A sophisticated new Linux malware dubbed Koske leverages seemingly innocent panda JPEGs to deploy cryptominers directly into memory, bypassing traditional defenses. Researchers suspect AI involvement due to its adaptive behavior, highlighting evolving threats to cloud and open-source infrastructure.
Stealthy Linux Malware Koske Turns Cute Pandas into Cryptojacking Weapons
In a startling blend of deception and technical ingenuity, cybersecurity researchers at AquaSec have uncovered Koske—a new Linux malware that disguises malicious payloads within JPEG images of panda bears. As reported by BleepingComputer, this threat exploits polyglot files to execute attacks directly in memory, evading detection while hijacking systems for large-scale cryptocurrency mining. The malware's adaptive tactics suggest potential AI-assisted development, signaling a dangerous evolution in cyber threats.

The Polyglot Deception: When Images Become Code
Koske gains initial access by targeting misconfigured JupyterLab instances exposed online, allowing attackers to execute remote commands. Once inside, it downloads two panda-themed JPEGs from legitimate image-hosting services like OVH. Crucially, these aren't typical steganography attacks. Instead, Koske uses polyglot files—data interpreted differently depending on the processing application. To the human eye, they appear as harmless pandas. To a script interpreter, they execute embedded shell code.
"The same file can be interpreted as both an image and a script," AquaSec researchers noted. "A user sees a panda, but the system runs malicious code appended to the file."
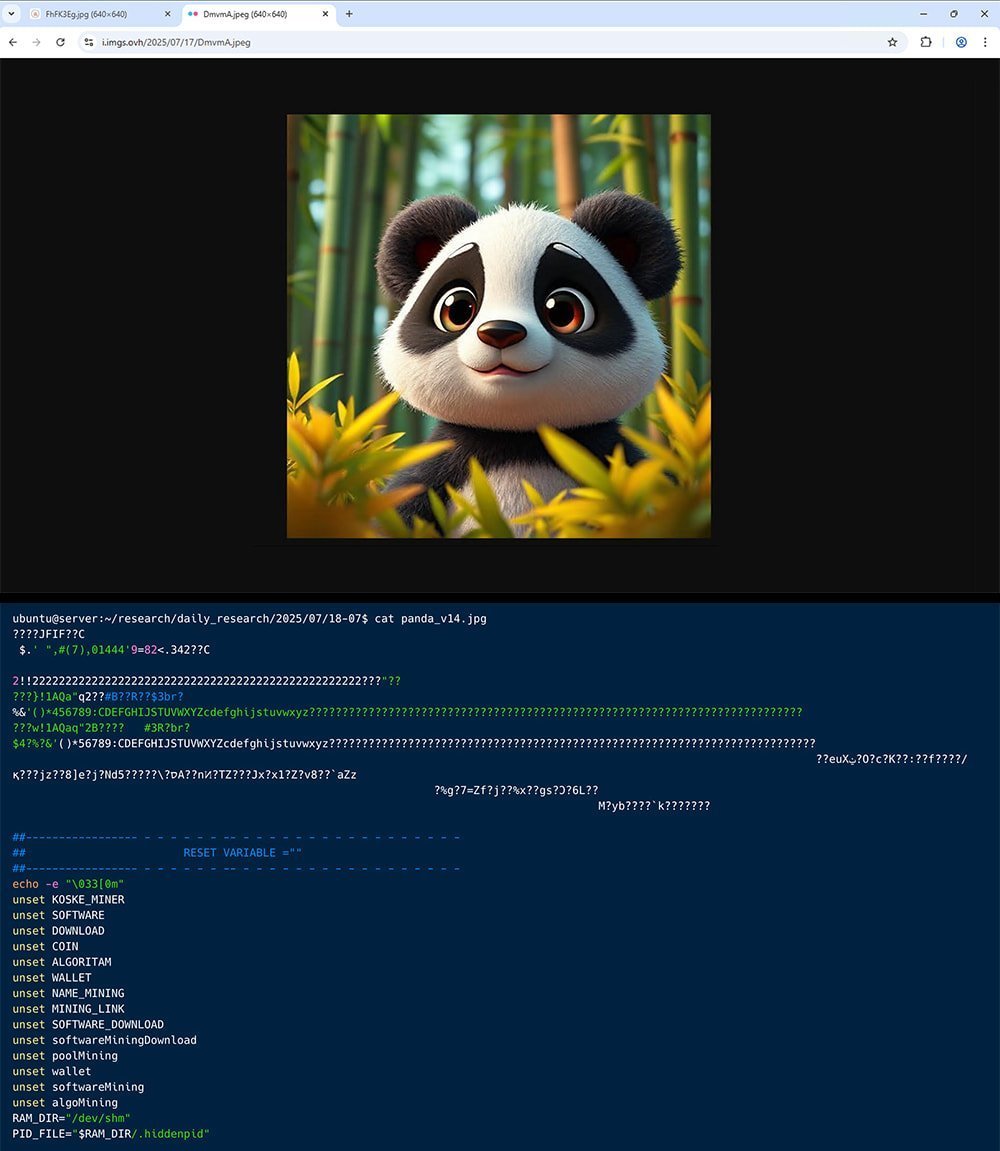 Seemingly innocuous panda image (top) and its malicious file contents (bottom). Source: AquaSec
Seemingly innocuous panda image (top) and its malicious file contents (bottom). Source: AquaSec
The dual payloads activate in parallel. One is a shell script executed in memory using native Linux utilities like bash -c, which establishes persistence via cron jobs (running every 30 minutes) and custom systemd services. It also hardens the network:
chattr +i /etc/resolv.conf # Locks DNS configuration
iptables -F # Flushes firewall rules
export http_proxy="" # Resets proxy variables
Simultaneously, a C-based rootkit compiles in memory and uses LD_PRELOAD to hijack the readdir() function, hiding processes and files related to Koske from monitoring tools. This includes filtering entries containing strings like "koske" or "hideproc."
