GreyNoise reports an unprecedented 500% spike in reconnaissance scans targeting Palo Alto Networks GlobalProtect and PAN-OS portals, with over 1,285 suspicious IPs detected in a single day. This surge mirrors pre-attack patterns previously seen before major zero-day exploits, raising alarms across enterprise security teams. Simultaneously, threat actors are aggressively exploiting a years-old Grafana vulnerability, highlighting the relentless pressure on network defenses.
Reconnaissance Surge Targets Palo Alto Networks: Prelude to Attack?
Cybersecurity teams are on high alert following a massive, coordinated surge in reconnaissance activity targeting Palo Alto Networks devices. According to threat intelligence firm GreyNoise, scans probing Palo Alto GlobalProtect VPN gateways and PAN-OS management interfaces skyrocketed by 500%, culminating in over 1,285 unique suspicious IP addresses detected on October 3rd alone. This dwarfs the typical baseline of fewer than 200 daily scanning IPs.
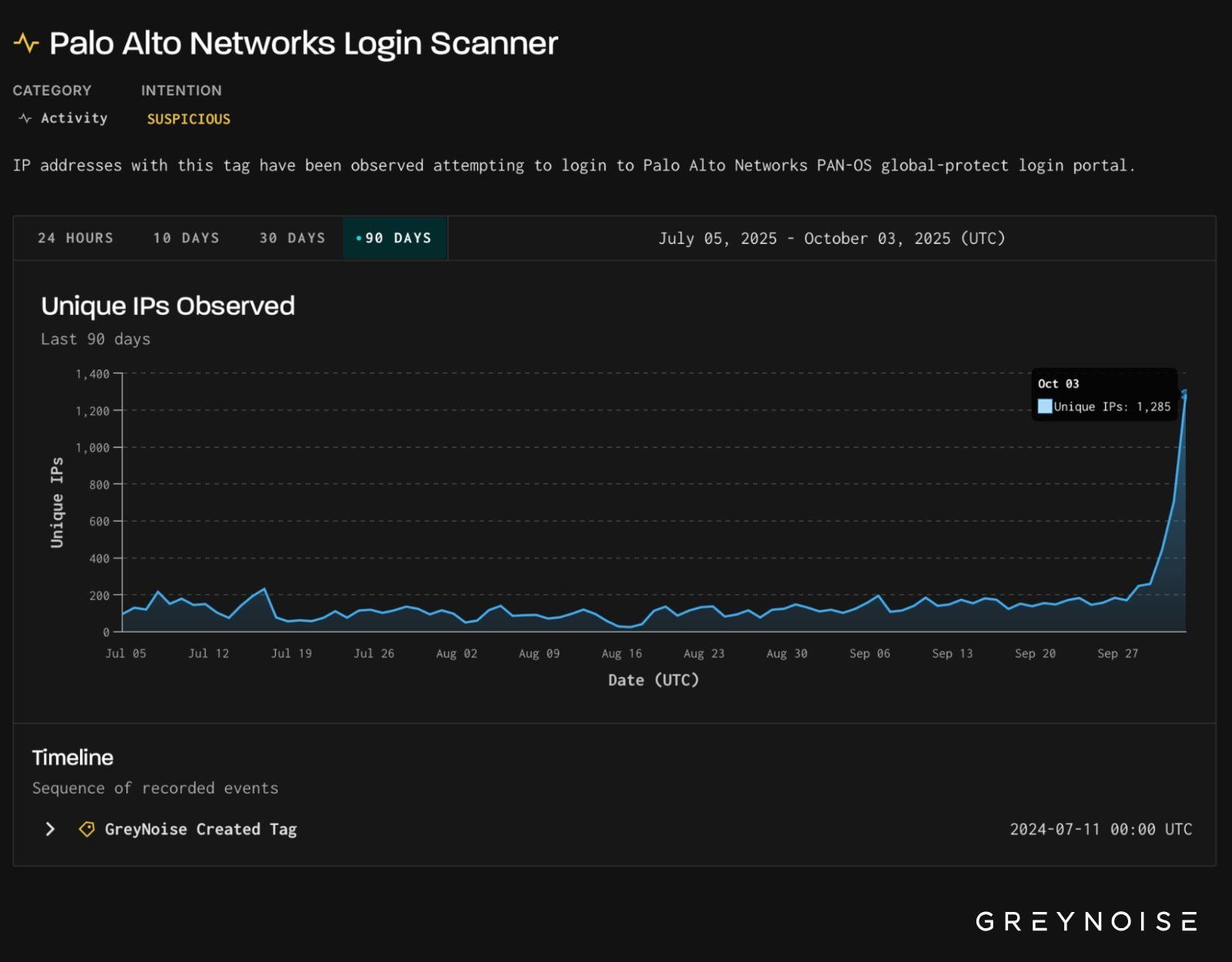 Palo Alto scanning activity (Source: GreyNoise)
Palo Alto scanning activity (Source: GreyNoise)
"Nearly all activity was directed at GreyNoise’s emulated Palo Alto profiles... suggesting the activity is targeted in nature, likely derived from public or attacker-originated scans fingerprinting Palo Alto devices," GreyNoise stated. Geolocation data revealed most scanning IPs originated in the U.S., with significant clusters in the U.K., Netherlands, Canada, and Russia. Researchers identified two distinct activity clusters: one heavily focused on U.S. targets and another concentrating on Pakistan.
