A flawed Windows 11 update left Task Manager quietly multiplying in the background, degrading performance and eroding trust in a core diagnostic tool. Microsoft’s fix in KB5068861 patches the bug—but the incident underscores deeper concerns about update quality, system observability, and operational resilience for modern Windows fleets.
Microsoft’s Task Manager Glitch Wasn’t Just Annoying—It Was a Warning Shot for Windows Reliability

When Task Manager—the tool you rely on to kill misbehaving processes—refuses to die itself, it stops being a utility and becomes a liability.
That’s effectively what happened to Windows 11 users after installing the optional KB5067036 update released on October 28, 2025. A regression meant that closing Task Manager did not fully terminate taskmgr.exe, leaving invisible background instances running and slowly cannibalizing CPU and memory. For many users, that meant intermittent stutters, hangs, and a creeping sense that something was off, with no obvious culprit.
Microsoft has now shipped a fix as part of the November security update KB5068861. The incident is closed. The questions it raises for developers, IT admins, and SREs managing Windows fleets are not.
Source: BleepingComputer – "Microsoft fixes Windows Task Manager bug affecting performance"
What Actually Broke in Task Manager
The bug manifested after installing the KB5067036 preview update for Windows 11:
- Closing Task Manager with the window’s Close (X) button did not fully terminate the process.
- Reopening Task Manager spawned a new visible instance while previous instances of
taskmgr.exeremained hidden in the background. - Over time, multiple lingering processes consumed resources, causing:
- Noticeable slowdowns
- UI stutters
- CPU hangs or degraded responsiveness in other applications
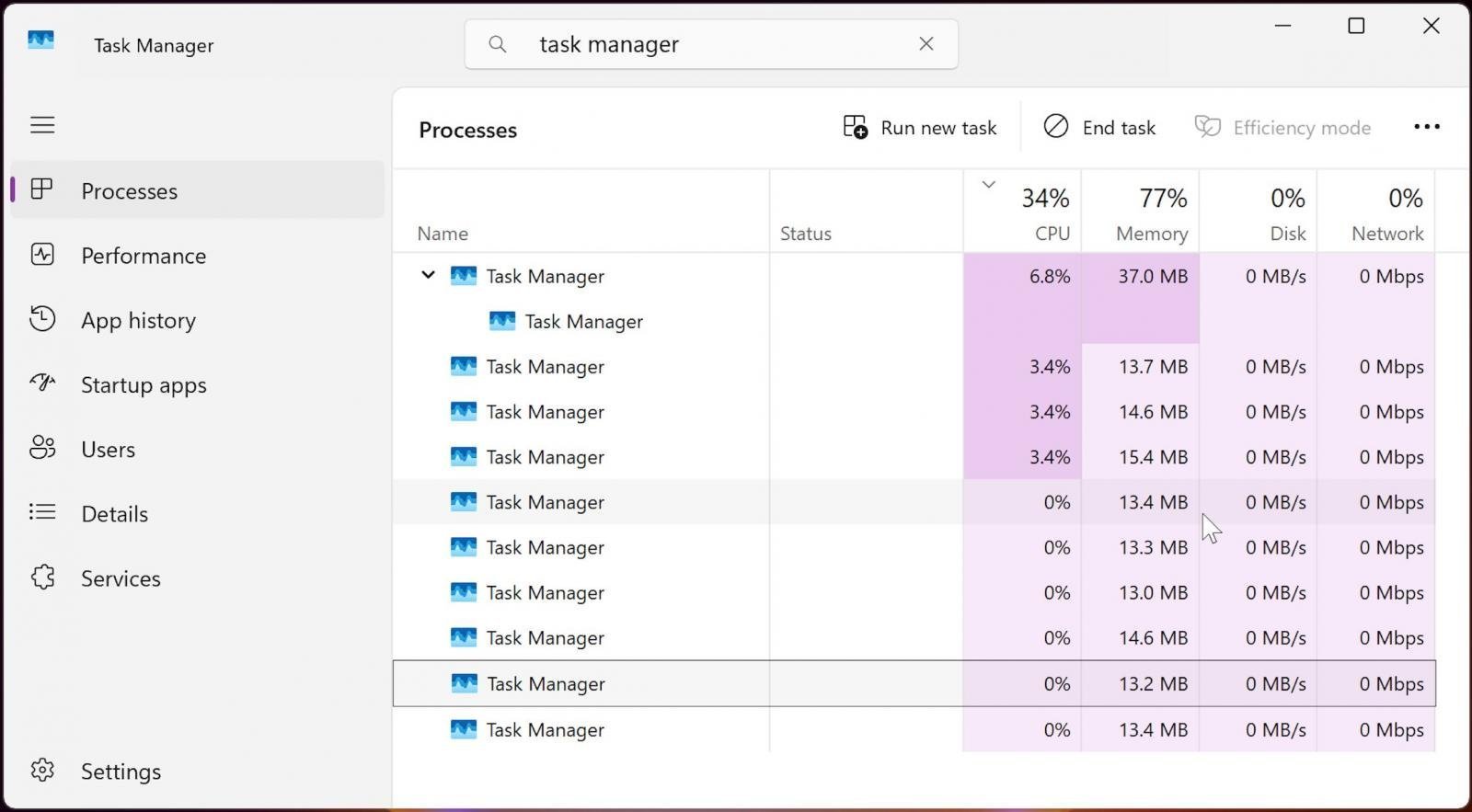
Individually, a single stray Task Manager process is usually harmless. But Task Manager is disproportionately used during periods of perceived system instability: when something’s slow, when CPU spikes, when memory leaks. In those situations, users often open and close it repeatedly, compounding the problem this bug created.
Microsoft acknowledged the issue publicly, documenting that the defect specifically impacted updates “released on or after October 28, 2025 (KB5067036)” and confirming that affected systems could accumulate multiple invisible instances even though no window was visible.
