Traditional Identity Governance & Administration solutions burden enterprises with years of complex custom integrations, delaying security gains. Modern no-code alternatives promise weeks, not years, to operational governance while mitigating identity-based threats.
The IGA Imperative in an Identity-Driven Threat Landscape
As organizations grapple with escalating identity-based attacks and sprawling hybrid IT environments, Identity Governance & Administration (IGA) has shifted from a compliance checkbox to a core security imperative. Effective IGA delivers crucial capabilities: automated user lifecycle management, precise access control, separation of duties enforcement, and auditable compliance reporting. Yet, for many enterprises, the promise of streamlined governance remains elusive, shackled by the implementation nightmares of legacy solutions.
 Main article image: Visualizing the complexity of identity governance in modern enterprises.
Main article image: Visualizing the complexity of identity governance in modern enterprises.
Why Legacy IGA Implementations Become Quagmires
The fatal flaw of conventional IGA platforms lies in their dependency on exhaustive custom coding. While marketed as 'infinitely customizable,' this approach demands:
- Months (or Years) of Integration: Connecting to each application, directory, and cloud service requires building bespoke connectors from scratch.
- Massive Resource Drain: IT teams drown in planning sessions, data mapping exercises, and writing low-quality, rushed code to meet unrealistic timelines.
- Technical Debt Accumulation: Highly customized integrations become fragile and resist modification, creating long-term maintenance burdens.
- Delayed Value: Security and compliance benefits remain out of reach until the entire, protracted setup is complete.
"Legacy IGA’s promise of a platform tailored entirely to your specifications simply will not realize. Instead, you are left with a project that runs over time and over budget," the sponsored analysis notes, highlighting the unsustainable reality for most organizations.
The No-Code Alternative: Accelerating Governance Outcomes
Emerging no-code IGA platforms represent a paradigm shift, prioritizing rapid deployment and operational agility. By leveraging extensive libraries of pre-built, high-quality connectors and workflows:
- Implementation collapses from years to weeks: Connecting systems becomes a configuration exercise, not a development project.
- Resources are freed: IT security teams focus on policy and oversight, not writing integration code.
- Maintenance is simplified: Vendor-managed plugins receive updates, reducing upgrade friction.
- Value is immediate: Core governance controls (provisioning, access reviews, SoD) activate rapidly.
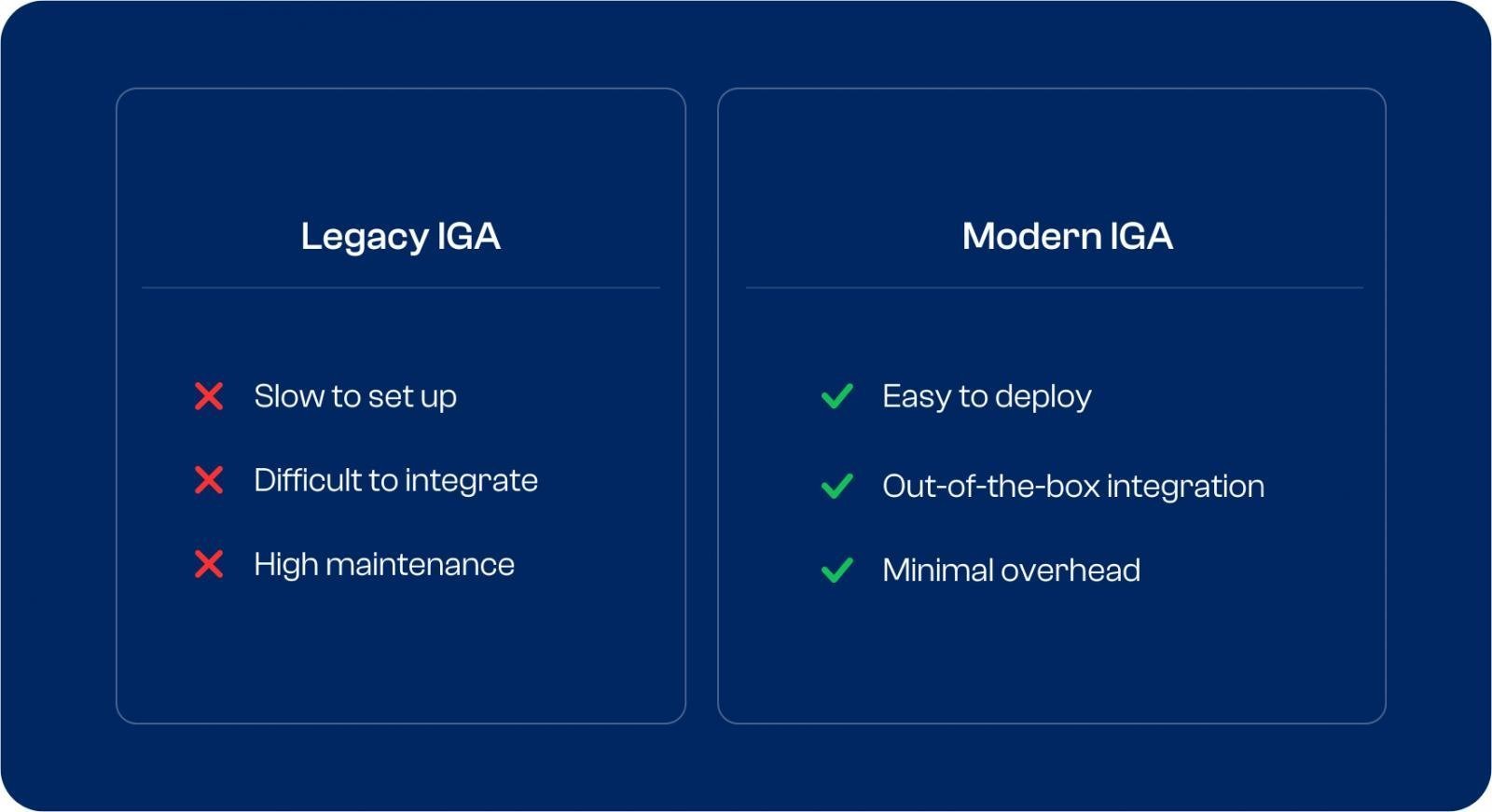 Modern vs Legacy IGA: Contrasting implementation complexity and time-to-value.
Modern vs Legacy IGA: Contrasting implementation complexity and time-to-value.
The Strategic Shift: Choosing the Right IGA Path
The choice between legacy and modern IGA is no longer just about features; it's about velocity and adaptability. Organizations facing dynamic threats and regulatory pressures cannot afford multi-year deployments riddled with technical debt. While complex, highly customized legacy deployments may still fit unique mega-enterprise needs, the majority of businesses require leaner solutions delivering:
- Faster Security Posture Improvement: Immediate enforcement of least privilege and access reviews.
- Reduced Operational Burden: Freeing security and IT teams from integration quagmires.
- Continuous Adaptability: Easily modifying workflows or adding systems as the business evolves.
The evolution of IGA signifies a broader trend: security tools must deliver tangible, rapid outcomes without becoming infrastructure projects themselves. As identity remains the primary attack vector, the speed at which governance is achieved becomes a critical competitive – and security – differentiator.
Source: Sponsored analysis based on content originally published by tenfold Software via BleepingComputer (September 5, 2025).

Comments
Please log in or register to join the discussion