The notorious ShinyHunters extortion group is systematically breaching major corporations including Qantas, LVMH, and Allianz Life through sophisticated voice phishing attacks targeting Salesforce CRM systems. Security researchers confirm these intrusions exploit social engineering to hijack OAuth connections, with stolen data now being used for private extortion attempts. The campaign reveals complex overlaps with Scattered Spider hackers and highlights critical third-party security blind spots
ShinyHunters Weaponizes Vishing in Global Salesforce CRM Assault

A coordinated attack campaign exploiting voice phishing (vishing) has compromised customer data at aviation giant Qantas, luxury conglomerate LVMH (including subsidiaries Louis Vuitton and Dior), insurance leader Allianz Life, and sportswear titan Adidas. Google's Threat Intelligence Group (GTIG) first identified the threat actor UNC6040—now confirmed as the ShinyHunters collective—using meticulously crafted social engineering to breach Salesforce CRM instances.
The OAuth Hijack Playbook
The attacks follow a consistent pattern: Threat actors impersonate IT support staff via phone calls, directing targeted employees to Salesforce's connected app setup page. Victims are instructed to enter a "connection code" that links a malicious version of Salesforce's Data Loader OAuth app to their corporate environment. In some cases, rebranding the malicious component as "My Ticket Portal" increased deception efficacy.
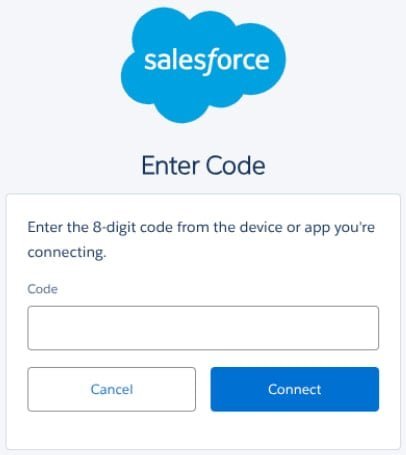
"The platform itself was not compromised, and the issues described are not due to any known vulnerability in our platform," Salesforce told BleepingComputer, emphasizing that compromised credentials stemmed purely from social engineering. GTIG notes attackers supplemented vishing with credential harvesting via fake Okta login pages.
Attribution Chaos and Criminal Synergy
The breaches initially confused researchers due to overlapping tactics with Scattered Spider (UNC3944), known for full network takeovers and ransomware. Evidence now points to ShinyHunters specializing in data-theft extortion targeting specific cloud platforms—though with alarming connections:
- Operational Synchronization: Both groups simultaneously target aviation, retail, and insurance sectors
- Personnel Overlap: Ties to defunct Lapsus$ group, with recent Scattered Spider arrests including former Lapsus$ members
- Extortion-as-a-Service Model: ShinyHunters may act as brokers, selling data for other threat actors
Allan Liska of Recorded Future noted: "The overlapping TTPs between known Scattered Spider and ShinyHunters attacks indicate likely some crossover between the two groups." Private extortion emails from "ShinyHunters" have already been dispatched to victim organizations, threatening data leaks reminiscent of their Snowflake campaign if ransoms go unpaid.
Mitigation Imperatives for Salesforce Customers
Salesforce urges immediate implementation of six critical defenses:
- Enforce Trusted IP Ranges for login restrictions
- Apply Strict Least Privilege for application permissions
- Mandate MFA universally
- Restrict and audit Connected App usage
- Deploy Salesforce Shield for advanced monitoring
- Designate dedicated Security Contacts for incident response
# Example Critical OAuth Permission Review
Administrators should regularly audit:
- Apps with "Full Access" or "Manage Data" scopes
- Unused/inactive integrations
- Apps bypassing IP restrictions or MFA
This campaign underscores a brutal reality: Third-party SaaS platforms are now primary attack surfaces. As ShinyHunters evolves its collaboration model, enterprises must treat CRM systems as critical infrastructure—not just business tools. The absence of public leaks suggests extortion negotiations are ongoing, but history shows ShinyHunters’ patience is finite. When deadlines expire, customer data floods the dark web in torrents.
Source: BleepingComputer

Comments
Please log in or register to join the discussion