In a coordinated strike across nine countries, authorities have dismantled over 1,000 servers powering the Rhadamanthys infostealer, VenomRAT, and Elysium botnet, marking a decisive new phase of Operation Endgame. For defenders and adversaries alike, this is a turning point in the economics of malware-as-a-service—and a warning that infrastructure is now the weakest link.
 )
)
On paper, the numbers look like yet another cybercrime press release: nine countries, over 1,000 servers seized, 20 domains taken down, one key suspect arrested.
In practice, this latest phase of Operation Endgame is something more serious: a direct strike on the infrastructure backbone of three prolific malware ecosystems—Rhadamanthys (infostealer), VenomRAT (remote access trojan), and Elysium (botnet)—and a case study in how coordinated disruption is reshaping both defensive strategy and the malware-as-a-service (MaaS) market.
Source: BleepingComputer – Police disrupts Rhadamanthys, VenomRAT, and Elysium malware operations
What Actually Happened
Between 10 and 14 November 2025, law enforcement agencies—coordinated by Europol and Eurojust and backed by a who's who of threat intel and security vendors, including Cryptolaemus, Shadowserver, Spycloud, Proofpoint, CrowdStrike, Lumen, Abuse.ch, DIVD, Bitdefender, Spamhaus, Cymru, HaveIBeenPwned, and others—executed synchronized actions against the infrastructure underpinning these operations.
Key actions:
- 1,025 servers taken down across multiple hosting providers.
- 20 domains seized.
- 11 locations searched in Germany, Greece, and the Netherlands.
- A key suspect arrested in Greece tied to VenomRAT.
Europol reports that the disrupted infrastructure fronted hundreds of thousands of infected endpoints and held several million stolen credentials, including access to more than 100,000 cryptocurrency wallets—an underground treasury potentially worth millions.
For many victims, this will be the first hint their systems were ever compromised.
Why This Phase of Operation Endgame Is Different
Operation Endgame isn't new, but this wave hits a strategic pivot point. Earlier phases focused on major loaders and botnets (IcedID, Bumblebee, Pikabot, Trickbot, Smokeloader, SystemBC) and associated ransomware ecosystems.
This round goes after three pillars of the current cybercrime stack:
- Rhadamanthys – a high-end infostealer MaaS, popular with credential and wallet thieves.
- VenomRAT – a lightweight, commodity RAT used for persistence, surveillance, and staging follow-on attacks.
- Elysium – a botnet platform, providing distributed infrastructure for spam, DDoS, or payload delivery.
Together, these systems form an attack chain many defenders know too well: steal credentials → obtain remote control → weaponize access at scale.
By dismantling their infrastructure, law enforcement is not just “arresting bad guys”; it’s striking at the operational viability of MaaS as a business model.
When the Control Panel Goes Dark
Confirmation of the disruption didn’t just come from Europol. It came from the criminals themselves.
In messages shared on Telegram and reported by BleepingComputer, the Rhadamanthys developer acknowledged the outage, noting that web panels hosted in EU data centers showed German law enforcement IPs shortly before access was lost.
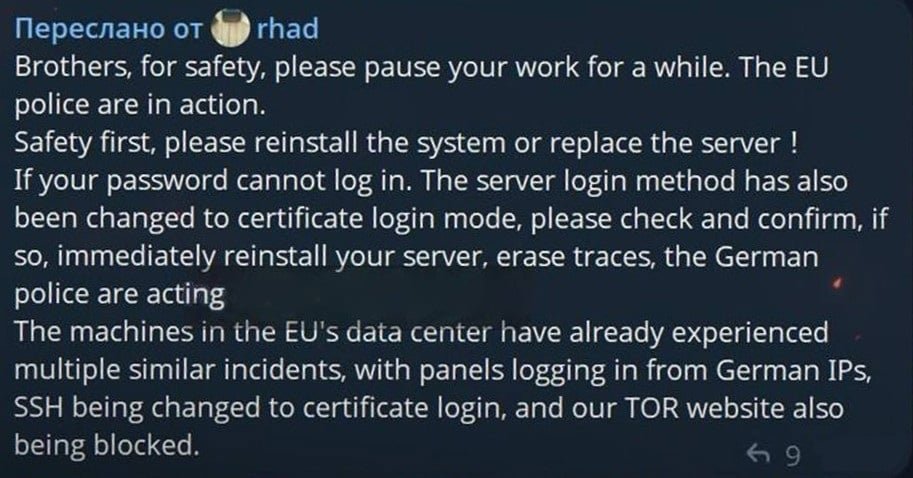
For operators and customers of these services, the implications are stark:
- Reliability—the key selling point of professionalized cybercrime—is under direct, persistent pressure.
