Security firm CTM360 has uncovered a sophisticated malware operation targeting TikTok's e-commerce ecosystem. Dubbed 'ClickTok,' the hybrid attack combines fake shops and trojanized apps to deploy SparkKitty spyware, harvesting cryptocurrency credentials through screenshot theft. The campaign has already spawned over 10,000 impersonated domains and 5,000 malicious app instances.

Security researchers at CTM360 have exposed a highly coordinated global malware campaign dubbed "ClickTok" that weaponizes TikTok's e-commerce platforms to steal cryptocurrency. The operation targets unsuspecting users of TikTok Shop, TikTok Wholesale, and TikTok Mall through a dangerous fusion of phishing and malware tactics, marking a significant evolution in social media-enabled cybercrime.
The Hybrid Attack Vector
ClickTok employs a dual-pronged approach to compromise victims:
- Phishing Infrastructure: Threat actors create thousands of fake TikTok domains (using TLDs like .top, .shop, .icu) that perfectly mimic official interfaces. These sites harvest credentials during fake "checkout" processes where users are instructed to pay via cryptocurrency wallets.
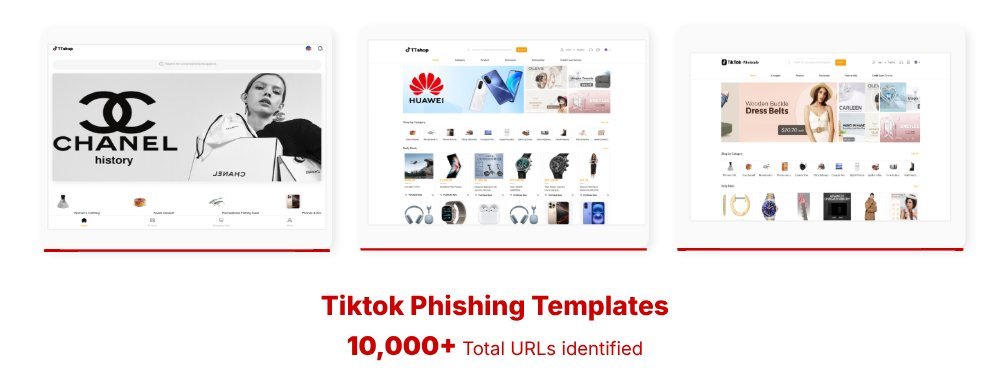 Fake TikTok Shop login templates used in ClickTok campaign (CTM360)
Fake TikTok Shop login templates used in ClickTok campaign (CTM360)
- Trojanized Applications: Users are tricked into downloading malicious Android apps infected with SparkKitty spyware—a variant of the known SparkCat malware. These apps mirror legitimate TikTok interfaces while performing:
- Real-time device surveillance
- Clipboard scraping
- Extraction of cryptocurrency credentials from gallery screenshots
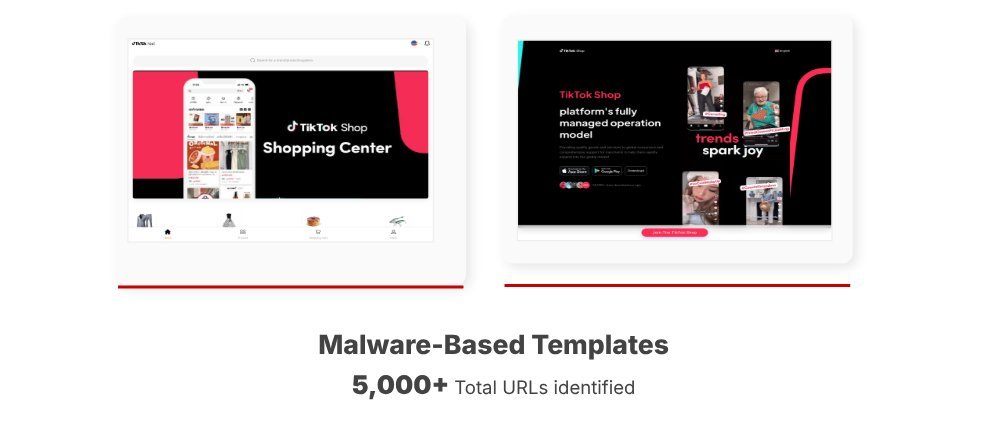 Malicious app templates distributing SparkKitty spyware (CTM360)
Malicious app templates distributing SparkKitty spyware (CTM360)
Why This Attack Stands Out
ClickTok's sophistication lies in its hybrid monetization model:
- Credential Harvesting: Fake shops capture seller/buyer logins for account takeover
- Wallet Draining: SparkKitty scans devices for wallet screenshots and seed phrases
- Forced Crypto Payments: Victims are coerced into "topping up" fake TikTok wallets with USDT, ETH, or other cryptocurrencies
CTM360 has documented over 10,000 impersonated domains and 5,000+ malicious app instances distributed via Meta ads, AI-generated videos, QR codes, and messaging platforms. The campaign exploits TikTok's rapid e-commerce growth, using lookalike domains and deepfake-style content to appear legitimate.
Mitigation Strategies
CTM360 recommends:
- ✔️ Avoid modded apps—especially from Telegram or torrent sites
- ✔️ Manually verify domains for spelling errors/suspicious TLDs
- ✔️ Use clipboard-protected crypto wallets
- ✔️ Deploy advanced EDR solutions to detect SparkKitty
- ✔️ Brands should continuously monitor for impersonations
"This campaign exemplifies the next generation of social media threats—where platform trust is weaponized at industrial scale. The fusion of phishing and spyware creates a self-sustaining fraud ecosystem," notes CTM360's threat intelligence team.
As e-commerce platforms increasingly embed financial functionality, ClickTok serves as a stark reminder that user interfaces can no longer be trusted at face value. The incident underscores critical needs for enhanced domain monitoring, behavioral-based malware detection, and user education on crypto transaction risks.

Comments
Please log in or register to join the discussion