Unencrypted DNS queries expose your online activity to prying eyes, especially on public Wi-Fi, but Android's Private DNS mode offers a simple fix. This guide walks through enabling it on modern devices and explains the privacy gains. In an era of rising cyber threats, encrypting your DNS is a crucial step for tech-savvy users.
Secure Your Android Browsing: How to Enable Private DNS and Why It Matters Now
Every online action on your Android device starts with a DNS query, translating user-friendly domain names like zdnet.com into IP addresses that direct your browser or app to the right destination. Without this system, navigating the web would be a tedious exercise in memorizing numeric strings. Yet, traditional DNS operates in plain text, laying bare your browsing habits to anyone on the same network—be it your ISP, a coffee shop snoop, or a malicious actor.
This vulnerability has real-world implications. On public networks, unencrypted queries can reveal sensitive searches or work-related URLs, potentially compromising privacy or security. Android's Private DNS mode addresses this by encrypting these queries using DNS over TLS (DoT), making interception futile. For developers and engineers who rely on mobile devices for secure access to tools like CMS platforms or cloud services, this feature isn't just convenient—it's essential.
The Risks of Unencrypted DNS
Consider a developer testing an app on a public Wi-Fi hotspot. A DNS query for a proprietary server could be sniffed, exposing internal infrastructure. Standard DNS lacks encryption, sending data as clear text packets that network eavesdroppers can capture and analyze. This isn't theoretical; tools like Wireshark make such interception straightforward for skilled adversaries.
Private DNS changes the game by wrapping queries in TLS encryption, similar to HTTPS for web traffic. Providers like Cloudflare, Google, and Quad9 support DoT, ensuring queries remain private even in transit. Beyond privacy, it bolsters security against DNS spoofing attacks, where attackers redirect traffic to malicious sites—a common vector in phishing schemes targeting tech professionals.
Enabling Private DNS on Android 11 and Later
Starting with Android 11, Google streamlined Private DNS implementation but shifted to app-based management for broader compatibility. The recommended tool is Cloudflare's 1.1.1.1 + WARP app, available on the Google Play Store.
- Install the App: Download and install '1.1.1.1 + WARP' from the Play Store.
- Activate WARP: Launch the app and toggle the 'Disconnected' slider to connect. This enables encrypted DNS routing through Cloudflare's secure servers.
- Re-enabling if Needed: If disabled, search for the app in the Play Store and tap 'Open'—it's not listed in the app drawer when inactive. A persistent notification allows quick access when running.
This method integrates seamlessly with Android's networking stack, providing system-wide encryption without manual configuration. For those wary of third-party apps, note that WARP is lightweight and focuses solely on DNS security.
For Older Android Versions (10 and Below)
Devices on Android 10 or earlier use built-in settings for a more direct approach:
Access Settings: Open the Settings app and navigate to 'Network & internet'. On Samsung devices, it's under 'More Connection Settings'.
Locate Private DNS: Scroll to the 'Private DNS' option. If not visible, use the search bar in Settings.
