A former Xbox 360 engineer reveals a critical CPU design flaw involving speculative execution and a custom prefetch instruction, years before Meltdown and Spectre emerged. This bug, which caused mysterious crashes by violating cache coherency, underscores the enduring risks of performance optimizations in hardware.
Long before Meltdown and Spectre sent shockwaves through the tech industry, a similar vulnerability lurked in the heart of the Xbox 360’s CPU. Bruce Dawson, a former Microsoft engineer who spearheaded the console’s CPU development, recently detailed his discovery of a design flaw that exploited speculative execution—a revelation that foreshadowed modern processor security crises.
The Setup: A Performance Gamble
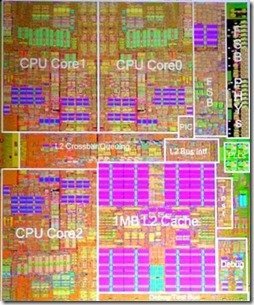
At the core of the Xbox 360 lay a triple-core PowerPC processor, manufactured by IBM, with a shared 1MB L2 cache. To combat high memory latencies, engineers added a custom instruction: xdcbt. Unlike the standard dcbt prefetch, xdcbt fetched data directly from RAM into the L1 cache, bypassing the L2. This avoided polluting the shared cache with transient data, boosting performance—but at a cost. By skipping the L2, xdcbt violated the MESI cache-coherency protocol, risking inconsistent memory views across cores if multiple threads accessed the same data.
"Memory prefetched with
xdcbtis toxic," Dawson writes. "If written by another core before being flushed, two cores have different views of memory with no guarantee of convergence."
The Bug: When Prefetch Goes Rogue
Dawson first encountered the issue when a game using his optimized memory-copy routine—which conditionally employed xdcbt—began crashing mysteriously. Heap corruption appeared in dumps, but the root cause was elusive. He traced it to xdcbt prefetching slightly beyond buffer boundaries, inadvertently pulling adjacent heap metadata into the L1 cache. This created "toxic" cache lines that, when modified by other cores, caused incoherent memory states and hard-to-diagnose failures.
A fix seemed straightforward: ensure xdcbt never prefetched past the buffer end. But after patching the code, crashes resurfaced—even without explicit xdcbt usage. This led Dawson to a chilling realization.
The Spectre Connection: Speculative Execution Unleashed
The Xbox 360’s in-order CPU relied heavily on branch prediction to mitigate pipeline stalls. Dawson hypothesized that mispredicted branches could speculatively execute xdcbt instructions—and once initiated, these prefetches couldn’t be canceled. Even if the branch was corrected, the damage was done: a rogue xdcbt could pull any memory into an incoherent state based on transient register values.
"The branch predictor would sometimes cause
xdcbtinstructions to be speculatively executed... identical to really executing them," Dawson explains. "Controlling when an instruction might be speculatively executed is too difficult."
To confirm, a colleague suggested replacing xdcbt with breakpoint instructions. The crashes vanished—proving speculative execution was the culprit. The team ultimately banned xdcbt entirely, deeming it irredeemably hazardous.
Why This Still Matters
This 2005 flaw mirrors Meltdown/Spectre’s core mechanism: speculative execution side effects leaking sensitive data or corrupting state. Both cases highlight how hardware optimizations—branch prediction, cache bypassing—introduce subtle, systemic risks. As Dawson notes, modern systems face analogous threats, like GPU-CPU cache incoherence in consoles, where misaligned data can trigger similar chaos.
For developers, the lesson is stark: performance shortcuts often come with hidden costs. Hardware must balance speed with robustness, and software must assume speculative execution can expose any instruction—even those never "officially" executed. In an era of pervasive side-channel vulnerabilities, Dawson’s Xbox 360 saga remains a cautionary tale of how pushing silicon to its limits can unravel the very foundations of secure computing.
Source: Finding a CPU Design Bug in the Xbox 360 by Bruce Dawson
Comments
Please log in or register to join the discussion