The notorious ShinyHunters collective has launched a public extortion portal leaking stolen Salesforce data from companies including Google, FedEx, and Marriott. Threat actors demand ransoms under threat of full data exposure by October 10, while separately pressuring Salesforce to pay for global customer protection. This coordinated campaign exploits voice phishing and OAuth vulnerabilities, impacting billions of records across major corporations.

A coalition of threat actors identifying as "Scattered Lapsus$ Hunters"—comprising members of ShinyHunters, Scattered Spider, and Lapsus$—has escalated their ongoing Salesforce exploitation campaign by launching a dedicated data leak site targeting 39 major enterprises. The site, revealed this week, displays stolen data samples from victims including FedEx, Disney/Hulu, Home Depot, Marriott, Google, Cisco, and Toyota, with an October 10 deadline for ransom payments to prevent full disclosure.
"All of them have been contacted long ago, they saw the email because I saw them download the samples multiple times. Most of them chose to not disclose and ignore," ShinyHunters told BleepingComputer. The group's leak portal warns organizations: "We highly recommend a decision-maker to get involved as we are presenting a clear and mutually beneficial opportunity to resolve this matter."
 ShinyHunters' Salesforce leak portal listing victim organizations (Source: BleepingComputer)
ShinyHunters' Salesforce leak portal listing victim organizations (Source: BleepingComputer)
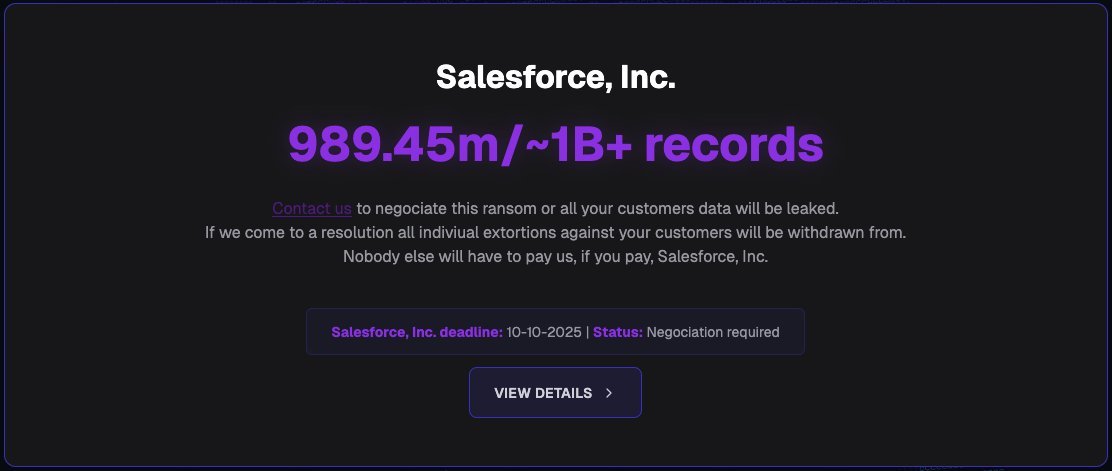
In an unprecedented move, attackers separately demanded a ransom payment directly from Salesforce itself, threatening to expose approximately 1 billion records containing personal information unless the company pays to shield all impacted customers. "Should you comply, we will withdraw from any active or pending negotiation individually from your customers," the group stated, while also threatening to facilitate GDPR-related lawsuits against Salesforce for alleged security failures.
Attack Methodology and Scale
The campaign exploits voice phishing (vishing) tactics to trick employees into connecting malicious OAuth applications to corporate Salesforce instances. Once authorized, attackers exfiltrate databases and leverage the data for extortion. Security firm Mandiant tracks these activities under cluster UNC6395, noting the group's use of stolen OAuth tokens from Salesloft's Drift AI chat integration to harvest sensitive credentials—including AWS keys and Snowflake tokens—from Salesforce environments.
ShinyHunters claims the Salesloft vector alone compromised 760 companies and resulted in the theft of 1.5 billion records, with victims including Palo Alto Networks, Cloudflare, Zscaler, and BeyondTrust. A dedicated leak site for these breaches is reportedly scheduled for launch on October 10.
Implications for Enterprise Security
This campaign highlights critical vulnerabilities in third-party integrations and identity management:
- OAuth Abuse: Malicious apps bypass traditional security controls by exploiting legitimate authentication protocols
- Supply Chain Exposure: Compromised SaaS integrations (like Salesloft Drift) create cascading breaches
- Extortion Economics: Centralized ransom demands to platform providers represent a dangerous escalation
Security teams should immediately audit Salesforce OAuth connections, implement phishing-resistant MFA, and monitor for suspicious token activity. The coordinated naming of high-profile victims suggests meticulous targeting of enterprises with maximum reputational leverage—a trend likely to intensify without fundamental shifts in third-party risk management.
As the October 10 deadline looms, organizations face not just data exposure but a watershed moment in cloud supply chain accountability. Whether Salesforce negotiates with attackers remains unknown, but the incident irrevocably demonstrates that platform-level breaches have graduated from theoretical risk to active battlefield.
Source: BleepingComputer

Comments
Please log in or register to join the discussion