A vulnerability in DoorDash's business platform allowed anyone to send convincing, branded phishing emails from official servers, remaining unpatched for over 15 months despite reports. The discovery sparked a heated dispute between the researcher and DoorDash, highlighting tensions in vulnerability disclosure and bug bounty ethics. While the flaw is now fixed, the case underscores the challenges of aligning security research with corporate responses.
DoorDash Email Spoofing Flaw Ignites Bug Bounty Battle: 15 Months of Neglect and Ethical Clashes
In the fast-paced world of food delivery, DoorDash has built an empire on seamless digital interactions. But a recently patched vulnerability in its DoorDash for Business platform exposed a glaring weakness: anyone could hijack the company's email infrastructure to send "official" branded messages, perfect for phishing scams. Discovered by pseudonymous security researcher doublezero7, this flaw turned a routine business tool into a potential weapon for social engineering, raising alarms about how delivery giants secure their backend systems.

The vulnerability stemmed from a simple yet dangerous oversight in the platform's budget management feature. Users could create free DoorDash for Business accounts and access admin dashboards to add employees, assign meal-expense budgets, and compose emails with arbitrary HTML content. These messages, sent from [email protected], arrived in recipients' inboxes without triggering spam filters, complete with DoorDash's authentic templates. As the researcher explained to BleepingComputer, the issue rooted in an unescaped input field for budget names, stored as raw text and rendered directly in emails. By injecting unclosed HTML tags and CSS like display:none, attackers could hide legitimate content and insert malicious payloads, such as fake voucher claims.
"The root was Budget name input field. It was stored as raw text in database and forwarded to email where it would be rendered," the researcher told BleepingComputer. "Using unclosed tags I could have altered the entire block of text about Budget information and using display:none it was possible to hide it completely and replace with crafted payload."
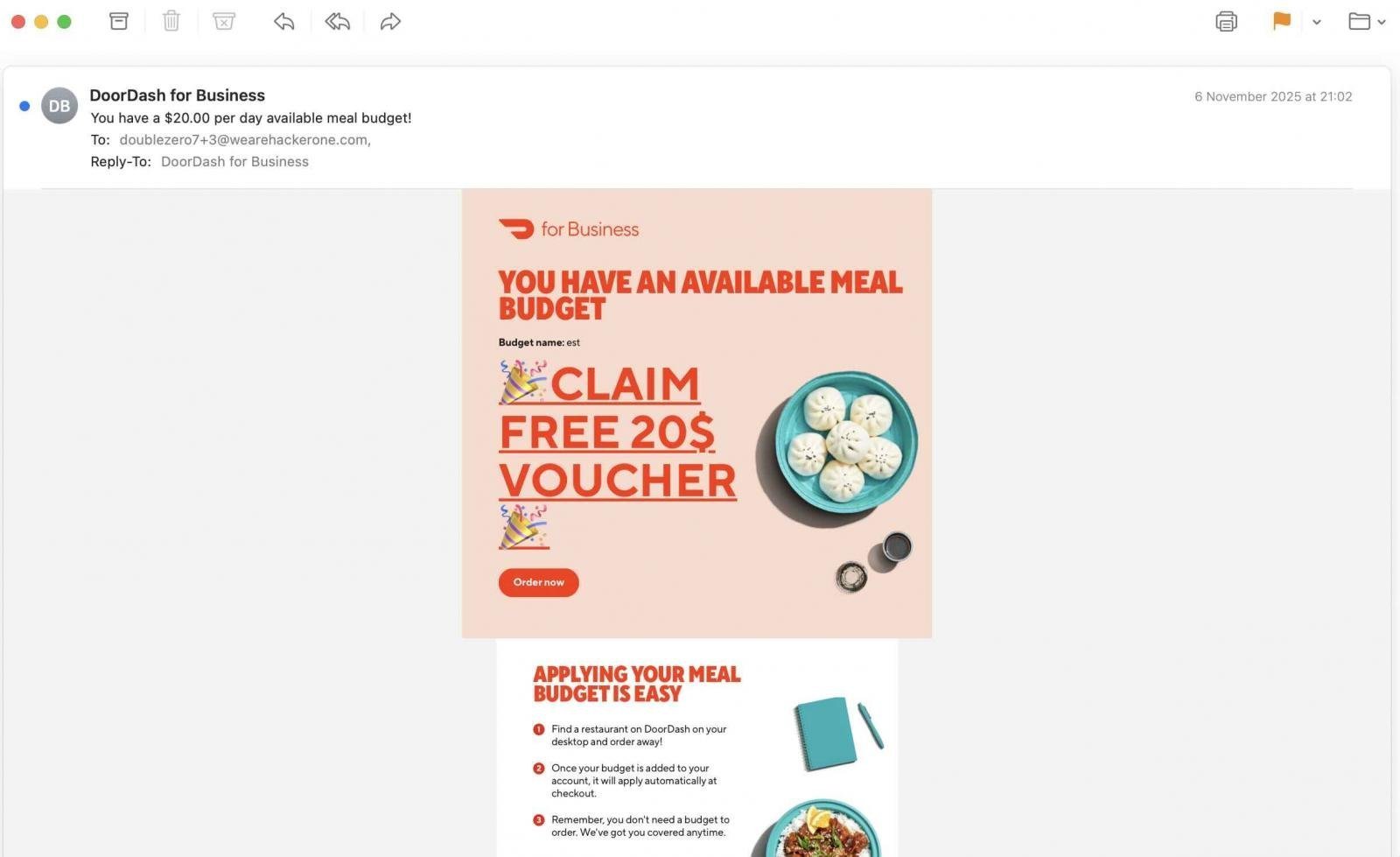
