A dangerous new toolkit called MatrixPDF enables threat actors to transform benign PDF documents into interactive phishing and malware lures capable of bypassing major email security filters like Gmail. Researchers warn its JavaScript-driven overlays and encrypted metadata create convincing traps that trick users into visiting malicious sites, marking a significant evolution in document-based attacks.
Security researchers at Varonis have uncovered MatrixPDF, a sophisticated cybercrime toolkit sold on underground forums and Telegram, designed to weaponize ordinary PDF files. Marketed ambiguously as a "phishing simulation tool," its primary function is enabling attackers to craft highly deceptive documents that evade detection and manipulate victims into compromising their systems.
How MatrixPDF Operates
Attackers upload a legitimate PDF into the MatrixPDF builder, then layer malicious elements on top:
- Blurred Content & Fake Security Overlays: Creates the illusion of a protected document, prompting users to click an "Open Secure Document" button.
- Embedded JavaScript Actions: Triggers when the document opens or when buttons are clicked. This JavaScript can force redirection to external phishing pages or malware download sites.
- Metadata Encryption: Helps obfuscate the file's malicious intent from scanners.
- Secure Redirect Mechanism: The core bypass technique.
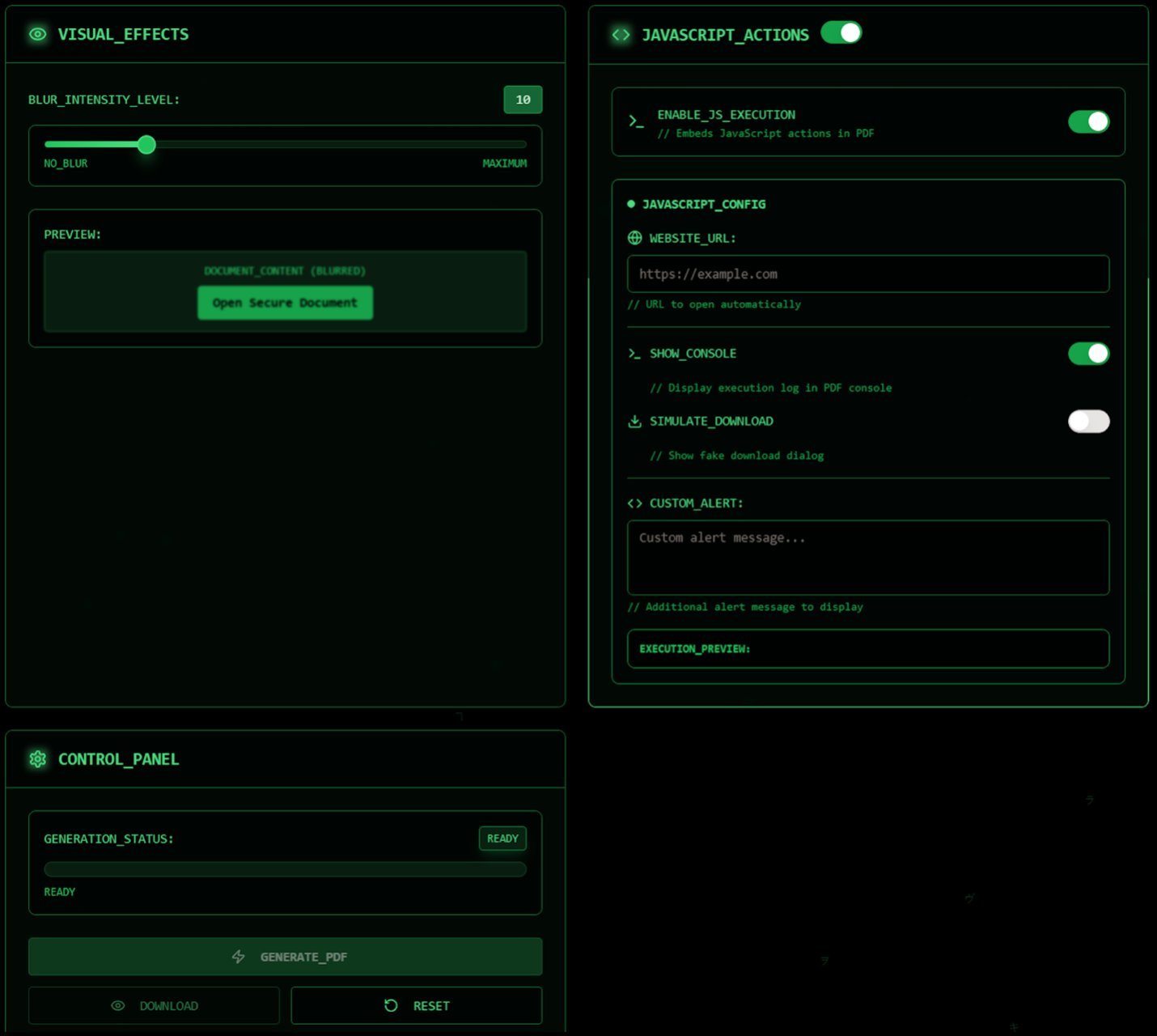 MatrixPDF's builder interface, showing options for adding malicious overlays and actions. (Source: Varonis)
MatrixPDF's builder interface, showing options for adding malicious overlays and actions. (Source: Varonis)
Evading Email Security (Especially Gmail)
MatrixPDF's effectiveness stems from its ability to bypass common email security measures:
- No Embedded Malware: The PDF itself contains no malicious binaries, passing static scans.