Cryptojacking with AI-Driven Adaptability
After securing persistence, Koske downloads CPU and GPU-optimized miners from GitHub repositories, supporting 18 cryptocurrencies including Monero and Ravencoin. The malware evaluates host hardware to select the most efficient miner and automatically switches to backup pools if one fails—a trait AquaSec links to potential LLM or automation framework involvement.
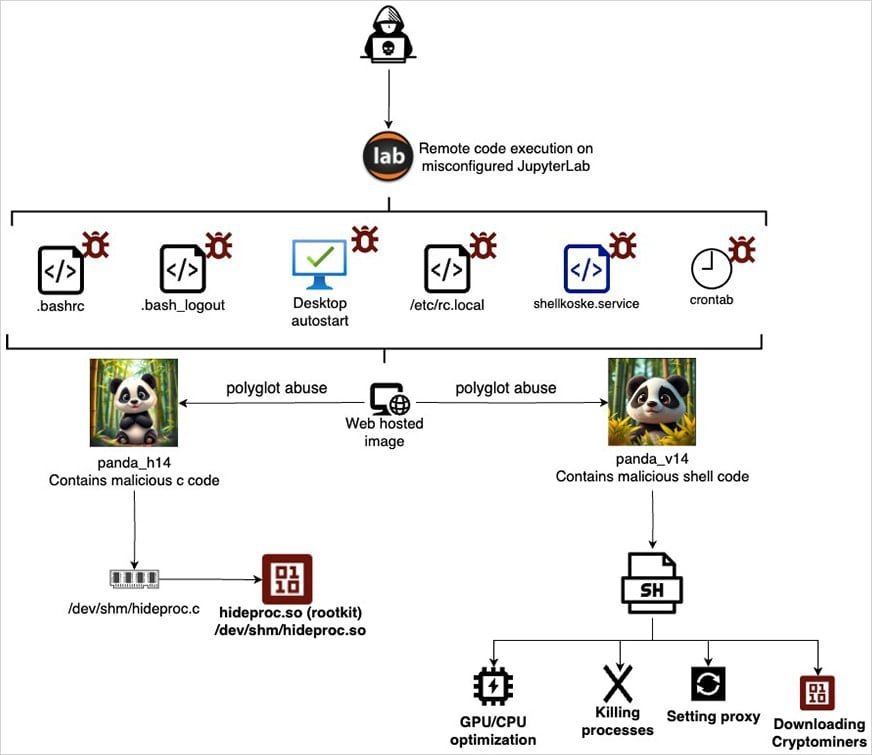 Koske's complete attack chain. Source: AquaSec
Koske's complete attack chain. Source: AquaSec
This adaptability extends to network evasion, where Koske brute-forces proxies using tools like curl and wget to maintain stealth. While infrastructure traces point to Serbian and Slovak origins, attribution remains unconfirmed. The malware's ability to self-optimize underscores concerns about AI lowering barriers for sophisticated attacks.
Implications: A New Era of Memory-Resident Threats
Koske exemplifies how polyglot files and memory-only execution can bypass conventional security scans, posing severe risks to cloud environments and Linux servers. Its cryptojacking focus drains resources and inflates costs, but future variants could incorporate ransomware or data exfiltration. As AquaSec warns, real-time AI enhancements might soon make such threats dynamically evolve during attacks. For developers and sysadmins, this underscores the urgency of securing exposed services like JupyterLab and adopting runtime protection that monitors memory anomalies. Vigilance against "benign" files is now as critical as ever—because today's cute panda could be tomorrow's system hijacker.
Source: BleepingComputer

Comments
Please log in or register to join the discussion