Logitech has confirmed a significant data breach following an attack by the notorious Clop extortion gang, which exploited a zero-day vulnerability in Oracle's E-Business Suite to steal nearly 1.8 TB of sensitive company data. While the breach did not disrupt operations, it highlights the persistent threat of supply chain attacks targeting enterprise software. This incident underscores the urgent need for robust third-party risk management in an era of escalating ransomware tactics.
Logitech's Data Breach: Clop Gang Exploits Oracle Zero-Day in Latest Supply Chain Assault
In a stark reminder of the vulnerabilities lurking in enterprise software ecosystems, Logitech International S.A., the Swiss multinational renowned for its computer peripherals and smart home devices, has confirmed a cyberattack that resulted in the theft of substantial corporate data. The breach, disclosed today via a Form 8-K filing with the U.S. Securities and Exchange Commission, was carried out by the Clop extortion gang, a group with a notorious track record of exploiting zero-day flaws to siphon data from high-profile targets.

The incident, which occurred through a third-party zero-day vulnerability, did not compromise Logitech's products, manufacturing, or day-to-day operations—a small mercy in an otherwise alarming development. However, the attackers managed to exfiltrate nearly 1.8 terabytes of data, including limited information on employees, consumers, customers, and suppliers. Crucially, Logitech emphasized that no highly sensitive details like national ID numbers or credit card information were stored in the affected systems, mitigating some immediate risks to individuals.
The Culprit: Clop's Relentless Campaign Against Oracle E-Business Suite
Logitech's disclosure comes on the heels of the Clop gang adding the company to its data-leak extortion site last week, a tactic designed to pressure victims into paying ransoms to prevent public leaks. While Logitech did not explicitly name the software vendor, cybersecurity experts and reports point to a zero-day flaw in Oracle's E-Business Suite (EBS), tracked as CVE-2025-61882, as the likely entry point. This vulnerability was part of a broader extortion campaign that began in July 2025, targeting numerous organizations using Oracle's widely adopted ERP system.
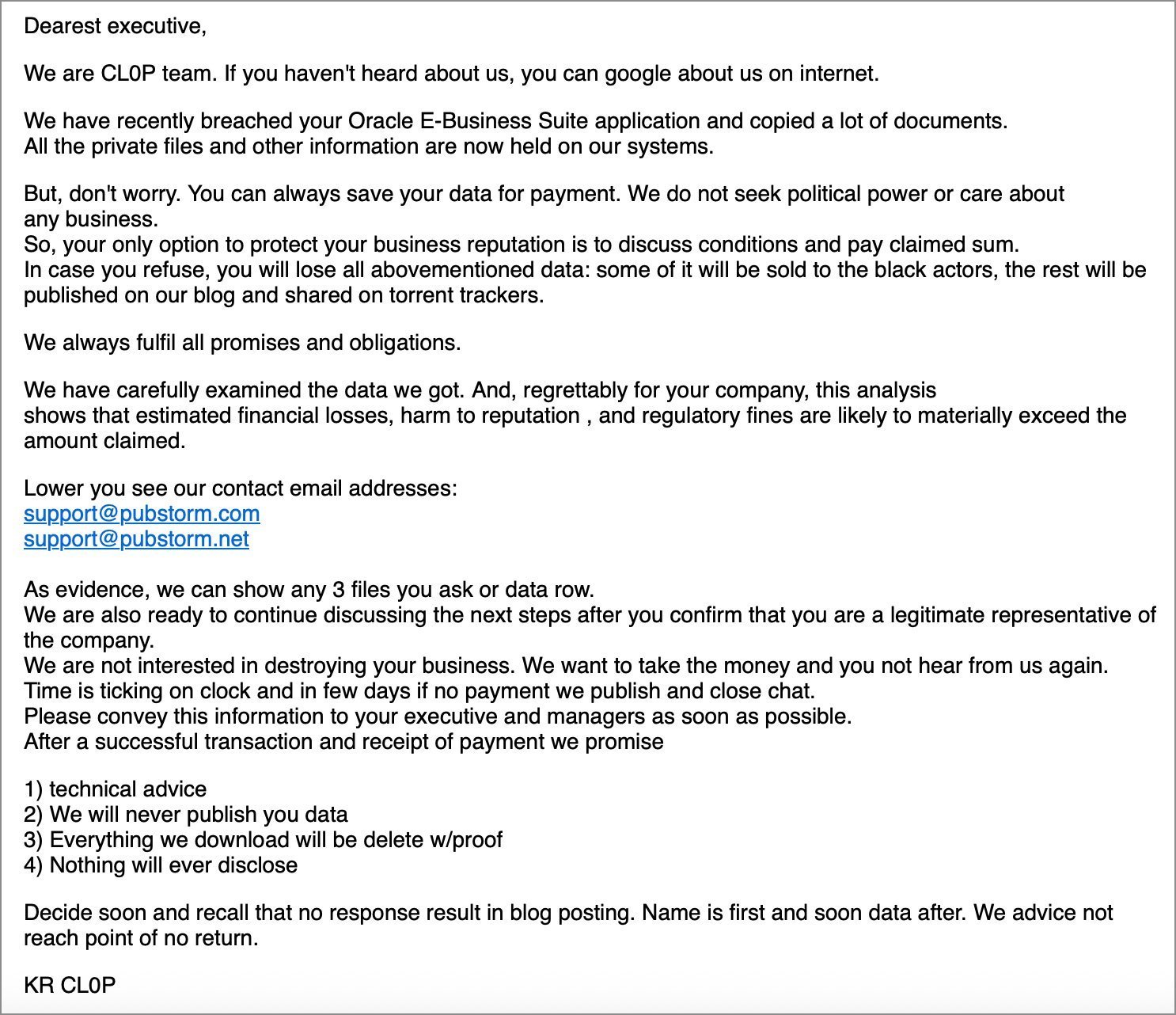