Why This Signals Danger: The Reconnaissance-Attack Nexus
This pattern is deeply concerning because large-scale, targeted scanning often precedes weaponized attacks. GreyNoise has documented this correlation previously:
- Cisco ASA Precedent: Weeks before the recent Cisco ASA zero-day (CVE-2024-20359) exploitation became public, GreyNoise warned of similar scanning spikes targeting those devices.
- Zero-Day Indicator: Scans help attackers identify vulnerable instances for newly discovered (zero-day) or recently patched (n-day) flaws. While GreyNoise notes the Palo Alto link is currently less definitive than the Cisco case, the scale and specificity demand vigilance.
- 91% Suspicious: GreyNoise classified the vast majority (91%) of the Palo Alto-focused IPs as "suspicious," with an additional 7% tagged as overtly "malicious."
Grafana Under Fire: Old Vulnerability, Renewed Assaults
Simultaneously, GreyNoise observed a separate campaign exploiting CVE-2021-43798, a critical path traversal vulnerability in Grafana dashboards patched in December 2021. On September 28th, 110 unique malicious IPs, primarily from Bangladesh, launched attacks targeting Grafana instances, especially in the U.S., Slovakia, and Taiwan.
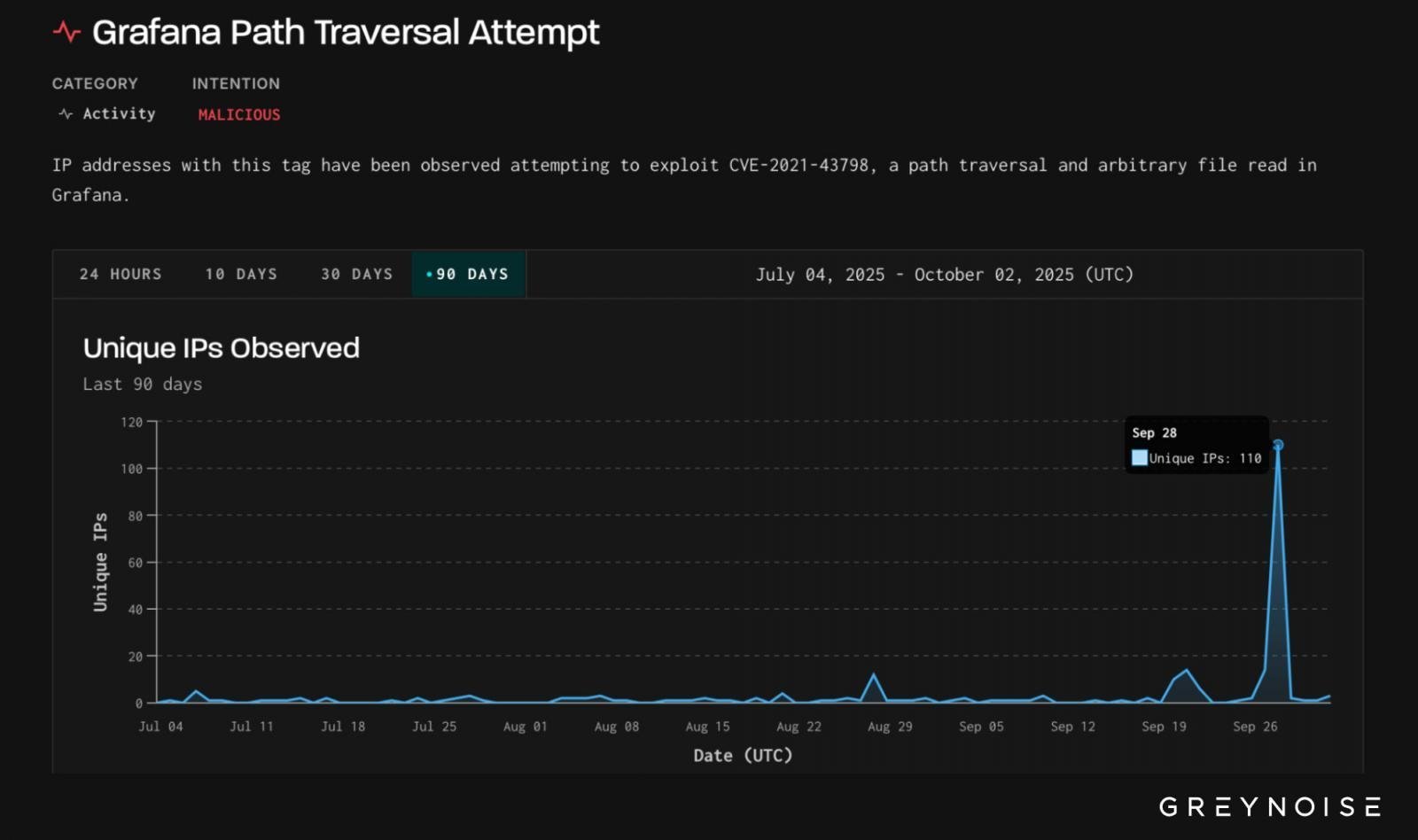 Observed Grafana exploitation attempts (Source: GreyNoise)
Observed Grafana exploitation attempts (Source: GreyNoise)
