Cloud environments generate an overwhelming volume and complexity of security alerts far surpassing traditional on-prem systems, creating unique challenges in prioritization, context, and response. This article explores the distinct nature of cloud alerts and outlines proven strategies, including centralized monitoring, AI-powered triage, and automated remediation, essential for modern security teams drowning in noise. Mastering these techniques is critical for transforming alert chaos into acti
Security operations centers (SOCs) are drowning. The shift to dynamic, multi-cloud environments hasn't just changed infrastructure; it's fundamentally altered the very nature of security alerts, creating a tidal wave of data that traditional on-prem processes are ill-equipped to handle. Unlike their static predecessors, cloud security alerts are generated at an unprecedented scale, lack crucial context, and demand rapid response within ephemeral architectures. Understanding these differences isn't academic – it's a survival imperative for modern security teams.
The Cloud's Unique Alarm System: Volume, Velocity, and Vanishing Context
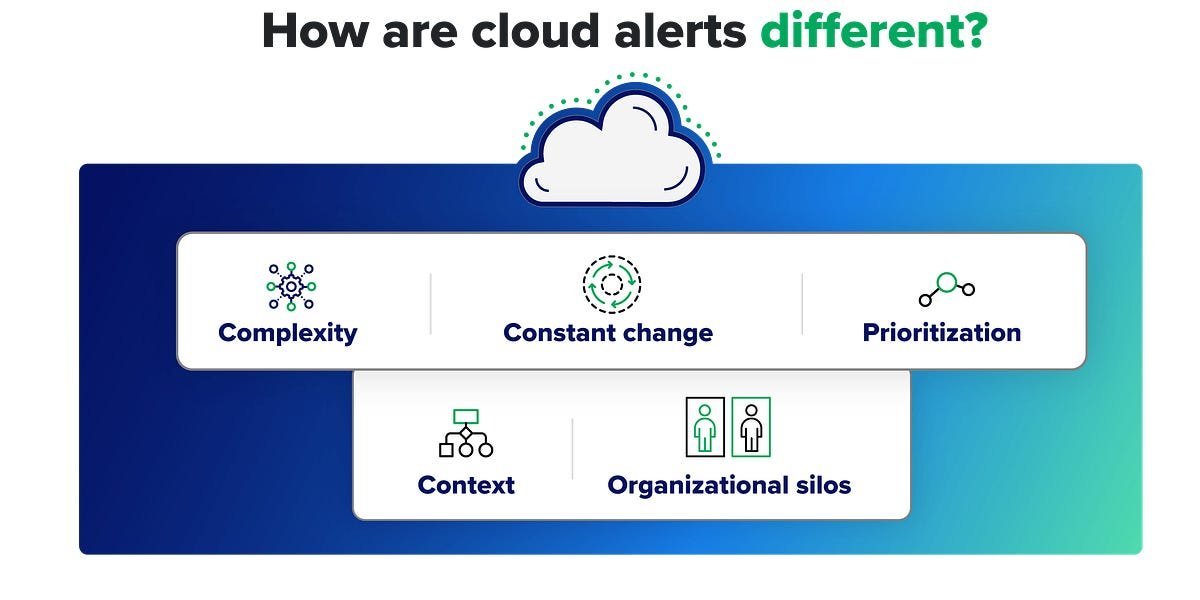
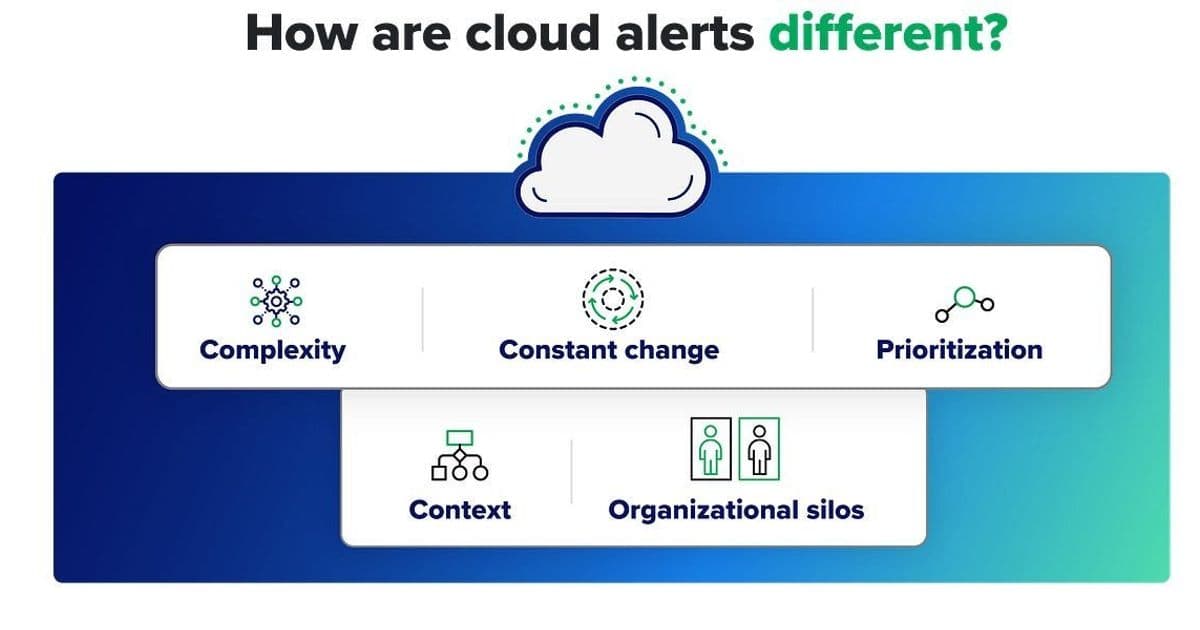
Cloud security alerts signal potential threats, vulnerabilities, and suspicious activities, much like on-prem alerts. However, the cloud's inherent characteristics amplify the challenge exponentially:
- Exponential Volume & False Positives: Constant change, automation, and ephemeral resources generate orders of magnitude more alerts. Service accounts (non-human identities) alone create a relentless stream of IAM events. Distinguishing signal from noise becomes a Herculean task.
