A coordinated campaign targeting ultra-valuable country-code domains exploited weak transfer processes, forged identities, and a self-styled registrar to hijack digital assets—including government and single-character domains. Here’s how the scheme unfolded, why it matters for every infrastructure and security team, and what needs to change in the domain ecosystem now.
A Coordinated Attack on the Internet’s Rarest Real Estate
In late 2023, a quiet but sophisticated campaign began circling some of the rarest assets on the internet: premium country code top-level domains (ccTLDs), single-letter names, and high-profile infrastructure domains that almost never change hands.
It looked, at first, like sporadic drama on Twitter and in obscure WeChat groups. A contested short domain here, a questionable brag post there. But as more data surfaced—WHOIS changes, transfer logs, archived pages, registrar records—a pattern emerged.
At the center of that pattern: a single individual, operating under the name "JianFei Wang," allegedly leveraging forged emails, social engineering, and a self-branded registrar to move high-value ccTLD domains out from under their rightful owners.
This story is based on the investigation documented at anti-theft.github.io and corroborating public artifacts. While some of the original material was machine-translated and rough around the edges, the underlying narrative exposes a serious, systemic weakness in how the domain name system (DNS) protects its most sensitive assets.

Act I: Red Flags in the Short Domain World
The earliest visible warning came on September 14, 2023, when developer David (@dvcrn) publicly reported an attempted takeover of his domain d.pn.
The attacker’s details, including the name "JianFei Wang," appeared plainly in the evidence David shared. At the time, it might have looked like an isolated case of domain fraud. It wasn’t.
Days later, "Wang" appeared again—this time in connection with x.st. In a WeChat group, he claimed to have acquired the name. But archived snapshots showed longtime owner Harold (@hrldcpr) as the legitimate holder. Shortly thereafter, the domain’s name server and WHOIS records were flipped to "Wang." Skepticism was immediate: the domain was both rare and strategically valuable, and there was no credible indication it had been legitimately sold. On November 21, 2023, the original owner successfully reclaimed x.st, reinforcing those doubts.
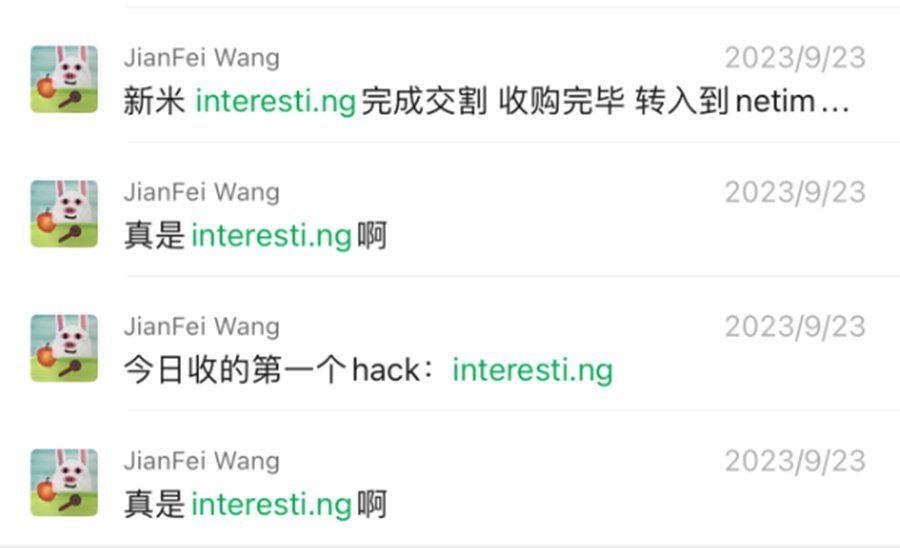
By late September, a cluster of .ng domains—eveni.ng, exciti.ng, interesti.ng, lovi.ng, morni.ng—followed a similar pattern. All were originally owned by investor Mark Kychma; all, at some point, reflected "Wang" in their WHOIS records. These names were eventually recovered, but they revealed something crucial: this wasn’t opportunistic domain flipping. It was systematic probing.
