Microsoft’s first major Extended Security Updates (ESU) release for Windows 10 delivers 66 fixes— including a Windows Kernel zero-day—while quietly cementing a two-tier Windows world. For organizations and power users still anchored to Windows 10, this patch is less a courtesy and more a stark reminder: security now has a metered price.
 )
)
A New Era for an Old OS
Windows 10 was supposed to be over. Official support ended, the upgrade drumbeat to Windows 11 has been relentless, and Microsoft has made its strategic preferences perfectly clear.
And yet, as of this November Patch Tuesday, a huge installed base of Windows 10 machines has been granted something rare in consumer operating systems: a paid second life.
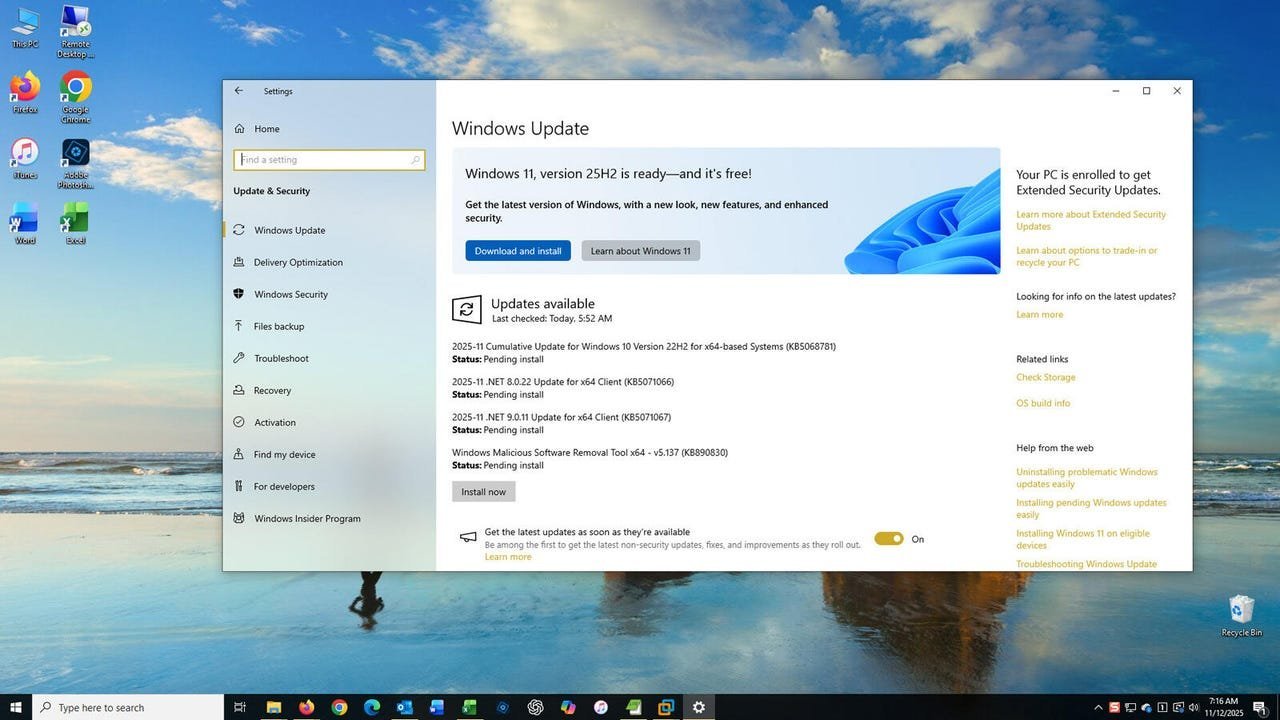
Microsoft’s first major Extended Security Updates (ESU) rollout for Windows 10—anchored by update KB5068781—lands with 66 security fixes across Windows 10 (for ESU-enrolled systems) and Windows 11. Hidden in the patch notes is the story that matters to engineering leaders and IT decision-makers: Windows 10 is now a subscription-grade legacy platform, and defending it is about to get expensive.
This isn’t just a patch. It’s a policy signal.
What the November ESU Drop Delivers
For ESU-enrolled Windows 10 devices, the November update brings three key elements:
Functional fixes for ESU itself
- A bug that incorrectly told ESU-registered users their OS was out of support has been fixed. Windows Update will now accurately reflect ESU enrollment status.
- An out-of-band patch addresses an enrollment failure that blocked some systems from joining ESU via the wizard—critical, because if you can’t enroll, you can’t legally receive post-EOL fixes.
Security coverage: 66 vulnerabilities patched
- The release includes 66 vulnerabilities affecting Windows 10 (ESU) and Windows 11.
- Five are rated critical, and one is a zero-day in the Windows Kernel.
- The zero-day is particularly concerning: kernel-level vulnerabilities are the gateway to privilege escalation—from standard user to SYSTEM or Administrator—opening paths to credential theft, persistence, and lateral movement across networks.