Oracle confirmed the zero-day and issued an emergency patch shortly after Mandiant and Google began tracking the attacks. The campaign involved phishing-like extortion emails warning victims of impending data leaks unless ransoms were paid. For developers and IT leaders relying on Oracle EBS, this breach exemplifies the dangers of unpatched third-party dependencies—flaws that, once discovered, can be weaponized at scale before fixes are universally applied.
Clop's history of such exploits is alarming. From the 2020 Accellion FTA attacks affecting nearly 100 organizations, to the massive 2023 MOVEit Transfer campaign that breached 2,773 entities worldwide, the gang has consistently targeted file transfer and enterprise management tools. Their 2024 strikes on Cleo file transfer software and now Oracle EBS demonstrate a pattern: zero-days in supply chain-critical software are low-hanging fruit for data extortion, often bypassing traditional defenses like firewalls or endpoint protection.
Implications for the Tech Industry: Beyond Logitech's Walls
This breach isn't isolated; it's part of a wave hitting major players. Other victims of the Oracle EBS attacks include Harvard University, Envoy Air (an American Airlines subsidiary), The Washington Post, and GlobalLogic, where up to 10,000 employees were notified of potential data exposure. For tech leaders, the fallout extends beyond immediate data loss. Supply chain attacks like this erode trust in third-party vendors, forcing organizations to rethink procurement, patching, and monitoring strategies.
From a technical standpoint, the exploit likely involved unauthorized access to EBS modules handling HR, finance, or supplier data—common repositories in ERP systems. Developers integrating with such platforms must now prioritize zero-trust architectures and continuous vulnerability scanning. As Clop's tactics evolve, so must defenses: automated patch management, behavioral anomaly detection in network traffic, and segmented access controls could have limited the blast radius here.
Logitech's swift response—engaging leading external cybersecurity firms and patching the vulnerability—offers a blueprint for resilience. Yet, the incident serves as a wake-up call. In an interconnected digital landscape, where enterprise software underpins global operations, the cost of a single zero-day isn't just measured in terabytes stolen, but in the long shadow it casts over innovation and security. As Clop continues its rampage, the tech community must collaborate more fiercely on threat intelligence sharing to outpace these digital extortionists.

Comments
Please log in or register to join the discussion