A sophisticated Coyote malware variant is exploiting Microsoft's UI Automation framework—designed for assistive technologies—to stealthily identify and target banking and crypto exchange sessions. This marks the first documented real-world abuse of Windows' accessibility features for credential theft, evading traditional security tools while expanding malware capabilities.

A dangerous evolution of the Coyote banking trojan is leveraging Windows' core accessibility infrastructure to conduct reconnaissance on high-value financial targets, cybersecurity researchers reveal. Microsoft's UI Automation (UIA) framework—intended to enable assistive technologies for users with disabilities—is being weaponized to identify active banking and cryptocurrency exchange sessions for data theft.
The Accessibility Backdoor
Microsoft's UIA allows programs to inspect and interact with application UI elements through an automation tree. As Akamai researchers warned in December 2024, this powerful capability creates a security blind spot:
"Malware can traverse browser tabs and address bars to extract URLs without triggering endpoint detection, effectively turning an accessibility feature into a surveillance tool."
Coyote's Novel Attack Chain
The malware—primarily targeting Brazilian users—scans for 75 specific financial services including Banco do Brasil, Santander, Binance, and Bitcoin wallets. Its updated workflow combines traditional tactics with UIA exploitation:
- Initial Recon: Checks window titles for target names
- UIA Fallback: If titles don't match, parses browser tabs/address bars via UIA
- Target Validation: Cross-references URLs against hardcoded financial sites
- Data Theft: Deploys keyloggers or phishing overlays post-identification
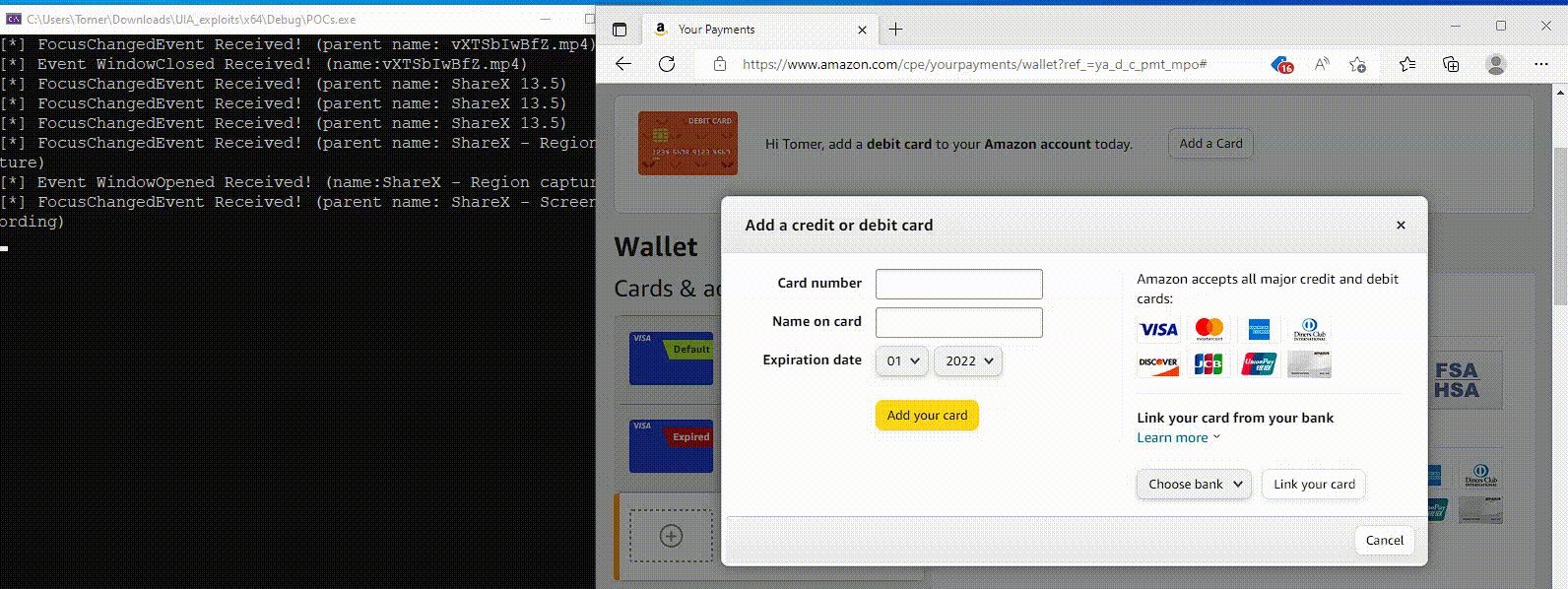 Demonstration of UIA-based credential theft (Source: Akamai)
Demonstration of UIA-based credential theft (Source: Akamai)
Beyond Reconnaissance
While current attacks use UIA only for target identification, Akamai demonstrated proof-of-concept credential theft using the same framework. This mirrors years of Android accessibility abuse, where malware like Anatsa exploited similar features until Google implemented countermeasures.
The Silent Threat Landscape
This represents a significant escalation in Windows malware sophistication:
- Detection Evasion: UIA interactions appear legitimate to security tools
- Precision Targeting: Focuses exclusively on high-value financial sessions
- Future Risk: Framework could enable automated form input manipulation
Microsoft hasn't yet commented on potential safeguards. For now, the malware's abuse of built-in Windows capabilities highlights the delicate balance between accessibility and security—a balance malicious actors increasingly exploit.
Source: BleepingComputer with research from Akamai

Comments
Please log in or register to join the discussion