"Administrators should ensure Grafana instances are patched against CVE-2021-43798 and block the identified malicious IP addresses," GreyNoise urged. "Check logs for evidence of path traversal requests attempting to access sensitive files."
The Imperative for Defenders: Patch, Monitor, Block
- Palo Alto Administrators:
- Monitor Aggressively: Scrutinize logs for unusual authentication attempts or scans targeting
/global-protect/and/php/login.phpendpoints. - Verify Patches: Ensure all Palo Alto devices (firewalls, Panorama) are running the latest PAN-OS versions, especially patches for critical vulnerabilities.
- Harden Configurations: Enforce strong authentication (MFA), restrict management interface access, and review security policy rules.
- Monitor Aggressively: Scrutinize logs for unusual authentication attempts or scans targeting
- Grafana Administrators:
- Patch Immediately: If running Grafana versions 8.0.0-beta1 through 8.3.0, upgrade immediately to mitigate CVE-2021-43798.
- Block Malicious IPs: Implement blocklists for the 110 IPs identified by GreyNoise.
- Audit Logs: Search logs for requests attempting paths like
/public/plugins/<plugin-id>/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f/etc/passwd.
This surge in hostile reconnaissance against critical network infrastructure serves as a stark reminder that scanning activity is rarely benign noise. It's the digital equivalent of attackers casing a neighborhood – and Palo Alto Networks devices are currently squarely in their sights.
Source: Analysis based on GreyNoise research reported by BleepingComputer (October 4, 2025).

Comments
Please log in or register to join the discussion