- User-Initiated Action: Malicious content is only fetched after the victim clicks a button within the PDF displayed in their email client (like Gmail).
- Gmail Viewer Limitation: While Gmail's built-in PDF viewer doesn't execute JavaScript, it does render clickable links/buttons. The victim's click appears as a legitimate user-initiated web request, not a blocked automatic redirect.
"Gmail's PDF viewer does not execute PDF JavaScript but allows clickable links/annotations," Varonis researcher Daniel Kelley explained to BleepingComputer. "This somewhat clever design works around Gmail's security."
While attempts to auto-open malicious sites on document load are often flagged by modern PDF viewers with warnings, the social engineering lure of the "Secure Document" button significantly increases the likelihood of user interaction.
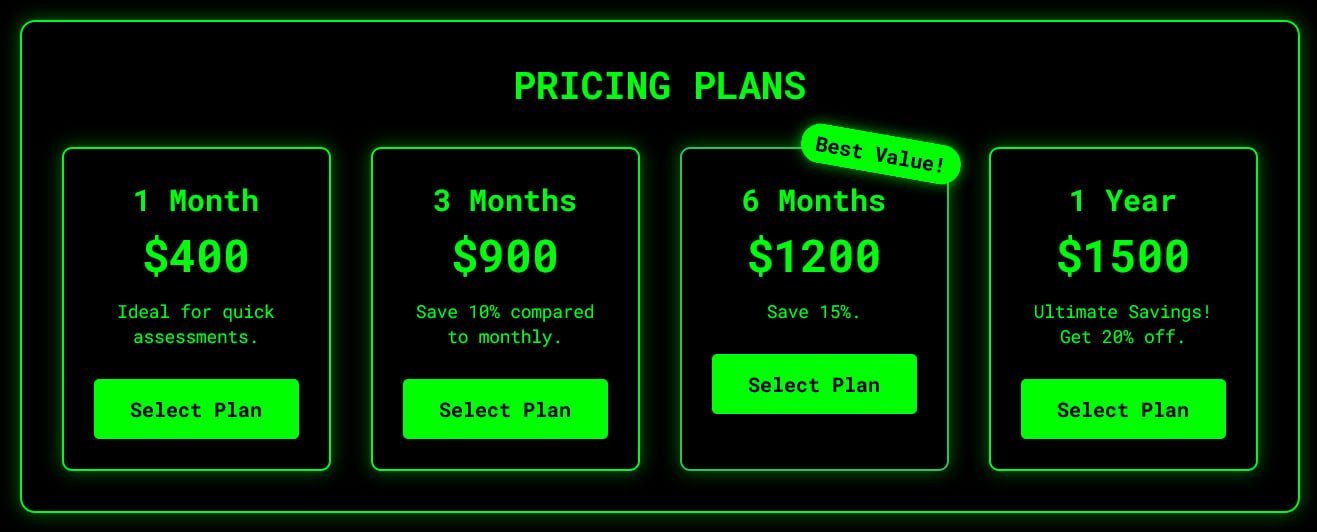 MatrixPDF subscription pricing, ranging from $400/month to $1500/year, reflecting its perceived value in the cybercrime ecosystem. (Source: Varonis)
MatrixPDF subscription pricing, ranging from $400/month to $1500/year, reflecting its perceived value in the cybercrime ecosystem. (Source: Varonis)
Why PDFs Remain a Prime Attack Vector
PDFs are the perfect vehicle for these attacks:
- Ubiquity: They are universally used and trusted for business communication.
- Rendering in Email: Most email clients display PDFs directly, reducing user hesitation.
- Complexity: Their structure allows for embedding scripts, forms, and layered content that can hide malicious intent.
Mitigating the MatrixPDF Threat
Varonis emphasizes that defending against these advanced PDF phishing lures requires moving beyond basic signature-based detection:
- AI-Driven Email Security: Solutions that analyze PDF structure for anomalies (like unexpected overlays, hidden buttons, or obfuscated JavaScript) are crucial.
- Content Detonation: Sandboxing PDFs to safely execute and observe their behavior, particularly monitoring for outbound connection attempts triggered by user interactions simulated within the sandbox.
- User Awareness: Reinforcing training about the risks of interacting with unexpected documents, especially those prompting urgent action to view "secure" content.
The Escalating Arms Race in Document-Based Attacks
The emergence of MatrixPDF, sold as a service to lower-skilled criminals, signifies a worrying trend. Attackers are investing heavily in tools that exploit the inherent trust and functionality of common document formats like PDFs. Defenders must prioritize advanced analysis capable of understanding the behavior and deceptive design within these files, not just their static content. As phishing toolkits become more sophisticated and accessible, the line between a harmless document and a devastating attack vector grows increasingly blurred.
Comments
Please log in or register to join the discussion