When the same persona repeatedly "acquires" premium, emotionally or strategically significant domains from unrelated owners—then loses them upon scrutiny—you’re not watching market activity. You’re watching operational testing.
Act II: The Bogus Registrar and a Wider Attack Surface
As 2023 progressed, the operation escalated.
- On November 4, 2023, WHOIS data for
f.cdchanged—in apparent violation of.cdrules restricting single-character domains. The name was later relocked by the registry. - In December,
x.kesurfaced under "Wang"’s control. Given its history and market value, its provenance was immediately suspect, though direct proof of theft remains inconclusive.
The real inflection point came in January 2024, when investigators noticed something deeply abnormal: a wave of high-value domains across multiple CoCCA-operated registries simultaneously entered pendingTransfer status.
Among them:
gov.cx— associated with the government of Christmas Island- Single-character
.hn,.sb,.cx, and.gsdomains - Notable names like
technolo.gyandener.gy
Different owners. Different contexts. Same registries. Same suspicious timing.
This was not coincidence. It was choreography.
Instead of immediately alerting CoCCA, the investigators waited to see where the domains would land. The pattern quickly crystallized:
4.gswas transferred to a registrar calling itself "InterCat Ltd" and then rapidly moved again to West263, with ownership records aligned to "Wang".f.sbandk.hnalso successfully transferred to "InterCat Ltd".
And "InterCat Ltd"?
- Its site listed "Wang"’s contact info.
- It displayed an ICANN logo despite having no ICANN accreditation.
- Its role in the transfer path aligned precisely with the suspicious activity.
This was the infrastructure play: if you can’t just socially engineer a registrar, become one—at least on paper. Then:
- Forge authorization emails "from" the legitimate owner.
- Involve addresses like
[email protected]and[email protected]in the cc/reply chain. - Get the domain moved into an account you control.
- Obtain auth codes and initiate cross-registrar transfers.
- List undervalued assets for fast liquidation.
The anti-theft team’s reconstruction of a k.hn transfer shows exactly this pattern. The registrar treated a forged request as genuine; the owner, busy with work, missed the window to object; the transfer was approved.
By the time the victim realized what had happened, "Wang" had already begun offering the names for sale on fora like dalao.net and platforms including Dan.com—at prices well below market, behavior consistent with laundering stolen inventory rather than long-term investing.

Act III: CoCCA Intervenes—and the Evidence Mounts
Once the scale became undeniable, the investigators moved.
They contacted:
- CoCCA, which operates registry platforms for several of the affected ccTLDs.
- Ben Dowling, owner of
ho.stand founder of IPinfo, after detecting suspicious WHOIS changes involving[email protected].
CoCCA responded quickly:
- They blocked pending transfers on many of the targeted domains.
- They flagged and locked domains already transferred under suspicious circumstances with statuses like
Registry Hold - Suspicious Activity. - They shared lists of anomalous transfers that closely matched the independent findings.
For domains already moved, CoCCA asked the investigators to help contact original registrants so that formal complaints could trigger registry action.
Meanwhile, archival evidence showed "InterCat Ltd" and "Wang"’s own accounts publicly boasting on Twitter (now X) about the domains they "acquired"—tweets later scrubbed but preserved in captures.
When confronted, "Wang" reportedly attempted to deflect responsibility, claiming the actions were carried out by a "hacker friend." But:
- The registrar application.
- The reused contact details.
- The sale listings.
- The consistent appearance of his identifiers in WHOIS records and transfer trails.
Together form a pattern that’s difficult to dismiss as third-party framing.
This is not a court verdict. But in the realm of operational security, these signals would trigger every incident-response playbook you have.
{{IMAGE:4}}
Why This Matters to Developers and Infrastructure Teams
If you run infrastructure, this story should feel uncomfortably familiar. It’s supply chain compromise—just at the DNS layer.