The official fix landed with KB5068861, the November Patch Tuesday release, which also bundles additional security and reliability improvements.
Why This Matters More Than a Minor UI Annoyance
To a casual user, this is a quirky annoyance with a built-in tool. To anyone running Windows in production—or building software that lives on top of it—it’s a flashing indicator of deeper reliability concerns.
1. A Trust Violation in a Core Diagnostic Primitive
Task Manager is foundational:
- It’s the default interface for:
- Inspecting CPU, memory, GPU, and I/O
- Killing stuck applications
- Detecting runaways and malware-like behavior
- It’s used instinctively: when something’s wrong, you hit Ctrl+Shift+Esc.
When the diagnostic tool itself becomes the source of performance issues, the entire support workflow degrades. Helpdesks see noisy signals. Power users misattribute slowdowns. IT teams chase ghosts.
For OS vendors, tools like Task Manager, top, and htop are sacred. Regressions here hurt credibility, fast.
2. Preview Updates Are Bleeding into Production Behavior
This issue was introduced by an optional preview (C-week) update—a channel explicitly meant for early adopters and testers. In practice:
- Many admins and power users deploy previews to get ahead of issues or access fixes early.
- OEMs, images, or internal baselines sometimes absorb previews faster than intended.
When a preview regression meaningfully impacts performance on such a widely used component, it raises questions about gatekeeping:
- Are regressions in critical system tools being isolated and tested with sufficient rigor?
- Are telemetry and staged rollouts tuned to catch behavioral anomalies like process accumulation and phantom UI exits?
For enterprises already wary of “Patch Tuesday roulette,” this does not help.
3. The OS as an Always-On, Continuously Updated Platform
This bug doesn’t exist in isolation. In recent months, Microsoft has:
- Fixed 0x800F081F update errors impacting Windows 11 24H2 since January.
- Resolved issues with the Windows 11 Media Creation Tool (MCT), including on Arm64.
- Acknowledged that an emergency WSUS security update broke hotpatching on some Windows Server 2025 systems.
- Confirmed BitLocker recovery prompts appearing unexpectedly after October 2025 security updates.
