Discover the sophisticated lifecycle of an Amazon CloudFront request, from DNS resolution to origin response. This deep dive reveals the orchestration of edge functions, caching layers, and security checks that power modern web delivery—essential knowledge for optimizing performance and security in global applications.

When a user clicks a link to a CloudFront-powered application, an intricate ballet of infrastructure springs into action. Far more than a simple content delivery network (CDN), Amazon CloudFront executes a meticulously choreographed sequence involving edge computing, security enforcement, and caching logic across its global network. Understanding this flow isn't academic—it's critical for developers architecting high-performance web applications and securing digital experiences.
The Infrastructure: Edge Locations and Regional Caches
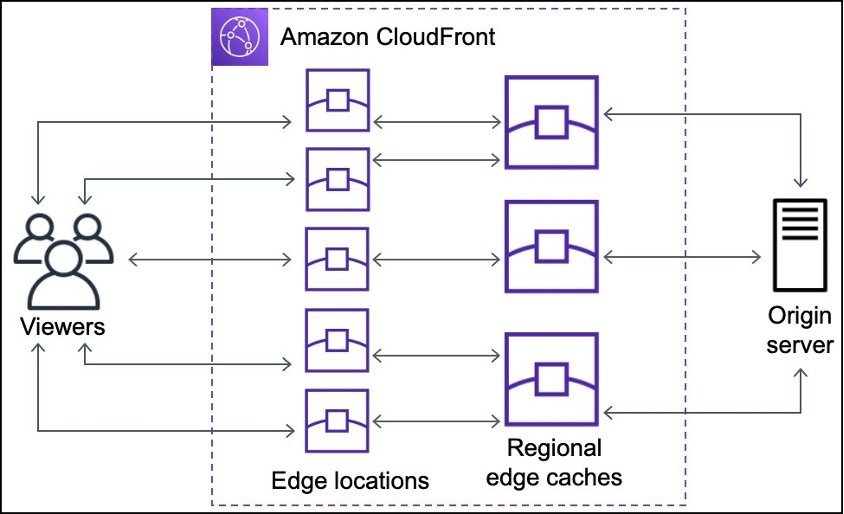
CloudFront's backbone comprises Points of Presence (POPs) and Regional Edge Caches (RECs). POPs—distributed globally—handle initial user connections, request routing, and lightweight edge functions. RECs operate deeper in the network, managing advanced compute tasks via Lambda@Edge and acting as macro-caching layers between POPs and origins. This tiered design balances low-latency responses with efficient origin offload. Notably, CloudFront supports HTTP/S, gRPC, and WebSockets, though HTTP/S remains the focus here.
Step-by-Step: Anatomy of a Request
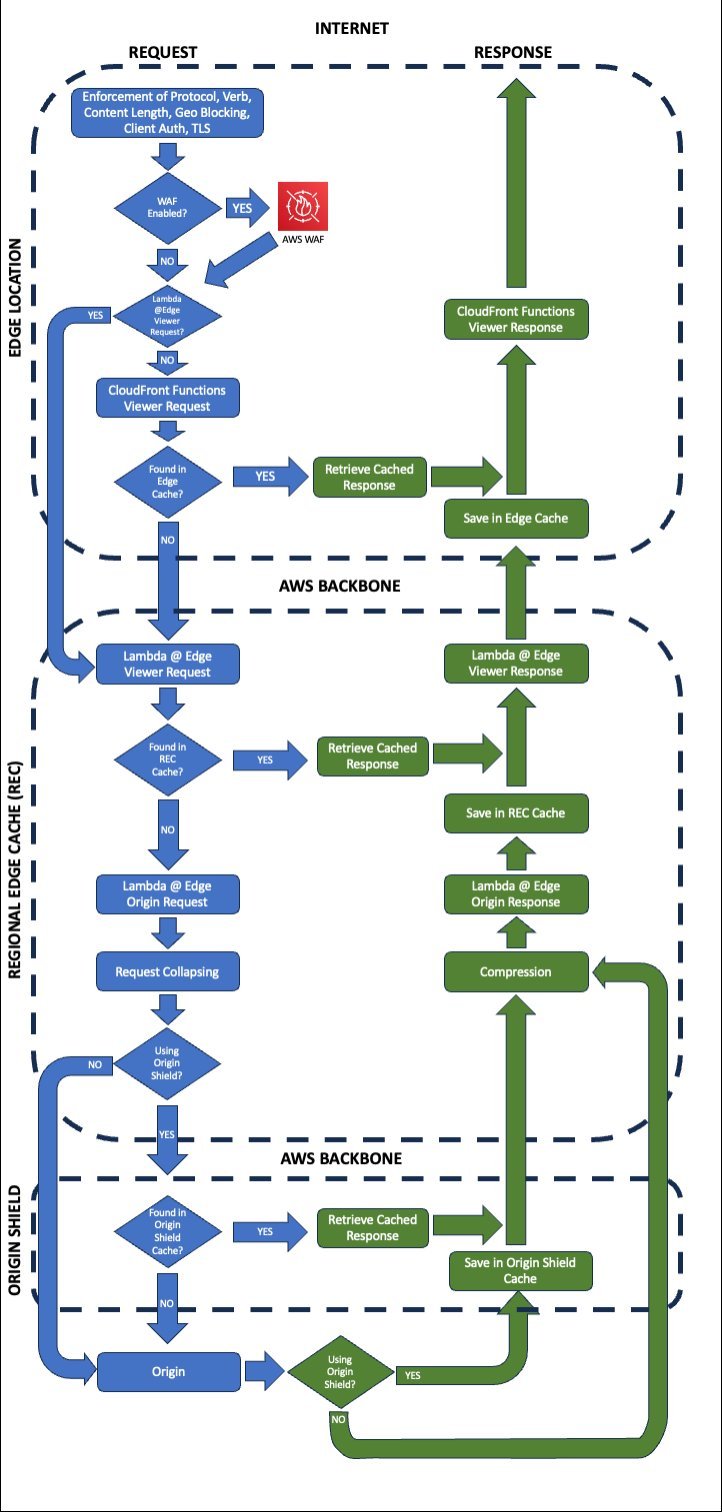
DNS Resolution & POP Selection
The journey starts with DNS. CloudFront uses real-time network health data to direct users to optimal POPs. Developers can constrain POP selection via Price Classes to balance cost and coverage—a trade-off visible through CloudWatch Network Monitor.TLS Handshake & Shield Protection
Upon connecting, TLS negotiation occurs using the distribution's security policy. Crucially, every POP benefits from AWS Shield Standard, mitigating volumetric DDoS attacks at the edge.Request Routing & Validation