Key insights for technical leaders:
Systemic Weak Links in ccTLD Operations
- Many ccTLDs still rely on:
- Email-based transfer approvals.
- Inconsistent identity verification.
- Weak or optional security controls like EPP locks and registry locks.
- CoCCA’s fast and responsible response here is commendable—but it also highlights that some registrars and processes were lenient enough to be gamed by forged emails.
- Many ccTLDs still rely on:
Ultra-Short Domains Are High-Value Attack Surfaces
- Single-letter and ultra-short ccTLD domains are:
- Brand-critical.
- Trust anchors for redirects, APIs, telemetry, and internal tooling.
- They are disproportionately targeted because they’re rare, visible, and liquid. Treat them as production infrastructure, not collectibles.
- Single-letter and ultra-short ccTLD domains are:
Fake Trust Signals Are Getting Cheaper
- Spinning up a convincing "registrar" façade (complete with lifted ICANN logos) is trivial.
- For many registry operators or smaller providers, the existence of a seemingly formal entity may short-circuit deeper due diligence.
- The same pattern generalizes to code-signing CAs, package registries, OAuth apps, and SaaS vendors.
Notification Gaps Are an Exploitation Vector
- In multiple cases, owners missed a narrow window to dispute fraudulent transfers.
- If your most critical domains rely on one person casually checking an overloaded inbox, you’ve already outsourced your perimeter to chance.
{{IMAGE:5}}
Securing Your Own Namespace: Practical Steps
For teams running production systems, especially on exotic or high-value TLDs, this incident is a checklist, not a curiosity.
Recommended controls:
Registrar and Registry Locks
- Enable clientTransferProhibited / serverTransferProhibited wherever possible.
- For flagship domains, request a registry lock (where the registry itself must manually approve changes via out-of-band procedures).
Hardened Contact and Email Hygiene
- Use dedicated, access-controlled email addresses for domain administration.
- Enforce MFA and SSO for registrar logins.
- Monitor for changes to registrant email or name server records with automated alerts.
Policy and Playbooks
- Treat domain integrity as part of your incident response and business continuity planning.
- Maintain an internal inventory of "crown jewel" domains and apply stricter policies than for ordinary names.
Due Diligence on Registrars
- Verify that your registrars are accredited (ICANN or relevant ccTLD authority).
- Be wary of niche or unknown entities claiming registrar status without verifiable accreditation.
Monitor for Market Anomalies
- If one of your domains (or a confusingly similar one) suddenly appears in marketplaces at suspiciously low prices, treat it as a potential compromise indicator.
This is also a prompt for registries and registrars:
- Normalize multi-factor and out-of-band verification for high-value transfers.
- Detect and rate-limit abnormal batched transfer requests.
- Improve transparency around registrar accreditation and enforcement against fraudulent branding.
A Fragile Trust Layer—and a Choice
The DNS is often described as the "phone book" of the internet, but that undersells its role. For many organizations, the right domain isn’t just an address; it’s an authentication primitive. People trust gov.cx to be a government, ho.st to be infrastructure, x.st or ultra-short ccTLDs to be stable landmarks.
This incident shows how easily that trust can be bent when outdated assumptions—"email is enough," "logos equal legitimacy," "nobody would target my tiny ccTLD"—collide with determined, methodical abuse.
The good news is that here, a small community of vigilant operators, registries, and investigators noticed early, preserved evidence, and intervened before the damage became irreversible.
The bad news: nothing about the attack path is unique.
If you own critical domains, assume someone will eventually try a version of this against you. The difference between "attempted" and "successful" will come down to the rigor of your controls, the responsiveness of your partners, and whether you treat domain security as a first-class part of your infrastructure—not an afterthought at renewal time.
For now, the message from this campaign is clear: the online world is not beyond the law, but neither is it automatically safe. We have the tools to protect our namespaces. The question is whether we choose to use them before the next "InterCat" shows up.
Source: Primary narrative, timeline, and artifacts adapted and verified from https://anti-theft.github.io/

Comments
Please log in or register to join the discussion