Attackers exploited GitHub's notification system to send fraudulent Y Combinator funding invitations to developers, deploying cryptocurrency drainers via typosquatted domains. The campaign abused repository issue tagging to deliver seemingly legitimate emails, ultimately tricking victims into signing malicious Ethereum transactions. This incident highlights evolving supply chain risks targeting developers through trusted platforms.
A sophisticated phishing operation has weaponized GitHub's notification system to impersonate startup accelerator Y Combinator, targeting developers with cryptocurrency-stealing malware. The attackers created repositories specifically to abuse GitHub's automated mention notifications, tagging hundreds of users with fake invitations to Y Combinator's Winter 2026 (W2026) batch program.
How the Attack Unfolded
Notification Hijack: Attackers created new GitHub accounts and repositories, then opened issues mentioning targeted developer usernames. This triggered GitHub's automated email notifications—messages that appear legitimate since they originate from
[email protected].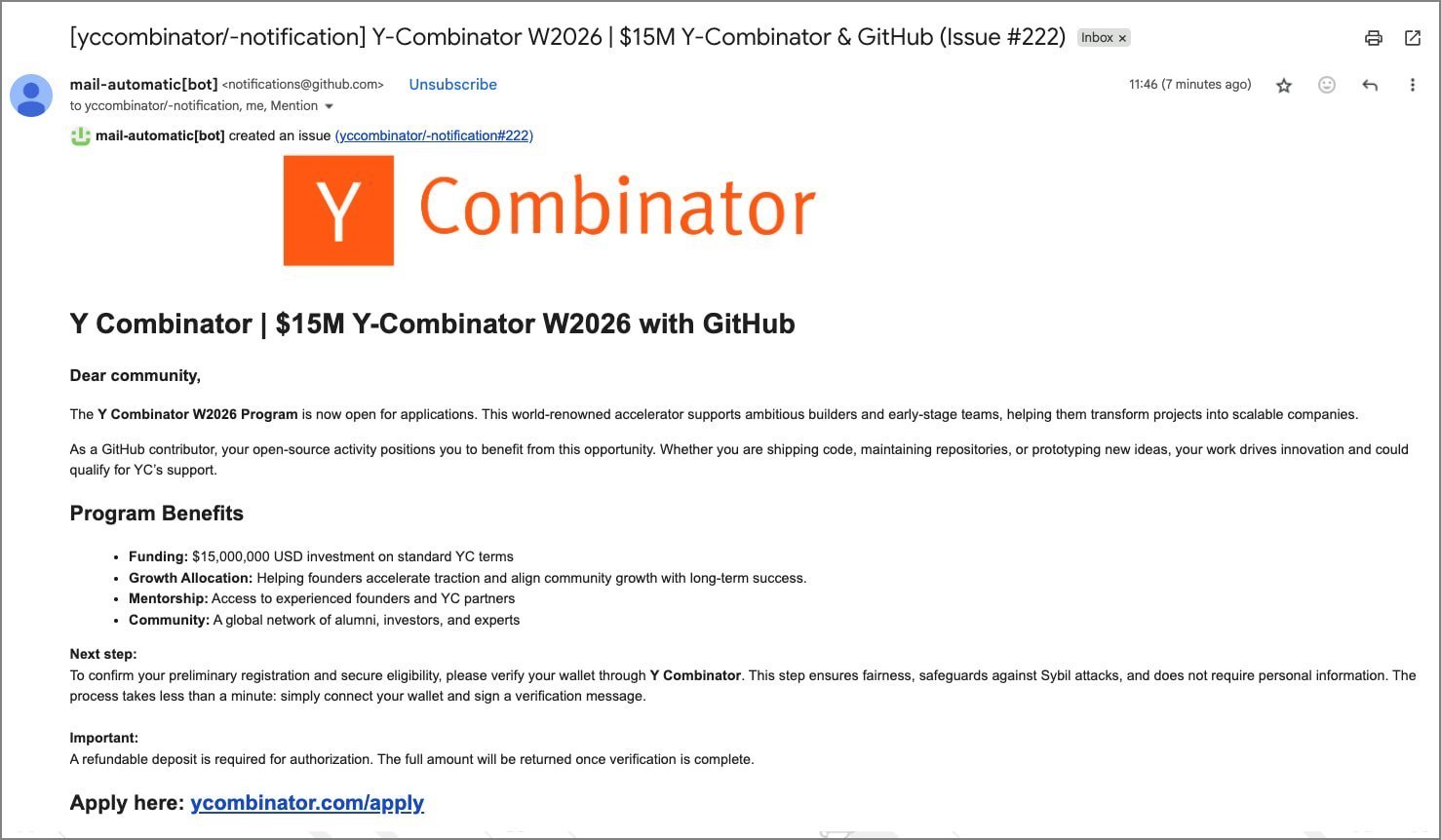 The phishing email delivered via GitHub's notification system (Source: BleepingComputer)
The phishing email delivered via GitHub's notification system (Source: BleepingComputer)The Lure: Messages promised $15 million in funding via Y Combinator's prestigious W2026 program, leveraging the accelerator's reputation to bypass skepticism.
Typosquatted Trap: Clicking the application link led to a domain where 'ycombinator' was misspelled (replacing 'i' with 'l'). The fake site mirrored YC's branding. {{IMAGE:4}} Fraudulent website impersonating Y Combinator (Source: BleepingComputer)
Crypto Drainer Execution: Victims were prompted to "verify" crypto wallets using "EIP-712 + Ethereum Attestation Service." The site displayed a deceptive message:
"During the process, you may see a standard withdrawal notification — this confirms your signature to record verification stamps on-chain. We guarantee that your assets remain completely secure" In reality, signing the transaction granted attackers withdrawal permissions, draining wallets.
Technical Implications
- Supply Chain Vulnerability: Abuse of GitHub's trusted notification system bypasses traditional email filters, exploiting developer workflows.
- Precision Targeting: Attackers likely scraped GitHub profiles to identify targets with public cryptocurrency affiliations.
- Obfuscation Tactics: JavaScript obfuscation hid the drainer's logic, while the EIP-712 standard lent false legitimacy.
Mitigation and Response
GitHub has removed the malicious repositories following reports. Developers should:
- Immediately revoke wallet permissions granted to suspicious sites using revoke.cash or Etherscan's Token Approvals checker.
- Migrate assets to new wallets if they interacted with the drainer.
- Verify domains meticulously—especially when cryptocurrency transactions are involved.
The legitimate Y Combinator application portal remains at ycombinator.com/apply. This incident underscores how attackers increasingly exploit trust in developer ecosystems, turning collaboration tools into attack vectors. Vigilance against unexpected invitations—even from "trusted" systems—is now essential armor in the crypto development landscape.
Source: BleepingComputer

Comments
Please log in or register to join the discussion