A cosmetic bug in Windows 10 triggered incorrect end-of-support warnings across actively supported and ESU-enrolled systems. While Microsoft has now patched the issue, the incident underscores a deeper challenge for IT teams: maintaining trust, clarity, and control in a long-tail OS lifecycle.
 )
)
On paper, this week’s Windows 10 incident is minor: a cosmetic bug, a quick fix, no missed patches, no exploited zero-day.
In practice, it’s exactly the kind of glitch that drains trust between IT, security teams, and the platforms they’re supposed to rely on.
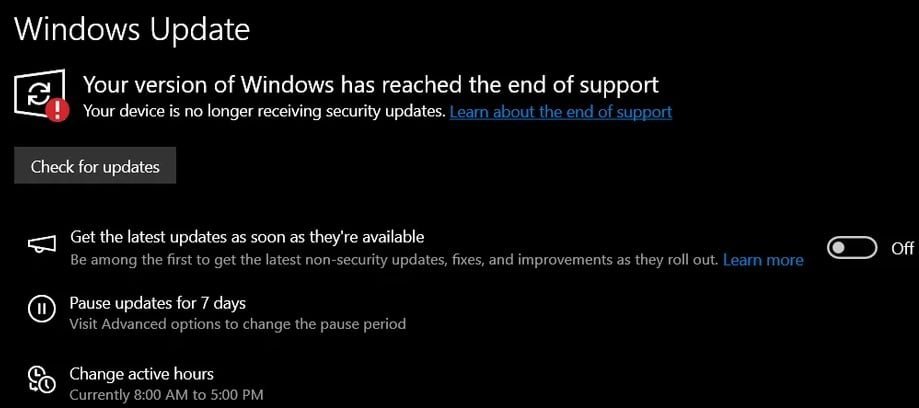
Microsoft has resolved a bug that caused Windows 10 systems—many of them validly licensed and fully supported—to display incorrect "Your version of Windows has reached the end of support" warnings following the October 2025 updates. The warnings appeared in Windows Update settings even for:
- Windows 10 22H2 Pro, Education, and Enterprise devices enrolled in the Extended Security Updates (ESU) program
- Windows 10 Enterprise LTSC 2021 (supported to January 2032)
- Windows 10 IoT Enterprise LTSC 2021 (supported to January 2029)
These devices never actually lost coverage. But the UI told admins otherwise.
What Actually Broke
The issue surfaced widely after last month’s Patch Tuesday, when organizations began reporting end-of-support (EOS) notices on systems they knew were properly licensed and managed.
Key points:
- The alerts were purely cosmetic: affected systems continued receiving security updates.
- Impacted builds were those under ESU or LTSC channels that remain formally supported.
- The problem originated in how Windows surfaced support state to users via Windows Update, not in ESU license validity or servicing stack behavior.
Microsoft first pushed a cloud configuration update to correct the message, but with caveats: devices that were offline, blocked from OneSettings downloads via Group Policy, constrained by strict firewalls, or otherwise unable to receive dynamic updates might never see the fix.
For an enterprise admin, that nuance matters. You don’t run production fleets on the assumption that "the cloud will nudge it right eventually."
The Fix: KB5068781 And A Safety Valve for Enterprises
On November 11, 2025, Microsoft released the first Windows 10 Extended Security Update package, KB5068781, which also formally resolves the erroneous EOS messaging:
"This issue was resolved by Windows updates released on November 11, 2025 (KB5068781), and updates released after that date. We recommend you install the latest update for your device as it contains important improvements and issue resolutions, including this one."
For enterprise environments that cannot immediately roll out KB5068781, Microsoft shipped a Known Issue Rollback (KIR) Group Policy to suppress the incorrect EOS messaging on managed devices. That gives IT a more deterministic lever:
- Apply KB5068781 where possible.
- Use the KIR policy where change windows, testing requirements, or regulatory constraints delay patch deployment.
It’s a clean resolution on paper—but the episode lands at a sensitive moment in the Windows lifecycle story.
Context: Windows 10’s Long Goodbye
Windows 10 officially reached end of support on October 14, 2025, for consumers and organizations not enrolled in ESU. Past that date, standard installations no longer receive patches for new vulnerabilities.
Extended Security Updates exist as a paid runway for organizations that:
- Have large legacy estates,
- Rely on hardware or line-of-business apps not yet ready for Windows 11,
- Or must stage migration carefully in regulated or high-availability environments.