- Blind Spots from Complexity: Resources sprawled across regions, services, and multiple cloud providers (AWS, Azure, GCP, OCI) shatter visibility. Correlating seemingly isolated alerts – like an API spike in AWS US-East, failed Azure logins in Europe, and suspicious GCP traffic in Asia – becomes near impossible without unified context, potentially masking coordinated attacks.
- The Context Vacuum: An alert is merely a starting pistol. Critical questions remain unanswered: Is this a true threat? What resource is affected? How critical is it? What's the blast radius? What should we do? Missing user, device, and behavioral context cripples prioritization and investigation.
- Organizational Friction: Security teams often spot the problem but lack the permissions to fix cloud misconfigurations or compromised resources. Remediation requires navigating silos, convincing engineering teams, and creating dangerous delays.
"Prioritization without context becomes guesswork," the analysis notes. "Facing deluges of alerts, teams make decisions based on gut instinct rather than insight, inevitably leading to mistakes."
Beyond the Flood: Strategies for Effective Cloud Alert Management
Surviving the cloud alert storm requires rethinking processes and embracing automation. Here are key best practices:
- Centralize Monitoring & Normalization: Aggregating logs and alerts from all cloud environments (IaaS, PaaS, SaaS, Kubernetes) into a single pane of glass is non-negotiable. This provides the holistic view needed to spot cross-platform attack patterns and streamline analyst workflows. Example: Expel MDR ingests and normalizes security data via APIs, enabling faster correlation and response.
- Implement Intelligent Triage with AI & Automation: Manual sifting is unsustainable. Leverage automation to filter millions of daily alerts, ruthlessly eliminating false positives. Augment this with AI and threat intelligence to surface only the critical alerts requiring human expertise, considering user behavior, device context, and historical incidents.
- Enrich Alerts Relentlessly: Transform bare alerts into actionable intelligence. Integrate:
- Asset criticality and relationships (What's affected? What's connected?)
- IAM context (Is this user behavior anomalous?)
- Threat intelligence (Known IOCs, TTPs, attacker motives)
- Historical similarity (Have we seen this pattern before?)
- Concrete remediation guidance
- Automate Remediation Where Possible: Not every alert needs a human. Automate responses for common, well-understood threats like revoking access for suspicious API activity, fixing misconfigured firewall rules, or quarantining instances involved in data exfiltration. Implement approval workflows where needed.
- Continuously Tune Detection Rules: Cloud environments and threats evolve incessantly. Detection rules are snapshots in time. Regularly:
- Adjust thresholds based on new activity baselines
- Add exceptions for legitimate processes
- Refine query logic
- Update risk scores
- Incorporate learnings from incidents and penetration tests
- Bridge the Sec-Dev Divide: Break down silos proactively. Foster collaboration before incidents through shared responsibility models, clear escalation paths, and post-incident reviews involving both security and engineering. Embed security earlier in the cloud development lifecycle (IaC, PaC).
- Leverage Alerts for Proactive Posture Improvement: Use alert trends strategically. Identify recurring misconfiguration sources (tweak IaC templates!), pinpoint overly permissive IAM roles (enforce least privilege!), and define secure cloud landing zones to prevent future issues. Turn reactive firefighting into proactive hardening.
The Imperative Shift: From Reactive Noise to Proactive Defense
Cloud security alerts represent a paradigm shift. Their volume, complexity, and context deficit render traditional SOC playbooks obsolete. Success hinges on embracing automation for scale, leveraging AI for intelligent filtering and enrichment, and fostering cross-team collaboration to overcome organizational friction. Centralized visibility provides the essential foundation, while continuous tuning ensures detection efficacy keeps pace with the dynamic cloud landscape. Mastering cloud alert management transforms a cacophony of warnings into a symphony of actionable intelligence, enabling security teams to move from overwhelmed to empowered.
Source: Analysis and strategies adapted from "Thoughts on cloud alerts from the top cloud MDR" originally published on Expel's blog and Grounded Cloud Security (Mar 07, 2025).
Comments
Please log in or register to join the discussion