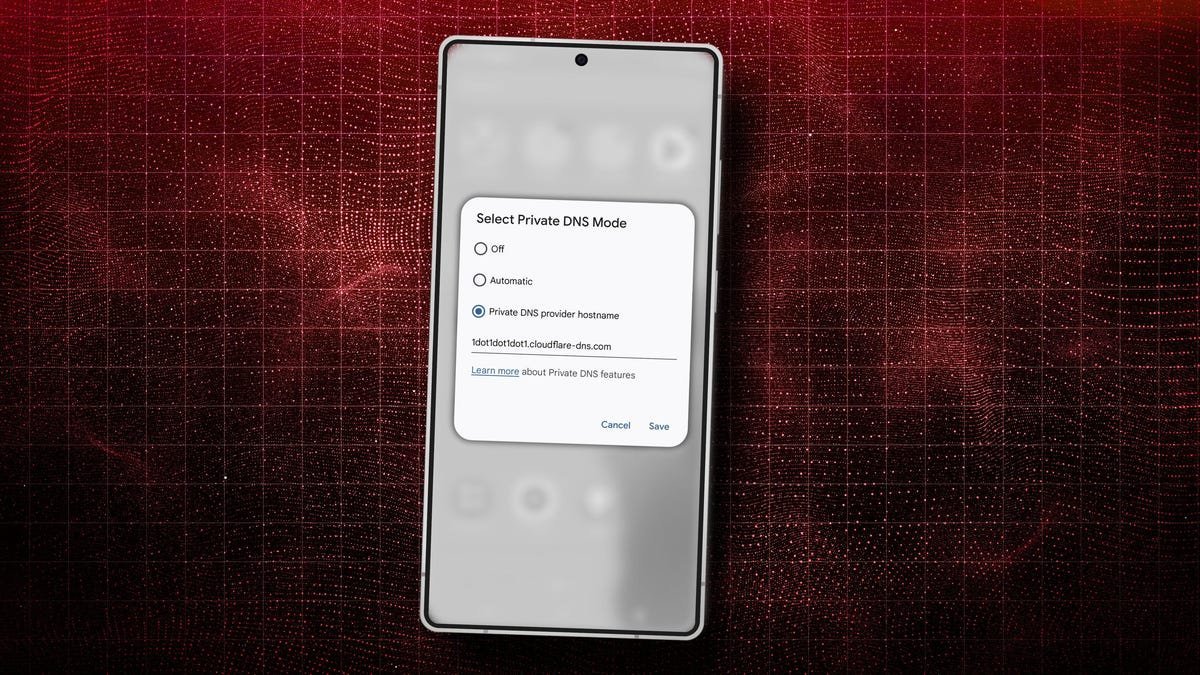
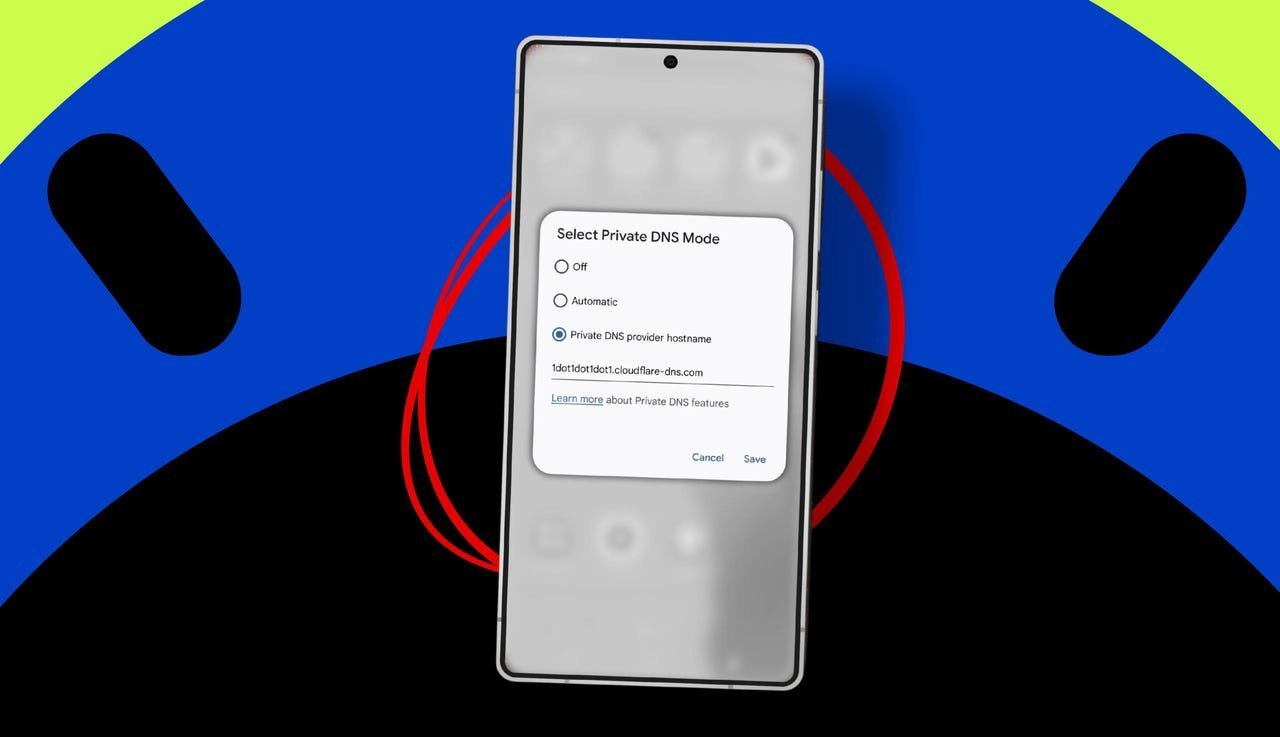
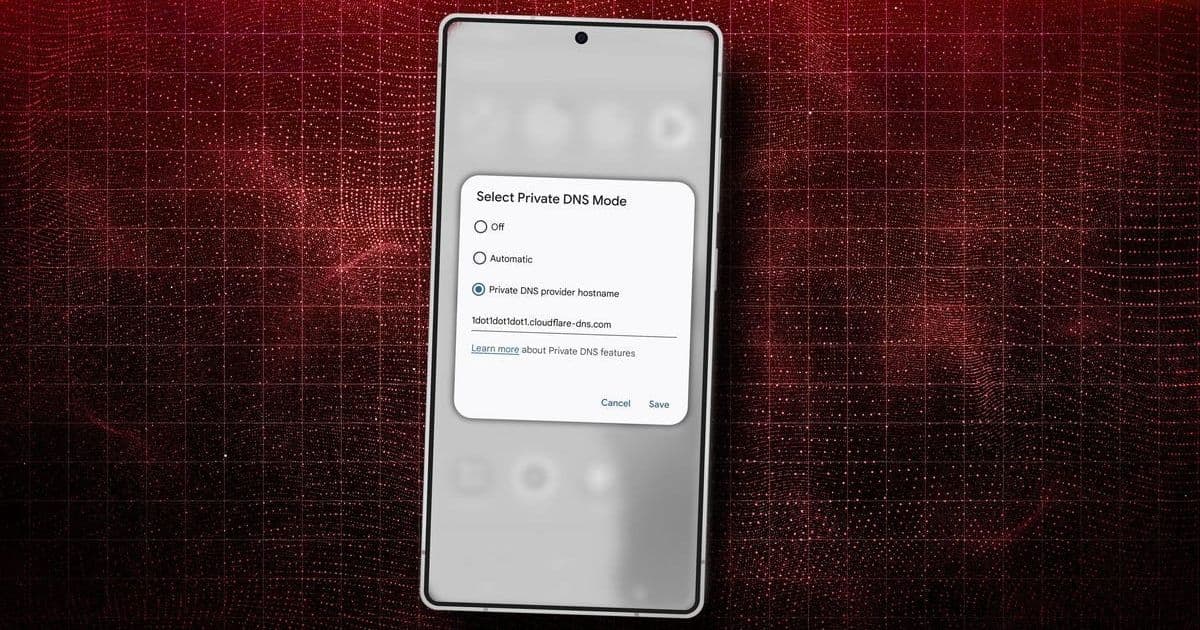
Select Provider: Choose 'Private DNS provider hostname' and enter a secure hostname, such as:
- Cloudflare:
1dot1dot1dot1.cloudflare-dns.com(recommended for speed and malware blocking). - Google:
dns.google. - Quad9:
dns.quad9.net.
Tap 'Save' to apply. For automatic fallback, select 'Automatic', though manual selection offers more control.
- Cloudflare:
To verify, visit http://1.1.1.1/help in your browser; 'Using DNS over TLS (DoT)' should read 'Yes'.
Why Developers Should Prioritize This
In the mobile development ecosystem, where apps interact with diverse APIs and services, DNS security directly impacts reliability. Unencrypted queries can lead to man-in-the-middle attacks, disrupting development workflows or leaking sensitive data during testing. By enabling Private DNS, engineers ensure a more robust foundation for secure coding practices, aligning with industry standards like those from OWASP for mobile security.
Moreover, as 5G and edge computing expand, the attack surface grows. Encrypted DNS mitigates risks from network-level threats, allowing developers to focus on innovation rather than defense. Providers like Cloudflare add value through features like DNS filtering, which blocks malicious domains proactively—vital for teams handling untrusted networks.
In a landscape where data breaches cost millions and privacy regulations like GDPR loom large, enabling Private DNS is a low-effort, high-impact measure. It's a reminder that even foundational internet protocols deserve scrutiny, empowering users to reclaim control over their digital footprint.
Comments
Please log in or register to join the discussion