CISA has ordered U.S. federal agencies to urgently patch a critical Samsung vulnerability, CVE-2025-21042, exploited since mid-2024 to deploy LandFall spyware via malicious WhatsApp messages. The flaw enables remote code execution on high-end Samsung devices, compromising sensitive data like calls, locations, and files. All organizations are urged to prioritize this update amid escalating mobile security threats.

In a decisive move highlighting escalating mobile security risks, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has mandated federal agencies to patch a critical Samsung zero-day vulnerability actively exploited to install sophisticated spyware. Tracked as CVE-2025-21042, this out-of-bounds write flaw resides in Samsung’s libimagecodec.quram.so library and allows attackers to execute arbitrary code remotely on devices running Android 13 or later—simply by sending a malicious DNG image file through WhatsApp.
The Exploitation Timeline and Spyware Payload
Samsung patched the vulnerability in April 2025 after reports from Meta and WhatsApp’s security teams. However, as Palo Alto Networks' Unit 42 revealed, threat actors had weaponized it as early as July 2024 to deploy 'LandFall' spyware. This malware harvests a chilling array of victim data, including:
- Call recordings, audio surveillance, and real-time location tracking
- Browsing history, photos, SMS, call logs, and contact lists
- Files and documents stored on the device
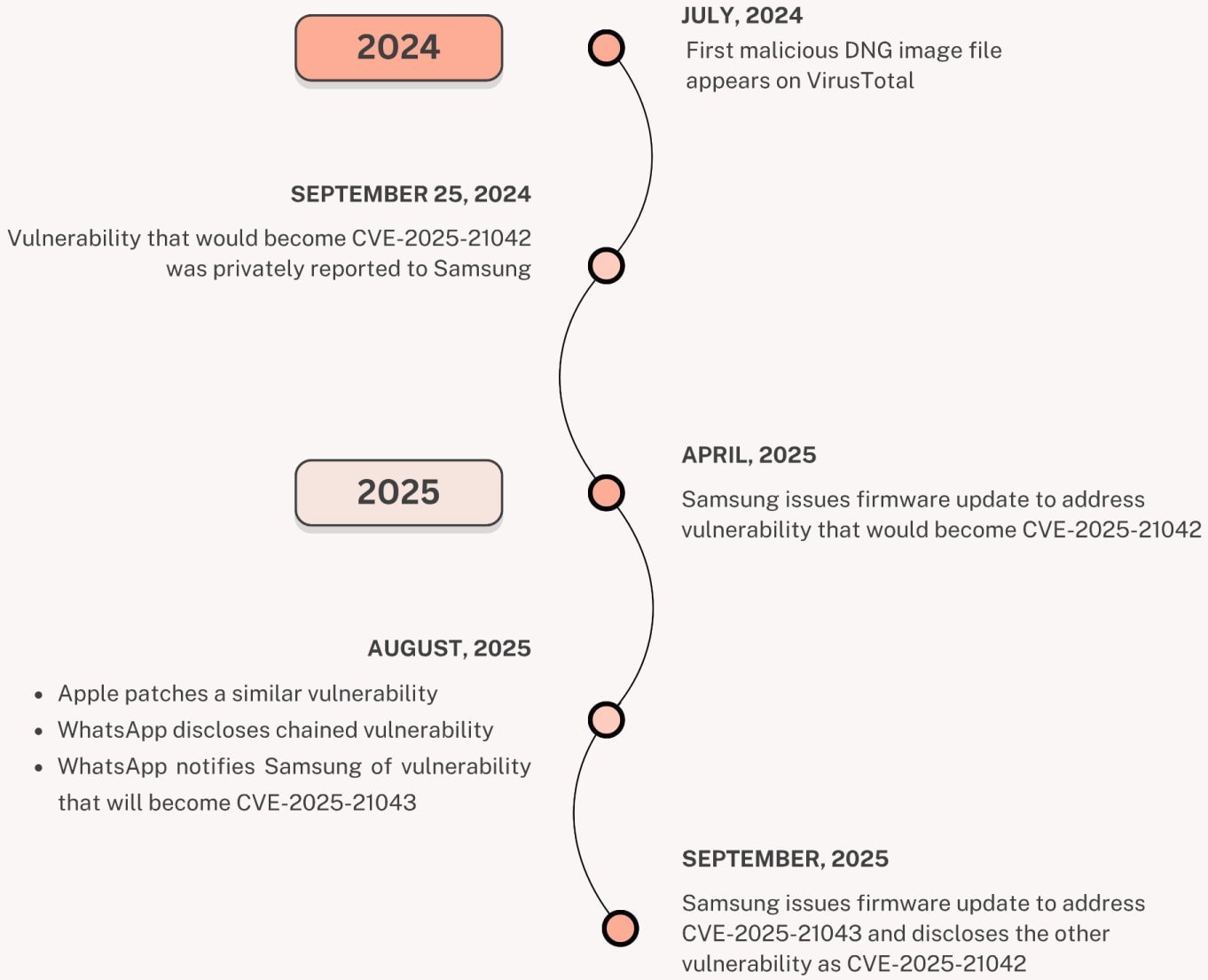 CVE-2025-21042 exploitation timeline (Unit 42)
CVE-2025-21042 exploitation timeline (Unit 42)
Targets span flagship Samsung models like the Galaxy S22-S24 series and Z Fold/Flip 4, with infections concentrated in Iraq, Iran, Turkey, and Morocco. Unit 42 analysts noted infrastructure similarities to the UAE-linked 'Stealth Falcon' group and the use of 'Bridge Head' malware loader terminology—a hallmark of commercial spyware vendors like NSO Group—though LandFall’s origins remain unconfirmed.
CISA’s Directive and Broader Implications
CISA added CVE-2025-21042 to its Known Exploited Vulnerabilities catalog, compelling Federal Civilian Executive Branch (FCEB) agencies—including Treasury, Homeland Security, and Health—to apply patches by December 1. As CISA warned:
"This type of vulnerability is a frequent attack vector for malicious cyber actors and poses significant risks to the federal enterprise. All organizations should prioritize patching immediately."
While the order binds non-military federal bodies, the advisory stresses that every enterprise using affected Samsung devices is at risk. This incident underscores a worrying trend: Samsung patched another zero-day (CVE-2025-21043) in the same library just months ago, signaling relentless targeting of mobile supply chains.
The persistence of such exploits—leveraging trusted apps like WhatsApp—demands rigorous update protocols and heightened scrutiny of image-processing components. As spyware vendors evolve, timely patching isn’t just compliance; it’s a frontline defense against silent, invasive surveillance.
Source: BleepingComputer

Comments
Please log in or register to join the discussion