Earlier this week—before KB5068781—Microsoft had to push an emergency out-of-band update to fix a separate bug that prevented some systems from enrolling in the ESU program. Combine that with false EOS warnings, and you get a worrying narrative for IT leaders:
- The licensing and eligibility model is complex.
- The visual signals in the OS can be wrong.
- The enrollment pipeline itself is fragile enough to warrant an out-of-band patch.
No single incident is catastrophic, but for admins responsible for tens or hundreds of thousands of endpoints, this is tension they don’t need.
Why This Matters More Than “Just a UI Bug”
For a technical audience, a cosmetic EOS warning is easy to dismiss—until you look at how modern IT operates:
Signal overload
- Admins and SOC teams rely on clear, accurate system cues to prioritize risk.
- False EOS warnings generate noise: tickets, escalations, audits, and compliance checks.
- Every false positive erodes confidence in the signals that should trigger real action.
Asset and lifecycle management
- EOS state is a control point for patch SLAs, segmentation policies, and regulatory reporting.
- If Windows says "end of support" on a system that’s contractually covered by ESU, it can:
- Trigger incorrect decommissioning workflows.
- Mislead compliance auditors.
- Skew CMDB and inventory accuracy if tools ingest that state.
Automation fragility
- Many organizations pipe Windows Update and support-status metadata into:
- Configuration management (Intune, SCCM, Ansible, Puppet, Chef)
- Security tooling (SIEM, XDR, vulnerability management)
- An incorrect EOS flag can cause playbooks to:
- Auto-quarantine systems considered "unsupported."
- Force replacement scheduling or OS upgrade tasks.
- Many organizations pipe Windows Update and support-status metadata into:
In other words, the "cosmetic" label is technically correct—no CVE, no missed patch—but operationally incomplete. At scale, trust in platform telemetry is a security control in itself.
Lessons for Enterprise IT and Developers
This bug is also a quiet warning about how we build and depend on cloud-mediated configuration logic and UI-driven trust signals.
For IT leaders and endpoint engineers:
Don’t treat the Windows UI as ground truth
- Cross-verify EOS and ESU status via authoritative channels:
- ESU license activation logs
- Volume licensing portals
- Endpoint management platforms and update compliance reports
- Ensure your security and compliance tools reference those sources, not just what Settings claims.
- Cross-verify EOS and ESU status via authoritative channels:
Make dynamic cloud config observable
- Cloud-based corrections (like the OneSettings-driven fix) are convenient but opaque.
- Where possible, log and monitor when these configurations are applied or blocked.
- Align firewall and Group Policy baselines so critical dynamic updates are either reliably allowed—or explicitly replaced by managed policies (like KIR).
For developers and product teams—especially those building management, RMM, or security tooling on top of OS signals—this is a design case study:
Treat vendor UI and status strings as non-authoritative
- Integrate with stable, documented APIs and licensing endpoints when determining lifecycle, support, or risk posture.
Build for graceful inconsistency
- Assume upstream platforms will occasionally misreport state.
- Implement validation layers and conflict detection (e.g., "ESU active + EOS warning = flag for review, not auto-remediation").
Communicate uncertainty explicitly
- When your product surfaces OS lifecycle status to customers, show how it was derived.
- If data sources conflict, expose that tension instead of masking it behind a single, falsely confident label.
Navigating the Last Miles of Windows 10
As Windows 10 transitions into its extended-support twilight, these "small" incidents carry outsized weight. Organizations paying to stay secure expect not only patches, but clarity.
Microsoft’s swift release of KB5068781 and the KIR option is the right move. But the bigger takeaway for enterprises is this:
If your operational posture assumes that the platform’s own messages are always accurate, you’re delegating too much trust to an increasingly complex, cloud-tuned signaling system.
In the final stretch of Windows 10’s lifecycle—and in every long-lived platform that follows—the winners will be the teams who verify, correlate, and instrument their own truth, rather than discovering in a crisis that "just a cosmetic bug" quietly rewired their assumptions.
Source: Original reporting based on Microsoft’s public guidance and issue documentation; primary incident coverage via BleepingComputer (https://www.bleepingcomputer.com/news/microsoft/microsoft-fixes-bug-causing-false-windows-10-end-of-support-alerts/).

Comments
Please log in or register to join the discussion