Microsoft has uncovered a dangerous new variant of the XCSSET macOS malware that specifically targets developers by infecting Xcode projects. The upgraded malware now steals Firefox data, hijacks cryptocurrency transactions via clipboard manipulation, and employs advanced persistence techniques. This represents a significant escalation in supply chain attacks against Apple's developer ecosystem.
Sophisticated XCSSET Malware Evolves: Microsoft Warns of Enhanced macOS Threat Targeting Xcode Developers

Microsoft Threat Intelligence has identified a dangerous evolution in the XCSSET macOS malware, now targeting developers through compromised Xcode projects. This refined variant introduces alarming capabilities including Firefox data exfiltration, cryptocurrency theft via clipboard hijacking, and sophisticated persistence mechanisms—marking a significant escalation in supply chain attacks against Apple's developer community.
Anatomy of an Xcode Invasion
XCSSET operates as a modular macOS threat that specializes in stealing sensitive data including Notes app content, cryptocurrency wallets, and browser information. Its core infection vector remains uniquely dangerous: the malware actively hunts for Xcode project files (.xcodeproj), injecting malicious code that executes automatically when developers build their projects.
"The XCSSET malware is designed to infect Xcode projects, typically used by software developers, and run while an Xcode project is being built," Microsoft researchers emphasized. "This mode of infection banks on project files being shared among developers building Apple or macOS-related applications," creating a potent supply chain attack vector.
New Attack Capabilities Unveiled
Microsoft's analysis reveals three critical upgrades in this variant:
Expanded Browser Targeting: The malware now incorporates a customized version of the open-source HackBrowserData tool to decrypt and steal sensitive information from Firefox—expanding beyond its previous focus on Safari and Chromium-based browsers. This allows theft of browsing history, saved credentials, and session cookies.
Cryptocurrency Clipboard Hijacking: A refined monitoring component scans the macOS clipboard in real-time for cryptocurrency addresses using regex patterns. When detected, it silently replaces the victim's address with attackers' wallet IDs, diverting transactions:
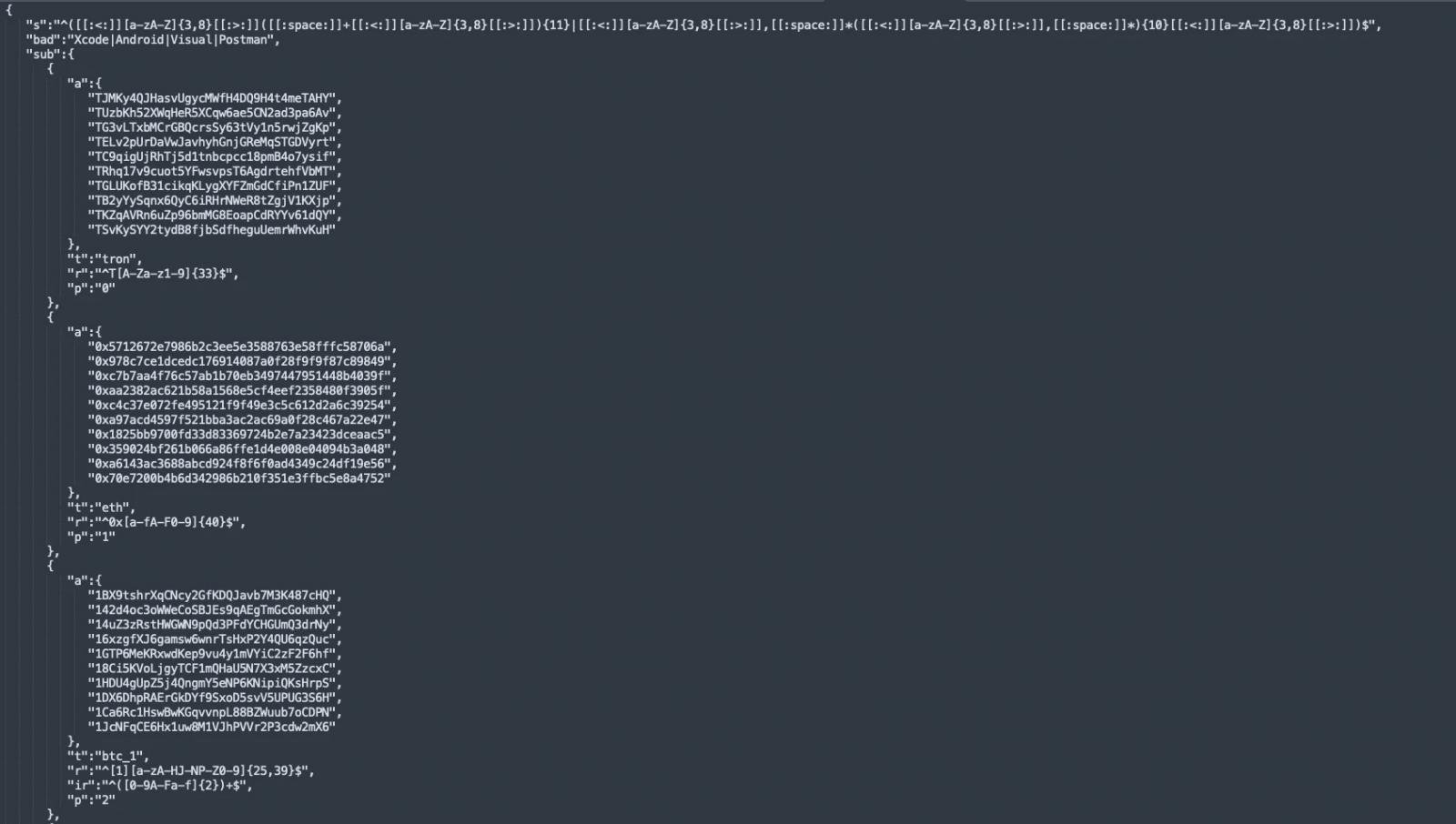
- Advanced Persistence Mechanisms: The malware establishes deeper footholds through:
- Fake
System Settings.appbundles in/tmpdirectories - LaunchDaemon entries executing hidden payloads (
~/.root) - Enhanced evasion techniques to avoid detection
- Fake
Targeted but Dangerous
While currently observed in limited attacks, the variant's sophistication poses disproportionate risks. Microsoft has shared findings with Apple and collaborated with GitHub to remove related repositories. The targeting of developers creates downstream risks: a single infected project could propagate malware to countless applications and end-users.
Mitigation Strategies for Developers
Microsoft recommends:
- Immediately patch macOS and all development tools, especially Xcode (XCSSET has exploited zero-days previously)
- Rigorously inspect Xcode projects from external sources before building
- Implement strict source control hygiene and sandboxing for third-party code
- Monitor for unexpected processes accessing clipboard or creating files in
/tmp
This evolution underscores a disturbing trend: development environments are now frontline targets. As attackers weaponize the tools used to create software, the industry must prioritize securing the pipeline—not just the products it delivers. For developers, vigilance against shared project files is no longer optional; it's existential defense.
Source: BleepingComputer (Microsoft Threat Intelligence)

Comments
Please log in or register to join the discussion