Intruder's new open-source tool Autoswagger scans exposed API documentation to uncover dangerous broken authorization vulnerabilities. Testing revealed sensitive data exposures at major enterprises, highlighting how publicly accessible schemas create attack surfaces attackers exploit.
APIs remain one of the most vulnerable entry points in modern applications, as demonstrated by high-profile breaches like the 2022 Optus incident where attackers stole millions of records through an unauthenticated endpoint. Despite widespread awareness, Intruder's security team continues to find identical flaws in major organizations—including S&P 500 companies—where attackers can exploit endpoints without technical expertise.
How Autoswagger Works
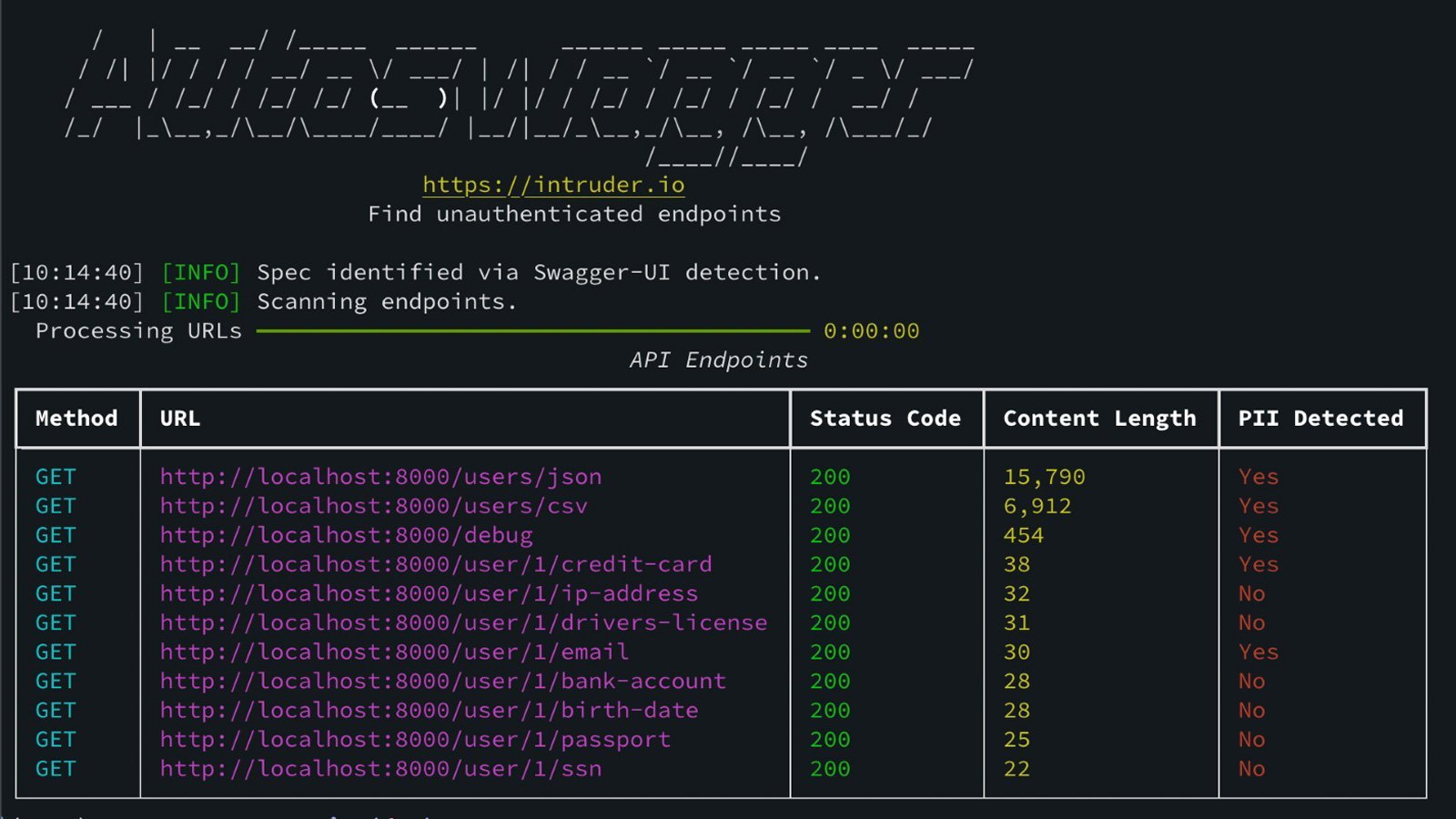
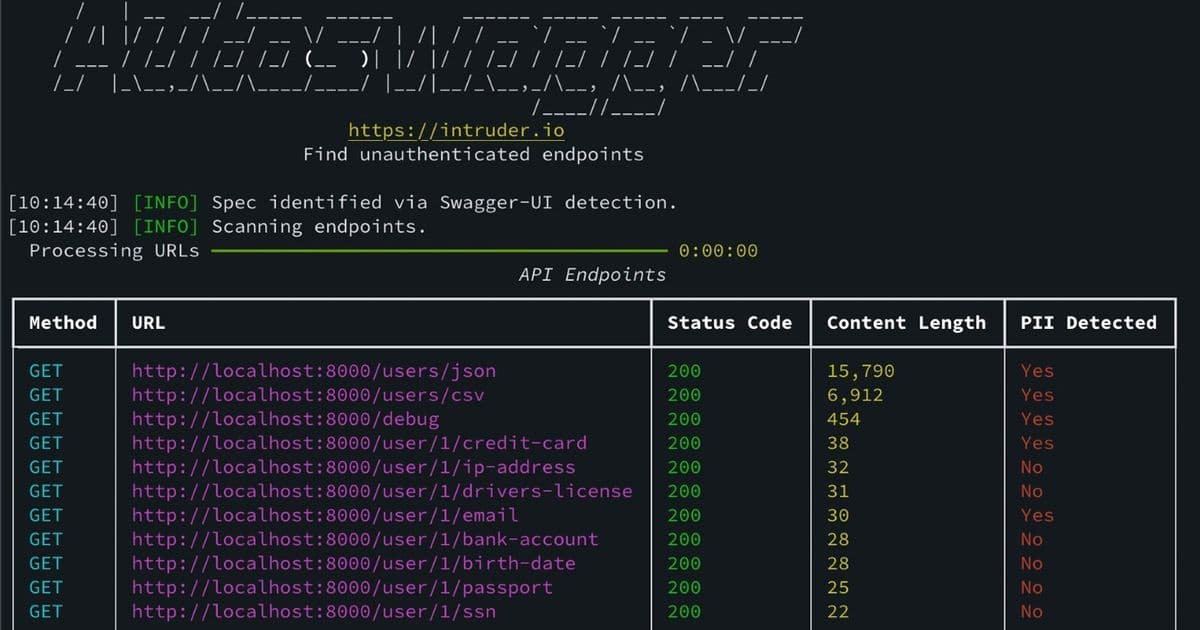
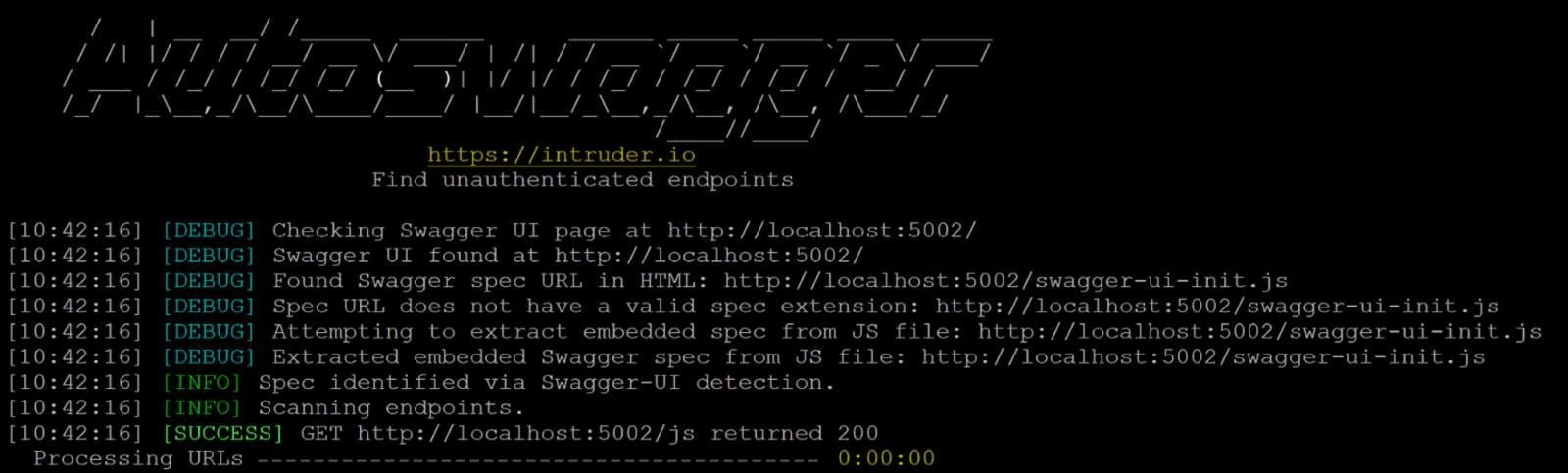 Autoswagger automates the discovery of exposed API documentation (like OpenAPI/Swagger schemas), parses endpoints, and tests them for broken authorization. The tool sends requests using valid parameters from the documentation and flags endpoints that return:
Autoswagger automates the discovery of exposed API documentation (like OpenAPI/Swagger schemas), parses endpoints, and tests them for broken authorization. The tool sends requests using valid parameters from the documentation and flags endpoints that return:
- Sensitive data (PII, credentials)
- Successful responses without proper 401/403 access controls
