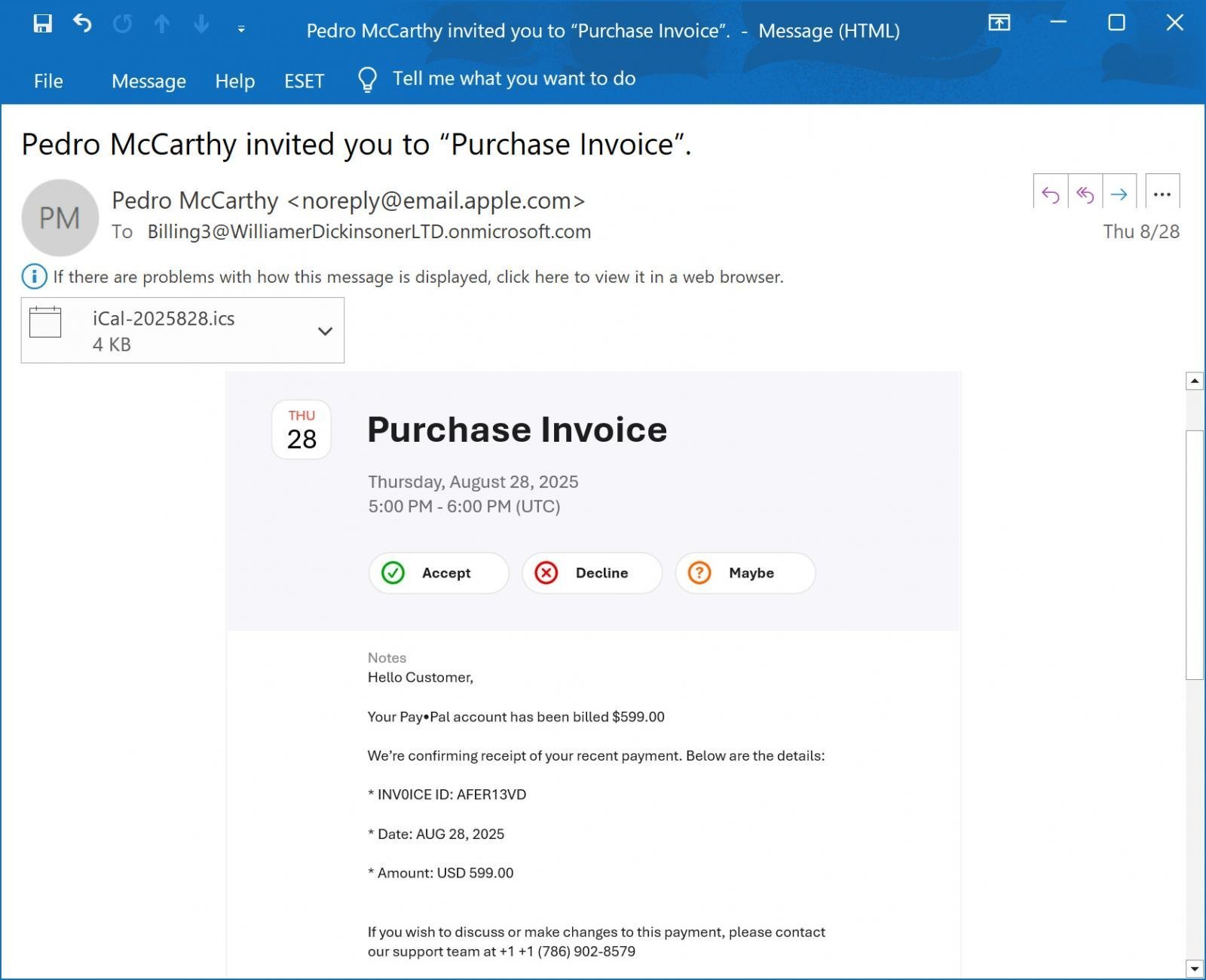 Phishing email disguised as PayPal notification sent via iCloud Calendar invite (Source: BleepingComputer)
Phishing email disguised as PayPal notification sent via iCloud Calendar invite (Source: BleepingComputer)
As cybersecurity expert Lawrence Abrams explains:
"The emails pass all authentication checks because they genuinely originate from Apple. Attackers then leverage Microsoft 365's Sender Rewriting Scheme (SRS) to forward these invites to victims while maintaining email validity—effectively laundering their credibility through two major tech platforms."
Technical analysis of the email headers confirms the exploitation:
Authentication-Results: spf=pass (sender IP is 17.23.6.69)
smtp.mailfrom=email.apple.com; dkim=pass
header.d=email.apple.com;dmarc=pass action=none header.from=email.apple.com;
Why This Bypass Technique Matters
This attack chain represents a significant evolution in phishing tactics for three reasons:
- Trusted Source Exploitation: Emails from
email.apple.cominherently bypass spam filters and recipient skepticism. - Infrastructure Abuse: Attackers manipulate legitimate features rather than deploying malware, making detection harder.
- Scale Potential: Microsoft 365 mailing lists enable mass distribution while maintaining email authentication integrity.
Security teams should treat unexpected calendar invites—especially those containing financial alerts or urgent requests—as high-risk vectors. The FBI's Internet Crime Complaint Center (IC3) notes that callback phishing scams like this have surged by 137% year-over-year, often leading to remote device takeover and six-figure losses.
The Bigger Picture: Securing Ecosystem Weak Links
While Apple and Microsoft aren't directly vulnerable, this incident highlights how interconnected cloud services can create unintended attack surfaces. As platforms add collaboration features, threat actors increasingly exploit trust relationships between systems. Defenders must now monitor not just malicious payloads, but also legitimate services being manipulated for illicit purposes.
Until platform-level mitigations emerge, the best defense remains user education: scrutinize unexpected calendar invites, verify payment alerts through official portals (not embedded contact methods), and assume any unsolicited tech support request is fraudulent. As phishing tactics evolve to exploit trusted infrastructure, vigilance becomes the ultimate firewall.
Source: BleepingComputer

Comments
Please log in or register to join the discussion