Windows 11 feature updates (not for 10)
- While Windows 10 ESU devices simply get to survive, Windows 11 users receive new features: a revamped Start menu, File Explorer and Taskbar changes, enhancements to Click To Do, and Voice access improvements for Copilot+ PCs.
- This reinforces the divide: Windows 11 is where innovation happens; Windows 10 ESU is where risk is managed.
The update is mandatory and should auto-install, but anyone managing fleets—or sensitive endpoints—knows “should” isn’t good enough. Admins should force verification via Windows Update or their patch management stack.
The Price of Standing Still
The economics of ESU are where the story sharpens for enterprises.
For individual consumers, Microsoft has made ESU surprisingly accessible:
- Roughly $30 flat for coverage, or
- 1,000 Microsoft Rewards points earned via Bing searches, or
- Effectively free via Windows Backup usage, if you:
- Sign in with a Microsoft account
- Backup and sync settings to the cloud
For organizations, the numbers look very different:
- Year 1: $61 per PC
- Year 2: $122 per PC
- Year 3: $244 per PC
- Total: $427 per Windows 10 machine over three years
This is not arbitrary pricing; it’s behavioral economics. The ESU ladder is designed to make inaction hurt more every year. By year three, failing to migrate is not just a security liability—it’s a budget anomaly.
For CIOs, CISOs, and infrastructure leads, this changes the calculus:
- A large estate of 5,000 Windows 10 machines left un-migrated could imply over $2.1 million in ESU costs across three years.
- That money does not buy new capabilities, user experience improvements, or hardware modernization. It buys time—and only for security patches.
In other words: ESU is not a strategy. It’s a containment measure.
Why This Patch Matters for Security Teams
Viewed through a security engineering lens, this ESU milestone exposes three critical dynamics.
Legacy OS as Permanent Attack Surface Windows 10 remains deeply embedded in regulated industries, OT environments, specialized workstations, and hardware-constrained fleets. Kernel-level vulnerabilities on such widely deployed systems offer attackers:
- Reliable privilege escalation primitives
- Paths to bypass EDR or tamper with security tools
- Opportunities to chain with browser/app exploits for full compromise
Every missed ESU patch compounds risk. Every unmanaged Windows 10 box becomes a soft entry point.
Two-Speed Windows: Features vs. Fixes Windows 11 gets UX and AI-oriented enhancements; Windows 10 (ESU) gets only patches. That split matters for security culture:
- No new security UX improvements or platform features for ESU users
- More fragmentation in testing, deployment, and baseline configurations
Security and IT teams must treat ESU Windows 10 as a distinct, constrained platform—not just "Windows, but older."
Operational Complexity for Dev and IT In mixed environments, this first ESU wave is a reminder to:
- Maintain separate baselines for Windows 10 ESU and Windows 11
- Verify ESU enrollment via scriptable checks (e.g., registry, licensing status) instead of UI alone
- Ensure patch management tools (Intune, ConfigMgr, third-party RMM/patch platforms) are explicitly configured to:
- Recognize ESU-eligible machines
- Apply the correct keys/activation mechanisms
- Report non-compliant or non-enrolled endpoints
For developers building internal tools or endpoint agents, assume OS heterogeneity will persist—and test accordingly.
Guidance for Teams Still on Windows 10
If you’re responsible for infrastructure, engineering tooling, or security posture, this first ESU release is the moment to formalize your stance instead of drifting.
Practical steps:
Inventory with intent:
- Identify all Windows 10 machines: where they run, what they do, and why they haven’t moved.
- Classify: can migrate now, can migrate with work, or truly blocked (e.g., hardware/critical app constraints).
Lock down your ESU estate:
- Ensure affected endpoints are properly ESU-licensed and receiving KB5068781.
- Validate enrollment via your management stack instead of trusting the GUI.
- Prioritize patching for exposed roles: internet-facing devices, admin workstations, machines with elevated access.
Design migration, not drift:
- Align ESU timelines with hardware refresh and Windows 11 (or alternative OS) transition.
- For dev and ops teams, treat ESU costs as a forcing function to retire or modernize legacy apps.
Assume adversaries are reading the same patch notes:
- A Windows Kernel zero-day fixed in a high-profile ESU cycle is exactly the kind of bug that will be reverse-engineered.
- Any stragglers not patched—or not in ESU at all—become increasingly attractive.
What This Signals About Microsoft’s Strategy
The first Windows 10 ESU patch does more than close vulnerabilities. It normalizes a pattern:
- Long-term support as a monetized, structured product.
- Security as an ongoing subscription for organizations that resist platform upgrades.
- A clear architectural nudge toward a Windows ecosystem where:
- The "living" branch (Windows 11 and beyond) is where AI, Copilot+, and UX innovation land.
- Legacy branches survive under tight, billable, security-only maintenance.
For technical leaders, the message is blunt but useful: if your stack depends on aging platforms, you will pay—with money, with complexity, or with risk. The November ESU update for Windows 10 is just the first invoice.
Comments
Please log in or register to join the discussion