As phishing and cookie theft attacks skyrocket by 84%, Google unveils Device Bound Session Credentials and expanded passkey support to fortify account security. These innovations aim to render stolen credentials useless and offer IT admins critical tools for enterprise defense.
Cyberattacks are evolving at a breakneck pace, with phishing and credential theft driving 37% of successful breaches, while cookie and authentication token theft surged 84% in 2024 alone. This alarming trend, intensifying in 2025, has pushed Google to deploy a multi-layered security overhaul. In a recent announcement, the tech giant detailed how its new tools—passkeys, Device Bound Session Credentials (DBSC), and the Shared Signals Framework (SSF)—are engineered to outmaneuver modern threats. For developers and security teams, this isn't just an update; it's a fundamental shift toward eliminating the weakest link in digital defense: passwords.
The Passwordless Revolution Gains Momentum
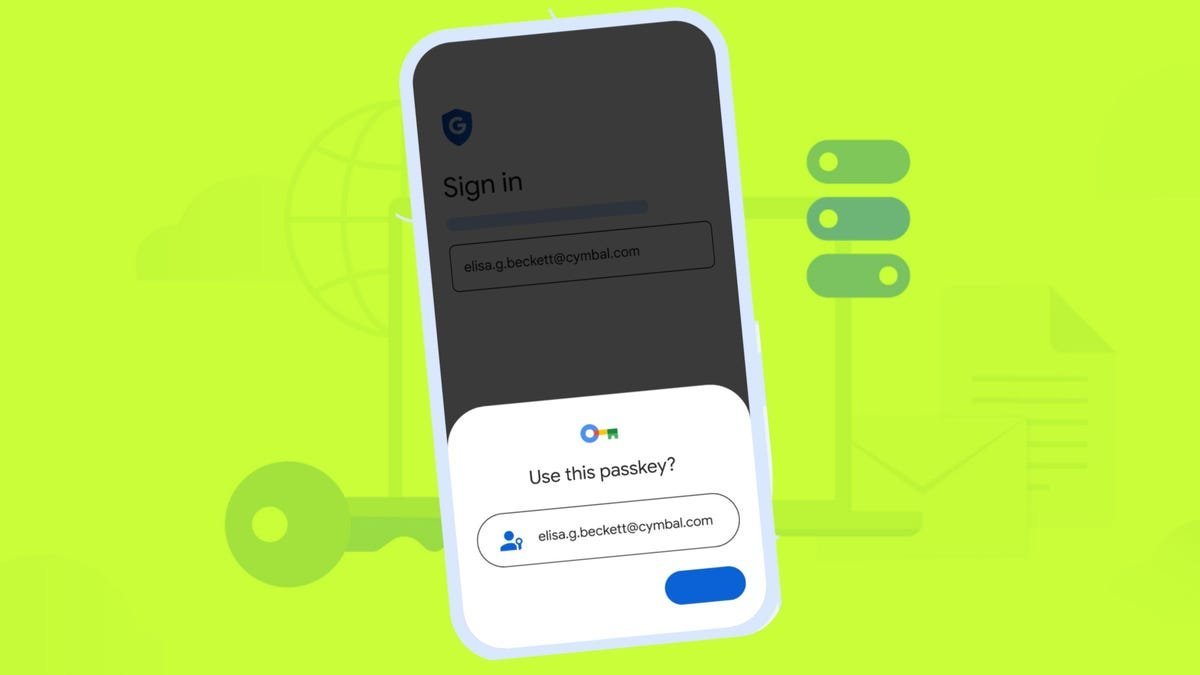
Passkeys, Google's flagship alternative to traditional passwords, are now active across 11 million Google Workspace accounts. By leveraging biometrics, PINs, or physical security keys for authentication, passkeys neutralize phishing risks—since they can't be shared or reused—and streamline user logins. IT admins gain granular control, with upcoming features allowing passkey audits and restrictions to hardware security keys. As Google notes: "To enhance security and prevent account takeovers stemming from phishing and infostealers, we recommend customers enable passkeys immediately." This move accelerates the industry-wide pivot to passwordless systems, reducing the attack surface for credential theft.
Locking Down Sessions with Device Binding
Where passkeys secure initial access, DBSC tackles the rampant theft of session cookies and tokens—a favorite tactic for attackers aiming to hijack active logins. Now in open beta for Chrome on Windows, DBSC binds session cookies to the originating device. Even if credentials are stolen, attackers can't reuse them elsewhere. Google highlights three core advantages:
- Enhanced post-authentication protection: Sessions are confined to the device that created them.
- Reduced cookie theft risk: Stolen cookies become inert on unauthorized devices.
- Strengthened session integrity: Combined with context-aware access, DBSC blocks compromised credentials from activating sessions.
Real-Time Threat Intelligence with Shared Signals
Rounding out its strategy, Google's Shared Signals Framework (SSF) enters beta to enable real-time security alerts between partners. As an OpenID standard, SSF facilitates instant data exchange on emerging threats, allowing organizations to react faster to incidents like token breaches. This interoperability is crucial for enterprises weaving together cloud, identity, and endpoint security systems—especially as attacks grow more coordinated.
Why This Matters for Tech Professionals
For developers, DBSC's device-binding approach could inspire similar API-level protections in custom applications, while passkeys simplify authentication flows. IT leaders must prioritize rolling out these tools: Delaying adoption leaves gaps in defenses against exponentially growing infostealers. As cookie theft eclipses password cracking, Google's focus on session security signals a broader industry reckoning—where trust in credentials alone is obsolete, and every interaction must be cryptographically anchored.
Source: ZDNet
Comments
Please log in or register to join the discussion