Kudelski Security engineers have engineered two novel approaches to fortify WireGuard against quantum attacks—one optimizing for speed using a modified Kyber KEM, the other slashing bandwidth via Rainbow signatures. Their open-source fork achieves handshakes under 5ms while halving packet overhead, proving practical post-quantum VPNs are within reach.
The ticking clock of quantum computing threatens to crack today’s cryptographic safeguards, and VPN protocols like WireGuard—renowned for speed and modern encryption—are no exception. While WireGuard’s symmetric tunnel encryption can be quantum-hardened by doubling key lengths, its handshake mechanism relies on elliptic-curve cryptography that quantum algorithms could dismantle. Kudelski Security’s latest research confronts this vulnerability head-on, delivering two optimized post-quantum handshake variants that balance speed and efficiency without compromising security.
The Quantum Handshake Dilemma
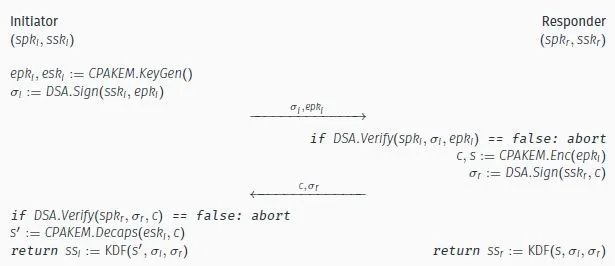
WireGuard’s handshake authenticates peers and establishes session keys using ephemeral elliptic curves. To quantum-proof this, prior work by Hülsing et al. replaced these curves with Kyber768, a lattice-based Key Encapsulation Mechanism (KEM) and NIST PQC finalist. Their "PQ-WireGuard" reduced client runtime to just 20.9ms but required four IP packets—a bottleneck for bandwidth-constrained networks. Kudelski’s team set out to push these limits further.
 Conventional VPN tunnels (like WireGuard’s) mask user traffic but rely on non-quantum-resistant handshakes.
Conventional VPN tunnels (like WireGuard’s) mask user traffic but rely on non-quantum-resistant handshakes.
Speed First: The Kyber Turbo-Charge
Building on Hülsing’s Fujioka-style authenticated key exchange (AKE)—which combines two KEMs—Kudelski replaced one Kyber instance with a tweaked CPA-secure variant. By stripping Fujioka’s transform and aggressively compressing ciphertexts, they slashed sizes by 22% while maintaining security via learning-with-rounding principles:
// Simplified tweaked Kyber (tKyber) workflow
ciphertext := Encrypt(publicKey, message, coins)
compressedCiphertext := Compress(ciphertext, d)
messagePrime := Decrypt(secretKey, compressedCiphertext)
This "K+tK" hybrid (static Kyber + ephemeral tKyber) cut client runtime to 0.50ms and traffic to 3,760 bytes—outpacing prior work by 45% in speed while using the same packet count.
{{IMAGE:4}} Fujioka’s AKE (left) vs. Kudelski’s tKyber optimization (right).
Bandwidth Revolution: Enter Rainbow
For low-bandwidth scenarios, the team pivoted to del Pino’s AKE, replacing the static-key KEM with Rainbow signatures—a post-quantum scheme with exceptionally compact signatures. Despite Rainbow’s large public keys, WireGuard’s design hashes these after initial exchange, amortizing overhead. The "R+tK" combo crunched handshake traffic to just 1,912 bytes (two packets) with a manageable 5.41ms server runtime:
| Approach | Traffic (B) | Packets | Client (ms) | Server (ms) |
|---|---|---|---|---|
| Prior PQ-WireGuard | 2532 | 4 | 20.9 | 20.3 |
| K+tK (Kyber focus) | 3760 | 4 | 0.50 | 0.29 |
| R+tK (Rainbow) | 1912 | 2 | 25.76 | 5.41 |
{{IMAGE:5}} del Pino’s AKE uses signatures instead of static KEMs—enabling drastic bandwidth savings.
Security and Practical Deployment
Critically, Kudelski preserved WireGuard’s deniability and anonymity by ensuring attackers couldn’t link handshakes to long-term keys. Their final implementation uses Kyber512 (≈AES-128 security) and Rainbow-I for optimal performance, with client runtimes as low as 0.27ms. All variants are open-sourced in their pq-wireguard fork, complete with deployment tutorials.
"We’ve shown that post-quantum WireGuard isn’t just theoretical—it’s practical today," the team notes. "Whether you prioritize latency or lean networks, there’s a quantum-resistant path forward."
Beyond the Lab
While Kudelski plans kernel-space ports for further optimizations, their work proves that VPNs can defy quantum threats without sacrificing WireGuard’s elegance. As quantum processors advance, such drop-in upgrades will be crucial for safeguarding privacy at scale—turning cryptographic agility from a luxury into a lifeline.
Source: Kudelski Security Research

Comments
Please log in or register to join the discussion