Microsoft reveals Russian state hackers linked to the FSB are hijacking local ISPs to launch adversary-in-the-middle attacks against diplomatic missions in Moscow, deploying custom malware disguised as Kaspersky antivirus. This ISP-level espionage campaign, ongoing since 2024, leverages Russia's lawful interception infrastructure for persistent intelligence gathering.

Microsoft has exposed a sophisticated cyber-espionage operation where Russian state hackers are exploiting their position within local internet service providers (ISPs) to target foreign embassies in Moscow. The group, tracked as Secret Blizzard (aka Turla, Waterbug, or Venomous Bear) and linked to Russia's Federal Security Service (FSB), uses its ISP-level access to deploy Adversary-in-the-Middle (AiTM) attacks, redirecting targets to malicious captive portals.
Victims are tricked into downloading a malware payload disguised as a Kaspersky antivirus installer. Once executed, the custom ApolloShadow malware installs a fraudulent root certificate masquerading as Kaspersky software. This allows the hackers to:
- Decrypt HTTPS traffic
- Maintain persistent access to compromised systems
- Spoof legitimate websites for credential theft
- Conduct long-term intelligence gathering
Microsoft states:
"This is the first time Microsoft can confirm Secret Blizzard's capability to conduct espionage at the ISP level, meaning diplomatic personnel using local internet providers and telecommunications in Russia are at high risk... This campaign poses a high risk to foreign embassies, diplomatic entities, and other sensitive organizations operating in Moscow."
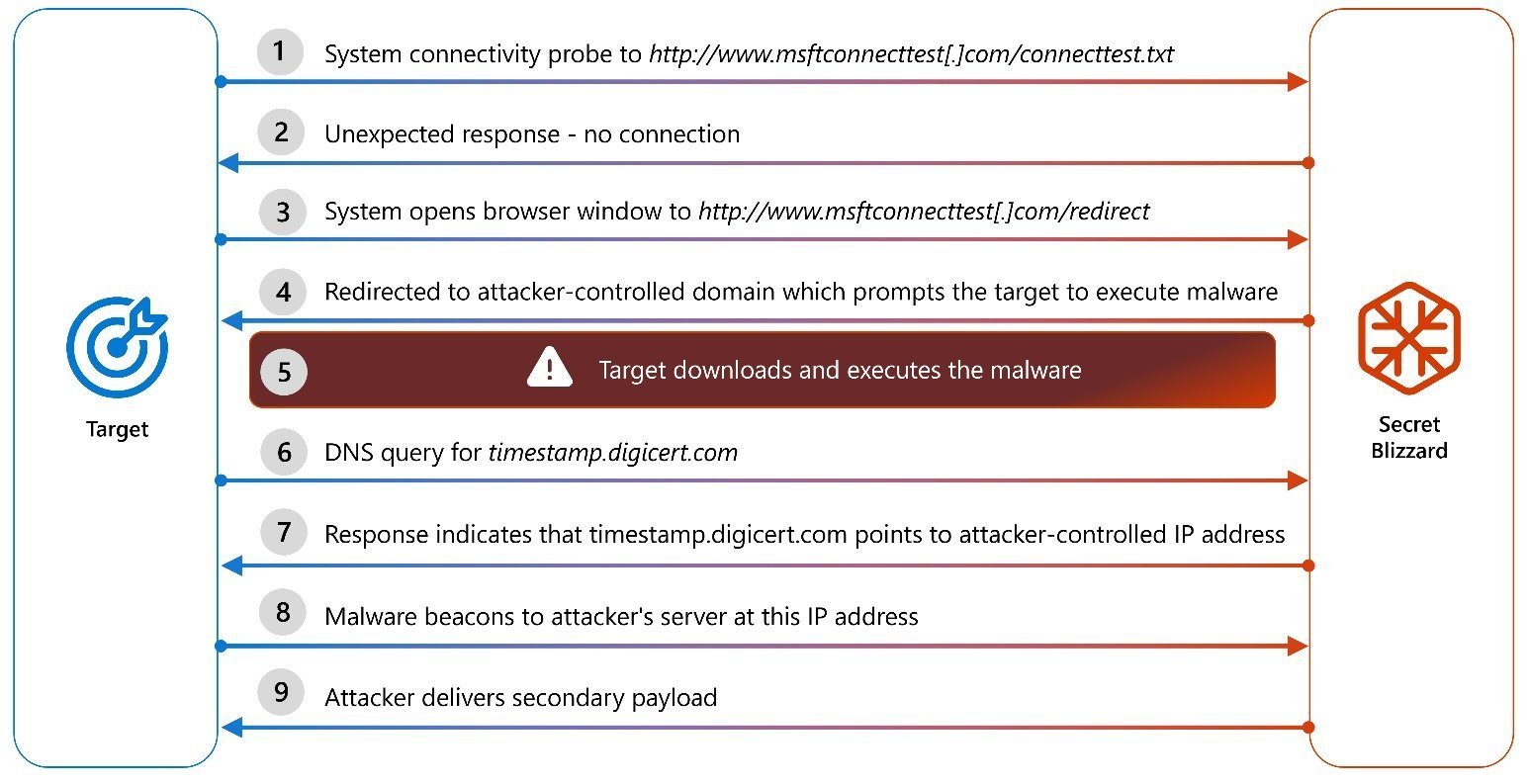 Microsoft's visualization of the Secret Blizzard infection chain
Microsoft's visualization of the Secret Blizzard infection chain
The hackers are reportedly exploiting Russia's System for Operative Investigative Activities (SORM) – the country's lawful interception infrastructure – to facilitate these large-scale attacks. Active since at least 1996, Turla is known for unconventional tactics including:
- Controlling malware via comments on Britney Spears' Instagram posts
- Developing backdoor trojans with custom APIs
- Hijacking infrastructure of other APTs (like Iran's OilRig) to mislead attribution
Recent activities include targeting Ukrainian military devices via compromised Starlink connections. This ISP-level campaign represents a significant escalation, demonstrating how nation-state actors weaponize fundamental internet infrastructure against high-value targets. Diplomatic entities relying on local Russian ISPs face critical exposure, with limited mitigation options beyond avoiding local telecommunications entirely.
Source: BleepingComputer

Comments
Please log in or register to join the discussion