Developers can run it locally via GitHub, with an optional --brute flag to bypass validation checks for deeper testing. This approach mirrors how attackers use documentation as a roadmap for exploitation.
Real-World Vulnerabilities Uncovered
When tested against bug bounty targets, Autoswagger exposed alarming gaps:
- Microsoft MPN Credentials: An unsecured
/configendpoint exposed Redis credentials containing partner PII and training records. - 60,000+ Salesforce Records: A tech company's API allowed bulk extraction of customer data by incrementing a date parameter.
- SQL Injection in Training App: A beverage company's internal Azure Functions API permitted arbitrary SQL queries revealing staff emails.
- Active Directory Enumeration (CVE-2025-0589): Octopus Deploy servers leaked AD user data via an unauthenticated endpoint.
The Double-Edged Sword of API Documentation
Automated documentation accelerates development but creates significant risk when exposed. As Intruder's findings show, internal APIs often inadvertently publish schemas, giving attackers a precise blueprint for intrusion. While hiding documentation isn't a security solution, reducing unnecessary exposure limits attack surfaces.
For teams managing complex API ecosystems, tools like Autoswagger provide critical visibility into authorization gaps before malicious actors exploit them. As APIs continue to proliferate, proactive vulnerability hunting shifts from luxury to necessity.
Source: BleepingComputer, sponsored by Intruder
Comments
Please log in or register to join the discussion