A request router distributes traffic across cache servers while an RFC-compliance layer filters malformed or ambiguous syntax—a first line of defense against protocol-level exploits.AWS WAF: The Security Gatekeeper
If enabled, AWS WAF evaluates requests against WebACL rules before caching or behavior processing. This sequencing ensures threats like SQL injection or XSS are neutralized early.Behavior Matching & Edge Functions
Path patterns trigger specific behaviors dictating origin routing, cache policies, and header manipulation. Here, CloudFront Functions (JavaScript) execute at POPs for nanosecond-scale transformations, while Lambda@Edge runs at RECs for heavier tasks like request modification.Caching: The Multi-Layer Hunt
POPs search cache tiers sequentially. On a miss, requests escalate to RECs—which perform their own cache checks and execute origin-request Lambda@Edge. Origin Shield (optional) further optimizes cache efficiency by consolidating requests.Origin Fetch & Response
After RECs resolve origin DNS (enabling Route 53 policies), responses traverse backward:
- Lambda@Edge modifies origin responses at RECs
- CloudFront Functions tweaks viewer responses at POPs
- Compression and caching policies apply en route
Why This Orchestration Matters
Understanding this sequence isn't theoretical. Misconfigured behavior orders can break security or cripple performance. For instance:
- Security: WAF must precede edge functions to inspect unmodified traffic.
- Caching: Lambda@Edge origin requests run after cache misses—knowing this prevents redundant origin loads.
- Cost/Performance: Heavy Lambda@Edge at RECs adds latency; CloudFront Functions at POPs suit submillisecond tasks.
As applications demand lower latency and stricter security, mastering CloudFront's inner workflow becomes non-negotiable. Revisit your distributions: Optimize cache policies, validate function sequencing, and leverage Shield/WAF—because in the world of edge computing, every millisecond and every header counts.
Source: Based on the AWS Networking & Content Delivery blog post "Charting the life of an Amazon CloudFront request" by Sanchith Kandaka and Jorge Prado.

Comments
Please log in or register to join the discussion