State-sponsored hackers and ransomware groups have converged to exploit critical Microsoft SharePoint vulnerabilities, compromising over 148 organizations including U.S. nuclear agencies and European governments. The newly identified 4L4MD4R ransomware variant amplifies threats from an exploit chain now linked to Chinese APTs. Emergency patches and CISA directives underscore the severity of this escalating crisis.
Ransomware Gangs Weaponize SharePoint Zero-Days in Global Cyber Assault

A dangerous convergence of state-sponsored espionage and criminal ransomware operations is exploiting critical flaws in Microsoft SharePoint servers, compromising at least 148 organizations worldwide. Security researchers have observed Chinese advanced persistent threat (APT) groups and ransomware gangs jointly leveraging an exploit chain dubbed "ToolShell," with the U.S. National Nuclear Security Administration, multiple government departments, and multinational corporations among the high-profile victims.
The ToolShell Exploit Chain Unleashed
The attack begins with exploitation of SharePoint vulnerabilities CVE-2025-49706 and CVE-2025-49704—initially used as zero-days—to gain initial access. Dutch firm Eye Security first detected these intrusions in July 2025, noting attackers swiftly deploy malware loaders that execute PowerShell commands to disable security controls. Palo Alto Networks' Unit 42 then identified a new threat: the 4L4MD4R ransomware being delivered through the same attack vector.
"Analysis of the 4L4MD4R payload revealed that it is UPX-packed and written in GoLang," Unit 42 researchers reported. "Upon execution, the sample decrypts an AES-encrypted payload in memory, allocates memory to load the decrypted PE file, and creates a new thread to execute it."
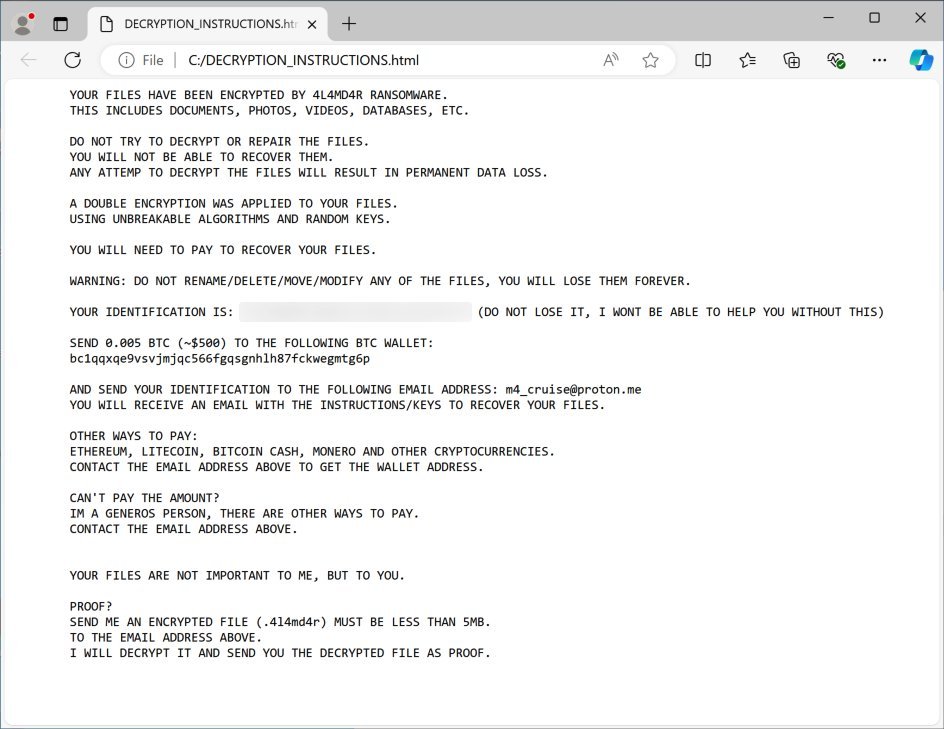
4L4MD4R ransom note and decryption instructions (Unit 42)
The ransomware, derived from open-source Mauri870 code, encrypts files and demands 0.005 Bitcoin (~$150). Its emergence signals ransomware groups capitalizing on vulnerabilities first exploited by nation-state actors—a troubling escalation in attack sophistication.
State-Sponsored Operators and Global Impact
Microsoft attributes the core ToolShell campaign to three Chinese threat groups:
- Linen Typhoon (APT41)
- Violet Typhoon
- Storm-2603
"Microsoft has observed two named Chinese nation-state actors exploiting these vulnerabilities targeting internet-facing SharePoint servers," the company confirmed. Government networks across Europe, the Middle East, and high-value U.S. targets—including Florida's Department of Revenue and Rhode Island's General Assembly—have been breached. Eye Security CTO Piet Kerkhofs revealed the true scale is likely higher, with at least 400 servers compromised in extended dwell-time intrusions.
Emergency Response and Patching Imperative
Microsoft issued patches for the original vulnerabilities in July 2025's Patch Tuesday, but subsequent discoveries revealed two additional zero-days (CVE-2025-53770 and CVE-2025-53771) enabling attacks on patched systems. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) took unprecedented action, adding CVE-2025-53770 to its Known Exploited Vulnerabilities catalog and mandating federal agencies patch within 24 hours.
Why This Cross-Hive Threat Matters
This campaign exemplifies three critical trends:
- Vulnerability weaponization velocity: Nation-state exploits are rapidly adopted by ransomware groups
- Supply chain amplification: A single SharePoint vulnerability chain can compromise entire networks
- Detection evasion: Memory-based payload decryption and security-tool disabling increase stealth

As detailed in Picus Security's Red Report 2025, 93% of malware attacks reuse core MITRE ATT&CK techniques—making behavioral analysis essential. For enterprises, immediate mitigation requires:
- Applying SharePoint patches immediately
- Monitoring PowerShell execution patterns
- Segmenting network zones to limit lateral movement
- Implementing ransomware-specific memory protection
The blurred line between geopolitical cyber operations and criminal profit-seeking now poses one of the most complex defense challenges of the decade. When state-sponsored tools leak into the criminal underground, every unpatched server becomes a potential catastrophe.
Source: BleepingComputer

Comments
Please log in or register to join the discussion