Cybercriminals are exploiting Meta's advertising platforms to distribute Brokewell Android malware disguised as TradingView Premium apps. The sophisticated campaign targets cryptocurrency assets and bypasses 2FA protections through device takeovers. Researchers at Bitdefender uncovered over 130 remote commands enabling full surveillance and financial theft.
Brokewell Malware Hijacks Android Devices Through Fake TradingView Ads

A dangerous malvertising campaign is leveraging Meta's advertising ecosystem to distribute the advanced Brokewell malware to Android users, cybersecurity researchers at Bitdefender revealed. Since July 22nd, threat actors have run approximately 75 localized ads impersonating TradingView's market analysis platform, luring victims with promises of free premium access. The operation specifically targets mobile users—redirecting Android devices to malicious domains while showing harmless content to other platforms.
Anatomy of the Attack
The fraudulent ads mimic TradingView's branding and visuals, creating a convincing facade for the trap. When Android users click, they're redirected to a spoofed TradingView site hosting tw-update.apk—a malicious payload that initiates the compromise.
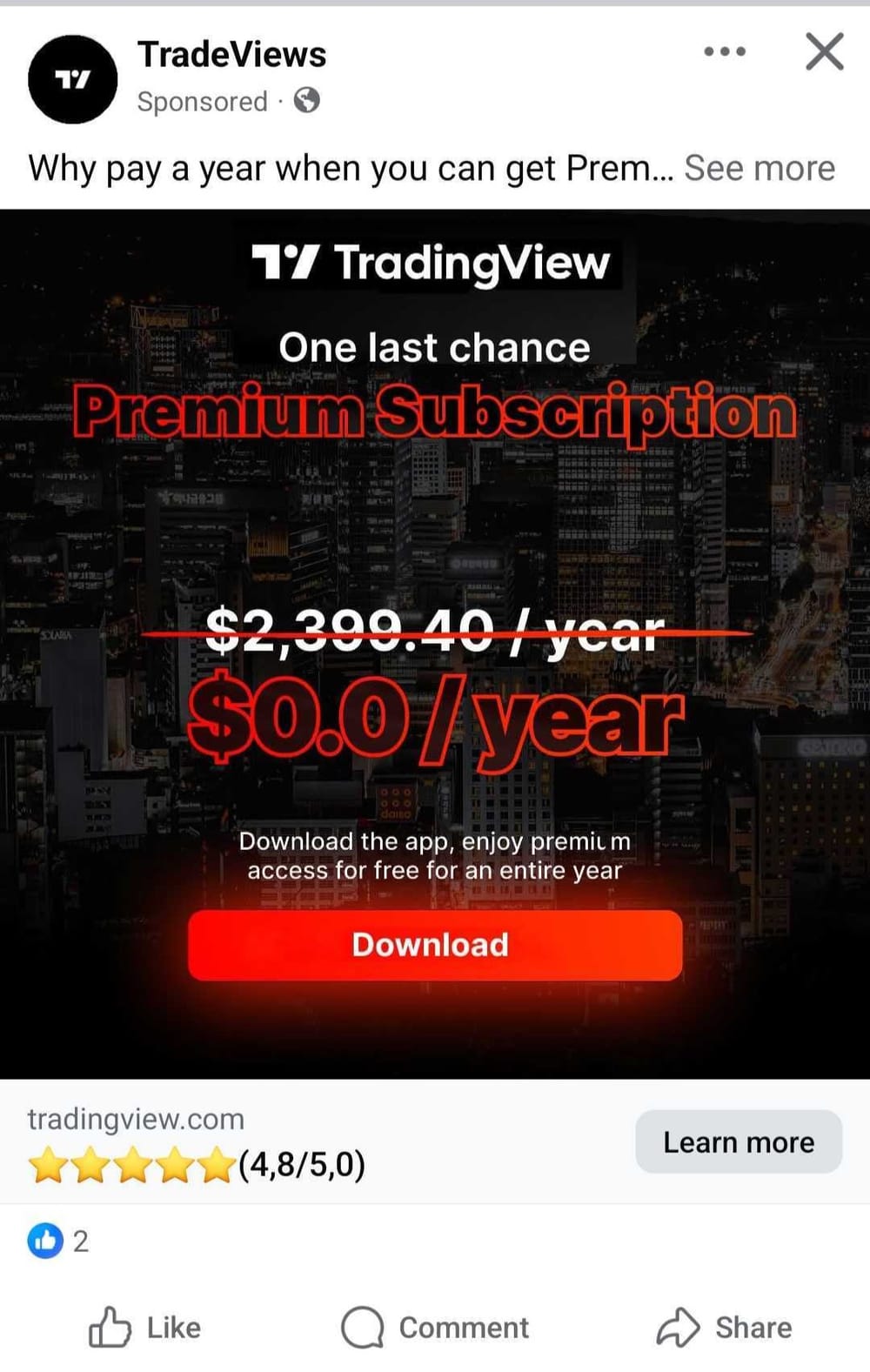
Source: Bitdefender
Upon installation, the malware requests accessibility permissions, then overlays a fake system update screen while silently granting itself extensive privileges in the background. In a particularly invasive maneuver, it attempts to steal device unlock PINs by simulating Android update prompts.