Individually: manageable. Collectively: they reinforce the perception that the modern Windows servicing model—fast, continuous, cloud-orchestrated—is straining its safety nets.
For organizations operating at scale, this means:
- Higher validation overhead for each cumulative/preview update.
- More aggressive canary rings and rollback plans.
- A growing gap between what’s “shipped” and what’s “trusted for production.”
The Task Manager bug is small, but symbolically potent: if something this visible slips, what about the subtle stuff you’re not looking at?
Practical Takeaways for Admins and Engineers
If you’re responsible for Windows endpoints or developer machines, here’s what matters operationally.
1. Patch to KB5068861
- Deploy the November 2025 security update (KB5068861) on affected Windows 11 systems.
- Treat it as high priority not only for this bug, but for the broader security fixes it contains.
2. Interim Workaround (If You Can’t Patch Yet)
For environments where change windows are tight or compatibility testing is still underway, Microsoft’s workaround is straightforward:
- Manually end lingering Task Manager processes via another Task Manager instance (if visible) or:
- Use Command Prompt (preferably elevated):
taskkill.exe /im taskmgr.exe /f
This terminates all existing taskmgr.exe processes cleanly.
3. Revisit Your Windows Update Strategy
Use this incident as a forcing function to tighten your servicing model:
- Maintain clearly defined rings:
- Canary: IT/dev devices
- Pilot: representative business users
- Broad: general population once validated
- Treat preview (C/D) updates as genuinely pre-production:
- Only on canary/pilot
- With explicit observability and rollback
- Instrument performance baselines:
- Monitor CPU, memory, and hangs around update rollout windows
- Flag anomalies like unexpected process counts or lingering system utilities
For large fleets, this is table stakes.
Lessons for the People Building the Tools
For developers and engineers inside and outside Microsoft, the Task Manager saga is a compact case study in platform reliability.
1. UX Bugs Can Have Systems Consequences
A close button that doesn’t fully close is not just a UI defect. In a resource-sensitive environment, it’s a systems bug:
- Any long-lived background process risks leaks, contention, and unpredictable tail latencies.
- For critical utilities, bugs are multiplicative: users will repeatedly invoke the broken behavior.
Takeaway: treat lifecycle management (start/stop/cleanup) as a first-class test surface, especially for diagnostics.
2. Guardrails for System Utilities Need to Be Ruthless
Core tools like Task Manager should have:
- Extra regression tests around:
- Process termination
- Handle and thread cleanup
- Startup/teardown loops
- Canary/telemetry signals that specifically watch for:
- Multiple concurrent instances
- CPU and memory footprint deviations
If you’re building internal tooling for your org (observability dashboards, admin consoles, CLI utilities), the same standard should apply. Your users will lean on these tools when things are already broken—failure here amplifies outages.
3. Communication Matters (And Microsoft Got Part of This Right)
To their credit, Microsoft:
- Rapidly acknowledged the issue.
- Published concrete mitigation steps.
- Rolled the fix into the next scheduled security release.
For technical audiences, this pattern is increasingly non-negotiable:
- Fast, transparent incident notes
- Clear scoping: who’s affected, which builds, which KBs
- Actionable guidance and workarounds
Vendors who treat regressions as part of a mature, observable lifecycle—not as embarrassments to bury—will maintain developer trust longer.
When the Debugger Becomes the Bug
It’s tempting to treat the Task Manager issue as a minor hiccup already made irrelevant by KB5068861. But for teams running Windows as critical infrastructure—from developer workstations to VDI farms to production servers—the story lands differently.
A core diagnostic tool misbehaving due to an official update is a sharp reminder that:
- Observability must extend to the platform itself.
- Update policies must be engineered, not improvised.
- Even the "safe" tools need safeguards.
In an era where operating systems are effectively rolling releases under enterprise constraints, small regressions become valuable signals. This one, fortunately, is easy to patch. The smarter move is to treat it as justification to harden your pipelines, your telemetry, and your assumptions about what “just works” on Windows.

Comments
Please log in or register to join the discussion