A sophisticated new Endpoint Detection and Response (EDR) evasion tool, evolving from RansomHub's 'EDRKillShifter,' is being wielded by at least eight ransomware groups to disable security products on compromised systems. The tool leverages obfuscated binaries and stolen certificates to execute 'bring your own vulnerable driver' (BYOVD) attacks, targeting giants like Microsoft Defender and SentinelOne. Sophos researchers warn this signals a dangerous trend of collaborative development among cybe

In a stark escalation of the ransomware arms race, security researchers at Sophos have uncovered a highly advanced Endpoint Detection and Response (EDR) killer tool being actively deployed by eight prominent ransomware gangs. This tool, an evolution of the notorious 'EDRKillShifter' developed by RansomHub, enables attackers to systematically dismantle security defenses, clearing the path for payload deployment, privilege escalation, lateral movement, and network-wide encryption. Its adoption across groups like Blacksuit, Medusa, Qilin, and Crytox underscores a fragmented yet coordinated threat landscape where even rivals share tools to maximize chaos.
How the EDR Killer Operates: Obfuscation and Kernel Exploits
At its core, the tool employs a heavily obfuscated binary that self-decodes during runtime, injecting itself into legitimate applications to evade initial detection. Once active, it hunts for a digitally signed driver—often using stolen or expired certificates—with a random five-character name hardcoded into its executable. As illustrated below, this driver masquerades as trusted software, such as CrowdStrike's Falcon Sensor, to avoid suspicion.
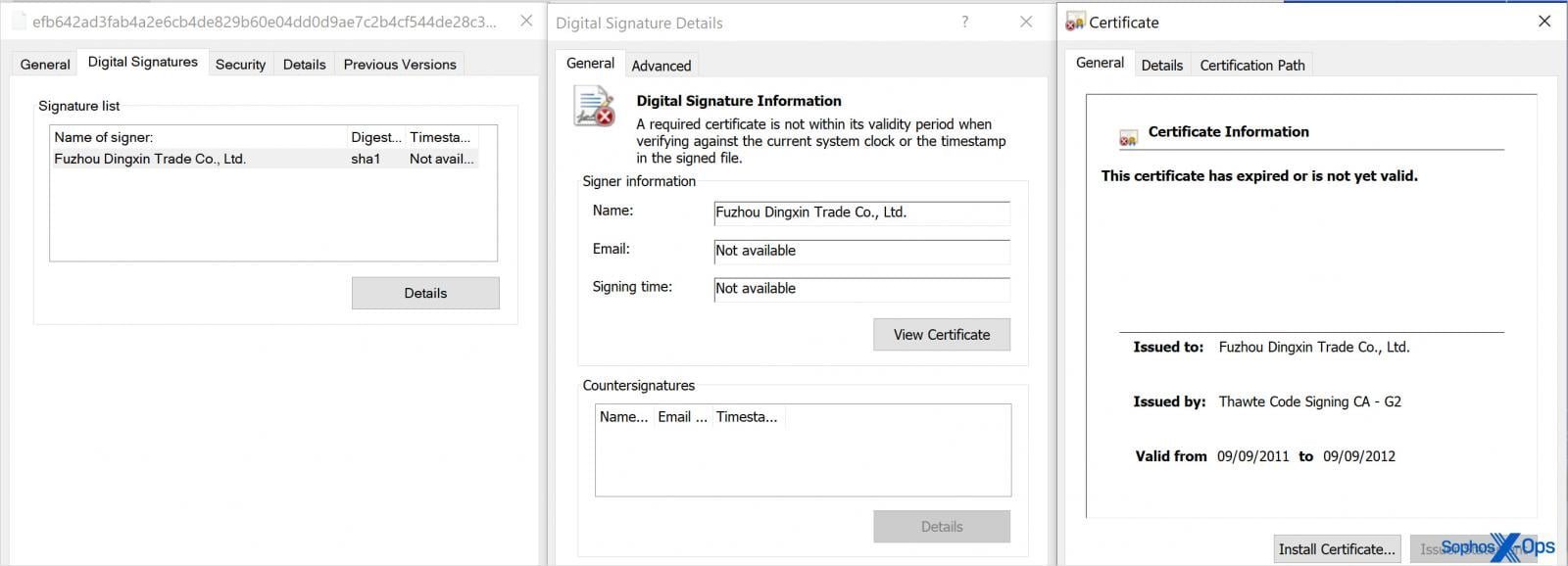 Stolen or expired certificates allow the malicious driver to appear legitimate, a critical enabler for the BYOVD attack. Source: Sophos
Stolen or expired certificates allow the malicious driver to appear legitimate, a critical enabler for the BYOVD attack. Source: Sophos
Upon loading the driver into the kernel, the tool gains the elevated privileges necessary for a BYOVD attack. This technique directly targets and terminates processes and services tied to leading security vendors, including Sophos, Microsoft Defender, Kaspersky, Symantec, Trend Micro, SentinelOne, Cylance, McAfee, F-Secure, HitmanPro, and Webroot. By neutralizing these defenses, ransomware operators can operate unimpeded, turning compromised systems into launchpads for widespread network infiltration.
A Collaborative Underworld: Shared Frameworks, Custom Builds
Sophos emphasizes that this isn't a case of a single leaked binary being reused. Instead, each ransomware group employs a distinct build of the proprietary tool, all packed with HeartCrypt and tailored to their specific targets. This points to a collaborative development framework where knowledge and code are exchanged among gangs, blurring lines between competitors. Christopher Budd, Director of Threat Research at Sophos, noted in the report:
"The consistency in techniques—like BYOVD and certificate abuse—across variants suggests a shared blueprint. It's not theft; it's a business model built on mutual escalation."
This pattern mirrors earlier threats like AuKill (used by Medusa and LockBit) and FIN7's AvNeutralizer, sold to groups like BlackBasta and BlackCat. Such tools commoditize EDR evasion, lowering barriers for less sophisticated actors and amplifying the scale of attacks. For defenders, the implications are dire: signature-based detection is futile against constantly evolving, custom-packed binaries.
Why This Matters: The Shifting Battlefield of Cyber Defense
Ransomware groups are no longer lone wolves but interconnected syndicates refining shared arsenals. The proliferation of this EDR killer signals a shift toward offensive innovation, where disabling security tools is as prioritized as encryption. Enterprises relying solely on traditional AV/EDR solutions face heightened risk; Sophos advises layering behavioral analytics, certificate monitoring, and kernel-level protection to detect driver-based exploits. As attackers refine collaboration, the defense must pivot to threat-hunting and intelligence-sharing—turning the criminals' tactics against them.
The emergence of such tools also highlights the critical role of software supply chain integrity. Expired or stolen certificates, as exploited here, remain a weak link, urging vendors to adopt stricter validation and revocation mechanisms. For now, defenders can access indicators of compromise via Sophos' GitHub repository to bolster detection. In this relentless cat-and-mouse game, vigilance and adaptation are the only constants. As one researcher starkly put it: "When ransomware gangs collaborate, the entire internet becomes their testing ground."
Source: Analysis based on Sophos research reported by BleepingComputer.

Comments
Please log in or register to join the discussion