Global fashion giant MANGO has disclosed a data breach originating from a third-party marketing vendor, exposing customer names, contact details, and location data. While financial information remained secure, the incident highlights escalating supply chain risks and new phishing threats for 2025.

Spanish fashion powerhouse MANGO has confirmed a significant data breach impacting customers worldwide, tracing the compromise to an unnamed external marketing services provider. The incident exposes critical vulnerabilities in third-party vendor relationships that continue to plague enterprises despite heightened security investments.
The Anatomy of the Breach
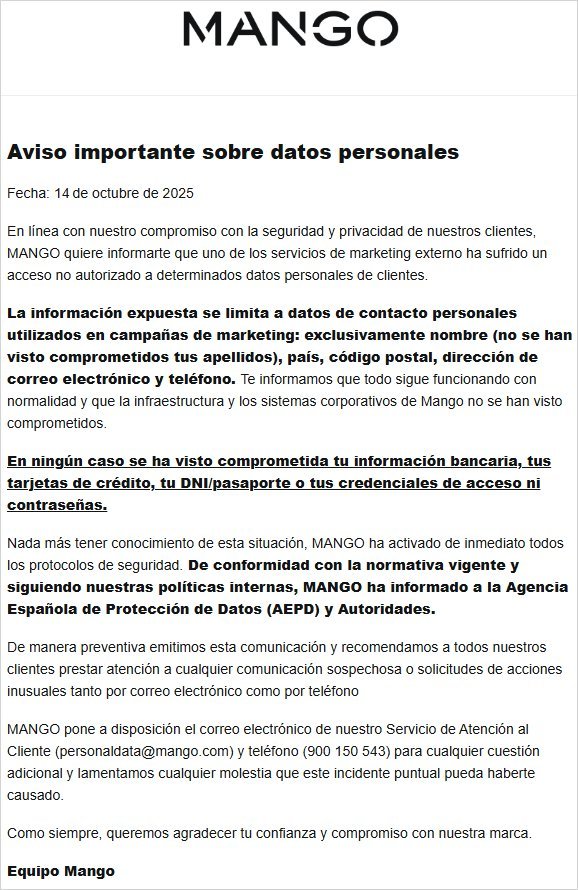
According to breach notifications sent to customers on October 14, 2025, attackers accessed:
- First names
- Email addresses
- Telephone numbers
- Countries of residence
- Postal codes
Crucially, MANGO confirmed no financial data, passwords, or government IDs were compromised, and its internal corporate systems remained untouched. The company emphasized that business operations continue normally, indicating the attack was isolated to the marketing vendor's infrastructure.
"MANGO wishes to inform you that one of the external marketing services has suffered unauthorized access to certain customers' personal data," stated the official customer notice.
Hidden Risks in Limited Data Exposures
While lacking traditional high-value targets like credit card numbers, cybersecurity experts warn the exposed dataset creates potent attack vectors:
- Hyper-targeted phishing: Combining first names, locations, and contact details enables convincingly personalized scam campaigns
- Identity correlation: Attackers can cross-reference this data with other breaches to build comprehensive profiles
- Geo-specific social engineering: Postal codes enable location-based impersonation tactics
Enterprise Third-Party Risk Management Failures
This incident underscores persistent gaps in vendor security oversight:
- Shadow access: Marketing vendors often retain excessive customer data with minimal security scrutiny
- Detection delays: MANGO activated protocols only after the vendor's compromise was discovered
- Accountability opacity: The unnamed vendor’s security practices remain unexamined publicly
MANGO has notified Spain's Data Protection Agency (AEPD) and established dedicated response channels:
- Email: [email protected]
- Hotline: 900 150 543
 Notice sent to MANGO customers about the data breach
Notice sent to MANGO customers about the data breach
The Silent Attacker Enigma
Notably absent is any claim of responsibility by ransomware groups or extortion sites—unusual for breaches of this scale. This suggests either:
- A financially motivated actor quietly selling data on dark web markets
- State-sponsored espionage targeting consumer behavior patterns
- An immature attacker who hasn't yet monetized the breach
As supply chain attacks increase in sophistication, this breach serves as a stark reminder that your security perimeter extends to every vendor touching customer data. For technical leaders, it reinforces the urgency of:
- Implementing zero-trust architectures for third-party access
- Conducting continuous security validation of vendors
- Developing breach playbooks that assume when—not if—partners will be compromised
The true cost for MANGO won't be regulatory fines alone, but eroded consumer trust in an industry where data privacy increasingly influences purchasing decisions.

Comments
Please log in or register to join the discussion