Python's ubiquity in development and infrastructure makes it a prime target for attackers, yet widespread security negligence in code auditing, developer training, and privilege management creates alarming vulnerabilities. Research reveals how unchecked Python environments become launchpads for injection attacks and lateral movement. This systemic risk demands urgent shifts in development culture and tooling adoption.
Python’s dominance in everything from AI development to cloud automation is undeniable. Its accessibility fuels innovation, but security researchers warn this very trait makes it a high-value target for attackers. Unlike compiled languages, Python’s dynamic nature allows arbitrary code execution—a feature routinely exploited in injection attacks and remote code execution (RCE) exploits. Yet, the language itself is only part of the problem. Three critical systemic failures compound the risk:
- The Auditing Void: A staggering volume of Python codebases never undergoes rigorous security scrutiny. Static Application Security Testing (SAST) and dynamic analysis are frequently absent throughout the development lifecycle (dev, staging, production). Vulnerabilities introduced early can persist undetected for years.
- The Knowledge Gap: Many Python developers lack foundational secure coding training. This, coupled with the rise of AI coding assistants that often generate functionally correct but insecure code, leads to pervasive weaknesses. Common pitfalls include improper input validation, unsafe deserialization, and reliance on vulnerable dependencies.
- Privilege Proliferation: Overly permissive accounts—used by developers, testers, and automation—are endemic. Attackers exploiting a Python vulnerability can leverage these excessive privileges for rapid lateral movement, data theft, or full system compromise.
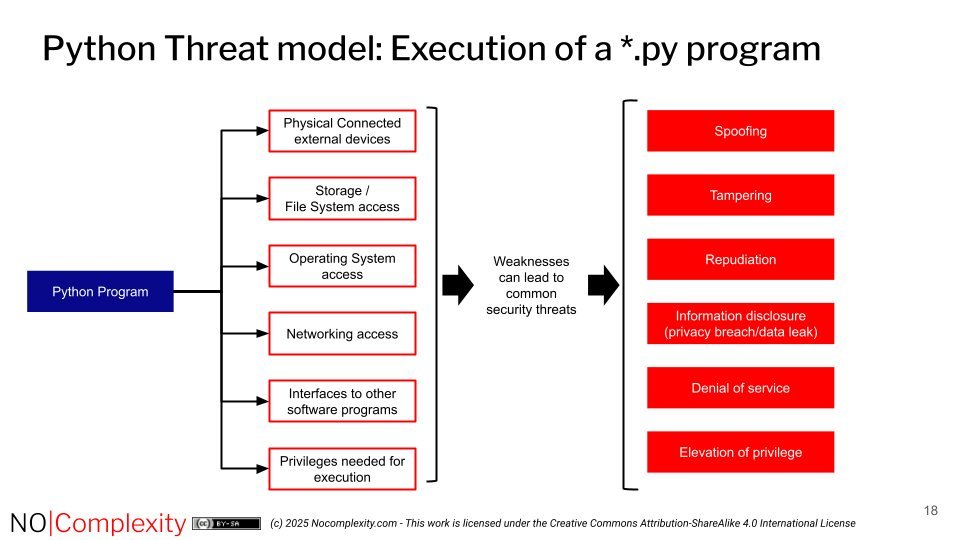
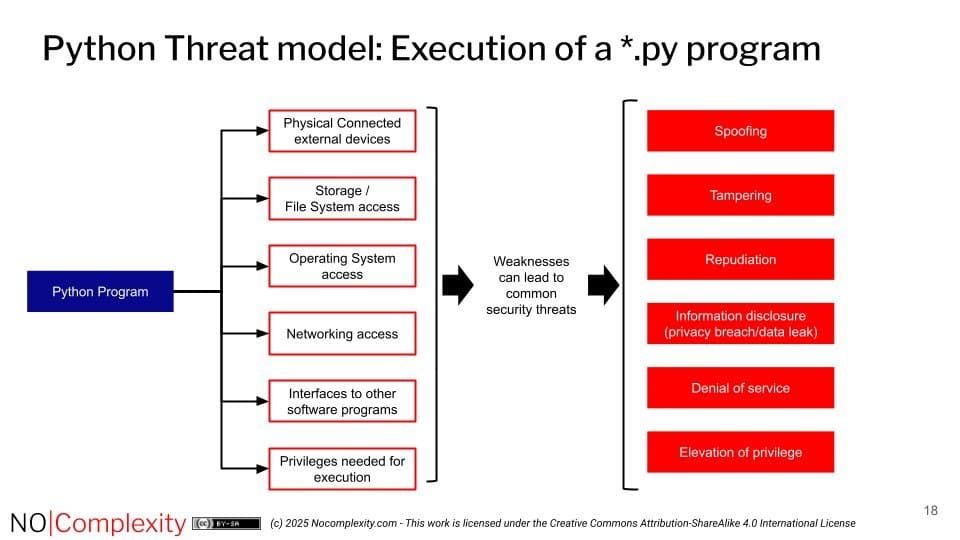
Python's flexibility combined with these systemic weaknesses creates a perfect storm. Malicious actors exploit Python's presence on developer workstations and servers, using it as a foothold. Common attack vectors include:
- Code Injection: Exploiting
eval(),pickle, or template engines to execute attacker-supplied code. - Dependency Poisoning: Compromising lesser-known PyPI packages.
- Environment Manipulation: Abusing misconfigured permissions or environment variables.
Addressing this requires more than just patching individual bugs; it demands cultural change. Integrating security into the development pipeline is paramount. Static Application Security Testing (SAST) tools specifically designed for Python, like the mentioned Python Code Audit, offer a critical layer of defense. These tools automate the detection of common vulnerabilities and insecure patterns directly in source code, shifting security left:
# Example of SAST potentially flagging a risky pattern
import pickle
# Warning: Unvalidated deserialization - Potential RCE!
data = input("Enter pickled data: ")
deserialized_data = pickle.loads(data) # SAST tool would flag this
While no tool is a silver bullet, SAST provides essential visibility into code-level risks often missed during manual reviews. Its integration, combined with mandatory security training, strict privilege control (adhering to least privilege principles), and regular dependency scanning, forms the bedrock of a resilient Python ecosystem. The time for complacency is over; securing Python requires recognizing it not just as a tool, but as a critical—and vulnerable—component of our infrastructure.
Comments
Please log in or register to join the discussion