Hackers infiltrated a bank's network by physically planting a 4G-enabled Raspberry Pi on an ATM switch, creating an invisible backdoor for lateral movement and fraud attempts. The UNC2891 group leveraged custom anti-forensic techniques to mimic legitimate processes while attempting to deploy ATM-spoofing malware. This sophisticated hybrid attack underscores critical vulnerabilities in financial institutions' physical and digital security postures.

In a bold hybrid attack blending physical intrusion with digital sophistication, the UNC2891 cybercrime group (aka LightBasin) planted a covert 4G-equipped Raspberry Pi inside a bank's network—directly connected to an ATM switch—in a failed attempt to orchestrate fraudulent cash withdrawals. The device created an invisible cellular backdoor that bypassed perimeter defenses, enabling persistent remote access while avoiding traditional network monitoring.
Security firm Group-IB discovered the intrusion during an investigation of suspicious network activity. The Raspberry Pi, likely installed via physical access to a bank branch or with insider assistance, hosted the open-source TinyShell backdoor. This established a command-and-control (C2) channel over mobile data, allowing attackers to:
- Move laterally to the Network Monitoring Server with extensive data center access
- Pivot to the Mail Server (retaining persistence even after device removal)
- Deploy backdoors named 'lightdm' to mimic Linux's legitimate LightDM display manager
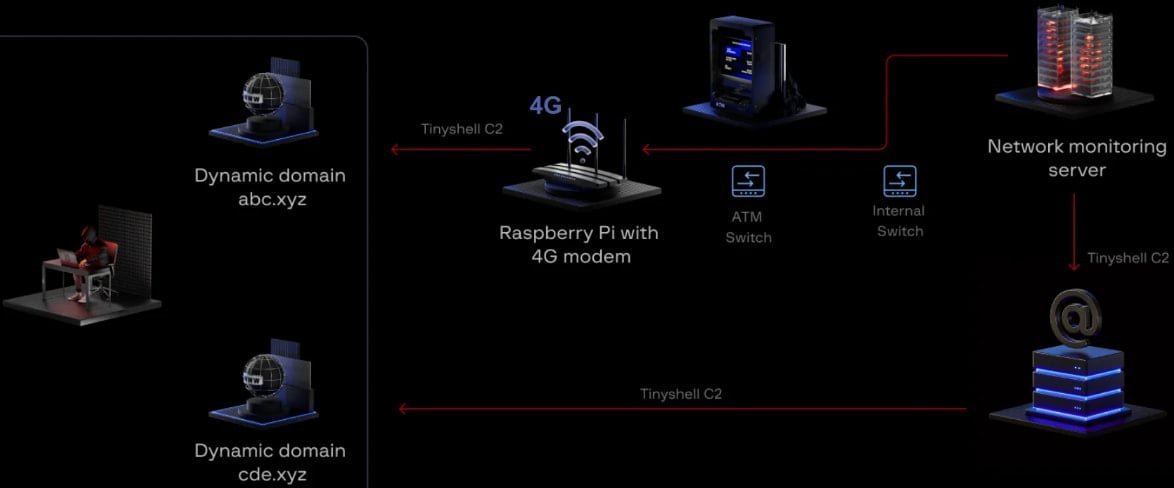 Overview of LightBasin's attack chain leveraging the Raspberry Pi pivot point (Source: Group-IB)
Overview of LightBasin's attack chain leveraging the Raspberry Pi pivot point (Source: Group-IB)
The attackers employed advanced anti-forensic techniques, mounting tmpfs and ext4 filesystems over /proc/[pid] paths to obscure malicious process metadata—a tactic designed to evade common forensic tools. Network telemetry revealed beaconing every 600 seconds to the Raspberry Pi on port 929, confirming its role as a critical pivot host.
LightBasin, active since 2016, has a documented history of targeting financial infrastructure. Their arsenal includes the Unix kernel rootkit Caketap, which manipulates Payment Hardware Security Module (HSM) responses to authorize fraudulent transactions. While the group failed to deploy Caketap in this incident, their methodology reveals alarming trends:
- Physical-Digital Convergence: Attackers bypassed network segmentation by bridging air-gapped systems with cellular-connected hardware
- Persistence Engineering: Multiple persistence mechanisms ensured operational continuity even after device discovery
- Process Camouflage: Legitimate system components were cloned to avoid detection
"This attack demonstrates how threat actors are creatively combining physical access with advanced evasion techniques," notes Group-IB's report. Financial institutions must reassess defenses against such hybrid threats, including:
- Enhanced physical security for network closets and ATM access points
- Network behavior analytics to detect irregular outbound cellular traffic
- Rigorous monitoring of
/procmodifications and process impersonation - Segmentation policies treating internal network traffic with zero-trust principles
The failed heist serves as a critical reminder: as financial networks become more interconnected, the attack surface expands beyond digital perimeters into the physical realm. Defenders must now secure not just data packets—but every unauthorized Raspberry Pi hidden in a server rack.
Source: Group-IB via BleepingComputer

Comments
Please log in or register to join the discussion