This wasn't limited to DoorDash's ecosystem; threat actors could target any email address, broadening the phishing potential. The exploit echoed a similar unpatched flaw in Uber's email system from 2022, where outsiders sent messages from official domains. For developers and security professionals, this highlights persistent risks in email templating systems, where stored cross-site scripting (XSS)-like vulnerabilities can bypass client-side defenses if email clients render HTML without strict sanitization.
The disclosure process, however, devolved into controversy. Doublezero7 reported the issue via HackerOne in early 2023, but DoorDash marked it as "Informative" and closed the ticket by July 2024, leaving it exploitable for 15 months. Frustrated, the researcher published a vague summary online and later emailed DoorDash directly, offering a compensated NDA for silence—a move they later admitted was "less ethical." The company patched the flaw within hours of this ultimatum but banned the researcher from its bug bounty program, labeling the approach as extortionate.
DoorDash's spokesperson emphasized their commitment to ethical research: "DoorDash operates a bug bounty program to work with security researchers to help find and fix potential security vulnerabilities. In this case, this individual attempted to extort DoorDash for money. They were subsequently banned from our bug bounty program. The issue reported fell outside the scope of our bug bounty program. Our security team has taken action to address the issue reported."
HackerOne corroborated the ban, stating actions were consistent with their Code of Conduct. The researcher countered that the delay justified their escalation, arguing DoorDash benefited from free labor without compensation or timely fixes. While the flaw didn't compromise user data or internal access—requiring recipient interaction to succeed—its potential for convincing phishing underscores why such vectors demand swift remediation.
{{IMAGE:4}}
This saga reveals deeper fault lines in the bug bounty ecosystem. For tech leaders, it serves as a cautionary tale: clear scopes, transparent communication, and mediation can prevent escalations. Developers building similar platforms should prioritize input sanitization in email generation, perhaps adopting libraries like DOMPurify for server-side rendering or switching to plain-text templates to mitigate HTML injection risks. As phishing evolves, incidents like this remind the industry that even minor flaws in trusted communications can erode user trust, especially in consumer-facing services like DoorDash where billions of interactions occur annually.

Comments
Please log in or register to join the discussion