- Hosting in “friendly” jurisdictions or bulletproof providers no longer guarantees uptime.
- Forced migrations to more ephemeral infrastructure (fast-flux, Tor hidden services, decentralized control) increase complexity and cost for attackers.
This is infrastructure warfare—and for once, it’s tilted in favor of defenders.
What This Means for Security Teams and Engineers
For practitioners, this disruption is an opportunity, not a victory lap.
1. The Credential Theft Problem Is Bigger Than You Think
The mention of millions of credentials and access to 100,000+ crypto wallets should recalibrate your threat model:
- Assume long-term persistence of stolen credentials in criminal markets.
- Treat password-only auth as effectively compromised.
- Tighten MFA coverage, especially for:
- cloud consoles and CI/CD platforms
- remote access (VPN, RDP, jump hosts)
- identity providers and SSO
At scale, credentials are still the cheapest, quietest path into your environment.
2. Incident Response: Turn This Takedown Into a Detection Sprint
Use the Operation Endgame window to:
- Cross-check exposure: Europol recommends:
- Hunt for historical compromise:
- Outbound C2 to infrastructure previously associated with Rhadamanthys, VenomRAT, Elysium.
- Unusual remote desktop, PowerShell, or process injection activity from endpoints now known to be infected.
- Invalidate at scale:
- Rotate credentials that may have been exposed.
- Reissue API tokens and long-lived service credentials.
Takedowns buy time; they do not reset your environment.
3. Builder vs. Buyer: Shifts in the Underground Supply Chain
Every time law enforcement successfully disrupts a MaaS platform, two things happen:
- Less capable actors are locked out, unable to self-build.
- More capable actors go further underground, investing in:
- hardened, multi-layer C2
- self-hosted panels on compromised infrastructure
- custom cryptors and loaders (as seen in prior Conti/LockBit collaborations)
For blue teams, expect:
- More bespoke variants and short-lived infrastructures, reducing IOC reuse but increasing behavioral detection value.
- Greater emphasis on initial access brokers leveraging infostealers; cutting their supply chain remains critical.
How Developers and Infrastructure Teams Can Respond Practically
If you build or operate systems, you are in the blast radius of infostealers and RATs, whether you see it or not. A few concrete measures that directly counter the tools hit in this operation:
Protect developer credentials like production secrets.
- Store tokens, SSH keys, and cloud creds in a managed secrets vault.
- Enforce hardware-backed keys (FIDO2, smartcards) for Git, CI, and cloud admin roles.
Instrument for anomalous control-plane activity.
- Alert on new API keys, new OAuth apps, or MFA resets from unusual IPs/ASNs.
- Monitor for access to CI/CD from endpoints previously tied to stealer infections.
Contain remote access tooling risk.
- Strictly inventory and approve any remote control tools.
- Log process command lines; VenomRAT-like activity is often behaviorally obvious when visibility exists.
Build stealer-aware secure coding and ops culture.
- Assume that any secret used on a compromised endpoint will be exfiltrated.
- Design for revocability and scope limitation of all tokens and keys.
None of this is glamorous, but it is precisely where Rhadamanthys-class operations monetize their access.
A Fragile Victory, and a Strategic Signal
Operation Endgame will not end infostealers, RATs, or botnets. Infrastructure can and will be rebuilt; code can be rebranded and resold. But this wave sends an unambiguous signal: running industrialized cybercrime at scale now carries real operational fragility.
For defenders, that fragility is leverage:
- Use this disruption window to find latent compromises.
- Pressure attackers’ economics by hardening identity, secrets, and remote access.
- Support and consume the growing ecosystem of public–private threat intelligence collaboration that made this action possible.
The story here isn’t that police “took down 1,025 servers.” It’s that infrastructure is now a contested domain—one where coordinated, data-driven, cross-border action can meaningfully degrade the service quality of cybercrime. The next move belongs to both sides; how quickly we operationalize this moment will determine who benefits more.

Comments
Please log in or register to join the discussion