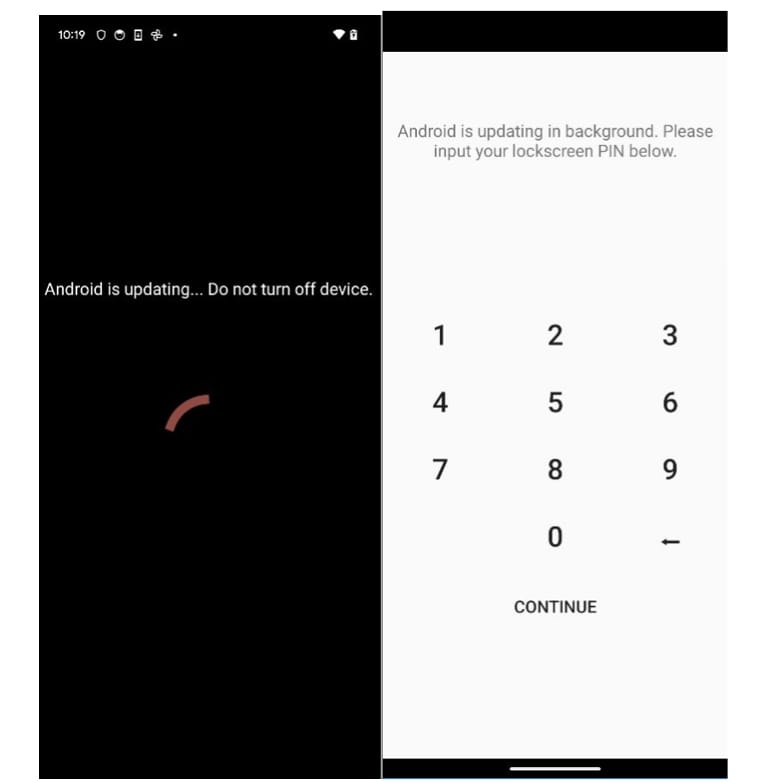
Source: Bitdefender
Brokewell's Devastating Capabilities
This evolved version of Brokewell—first observed in early 2024—operates as a Swiss Army knife for digital theft:
- Cryptocurrency targeting: Scans for BTC, ETH, and USDT wallets alongside bank account numbers (IBANs)
- 2FA compromise: Exports Google Authenticator codes to bypass security
- Real-time surveillance: Records screens, keystrokes, location data, and activates cameras/microphones
- Credential theft: Deploys overlay attacks mimicking login screens
- SMS hijacking: Intercepts messages including banking/2FA codes by becoming default messaging app
- Remote control: Executes commands via Tor/WebSockets (call/text, app removal, self-destruct)
Bitdefender's technical analysis identified over 130 supported commands, enabling near-total device control. The malware's modular design suggests ongoing development focused on financial exploitation.
Bigger Threat Landscape
This campaign forms part of a broader operation previously targeting Windows users through Facebook ads impersonating major brands. The shift toward Android—and specifically cryptocurrency enthusiasts—highlights attackers' adaptability in exploiting high-value niches. Security teams should note Brokewell's use of Tor for C2 communications, complicating detection efforts.
For developers and security professionals, this underscores the critical need to:
- Educate users about sideloading risks and "too-good-to-be-true" offers
- Implement runtime protection against accessibility service abuse
- Monitor for anomalous network traffic (especially Tor connections)
- Advocate for verified app stores despite their limitations
As malvertising grows more sophisticated, the boundary between legitimate advertising and cybercrime continues to blur—making vigilance the price of mobile security.
Source: BleepingComputer
Comments
Please log in or register to join the discussion