Modern iOS and Android devices can share Wi‑Fi access in seconds—no sticky notes, no shouted passwords, and far fewer security disasters. Behind this simple UX is a quiet but important evolution in how we model trust, identity, and access on consumer networks.
 )
)
Trying to onboard yet another device to your home or office Wi‑Fi should not feel like digital archaeology. Yet many of us still rummage through drawers for a router sticker, shout complex passphrases across the room, or—worse—dumb down our passwords so guests can type them faster.
The good news: iOS and Android have already solved most of this, and not just as a convenience feature. Done right, instant Wi‑Fi sharing is a more secure pattern for how we grant access to networks without oversharing secrets.
This story is based on ZDNET's practical walkthrough of Wi‑Fi sharing techniques across iPhone, iPad, Mac, and Android devices, and extends it with a closer look at why these patterns matter for anyone designing secure, user-friendly systems.
The old way: Convenience vs. confidentiality
Before we talk about the built-ins, it’s worth naming the anti-patterns many households and even small offices still use:
- Printing or taping the Wi‑Fi password to the wall.
- Reusing short, human-friendly passwords across networks.
- Texting passwords into permanent chat logs.
- Typing credentials directly into guests’ devices (which you never fully control).
Every one of these leaks a long-lived secret. Once your PS5, a contractor’s laptop, and your TV installer’s phone all know the same password, rotating it becomes painful—and so it never happens.
Apple’s sharing flow and Android’s Quick Share/QR features flip that model: instead of exposing the password, the already-trusted device vouches for the new one.
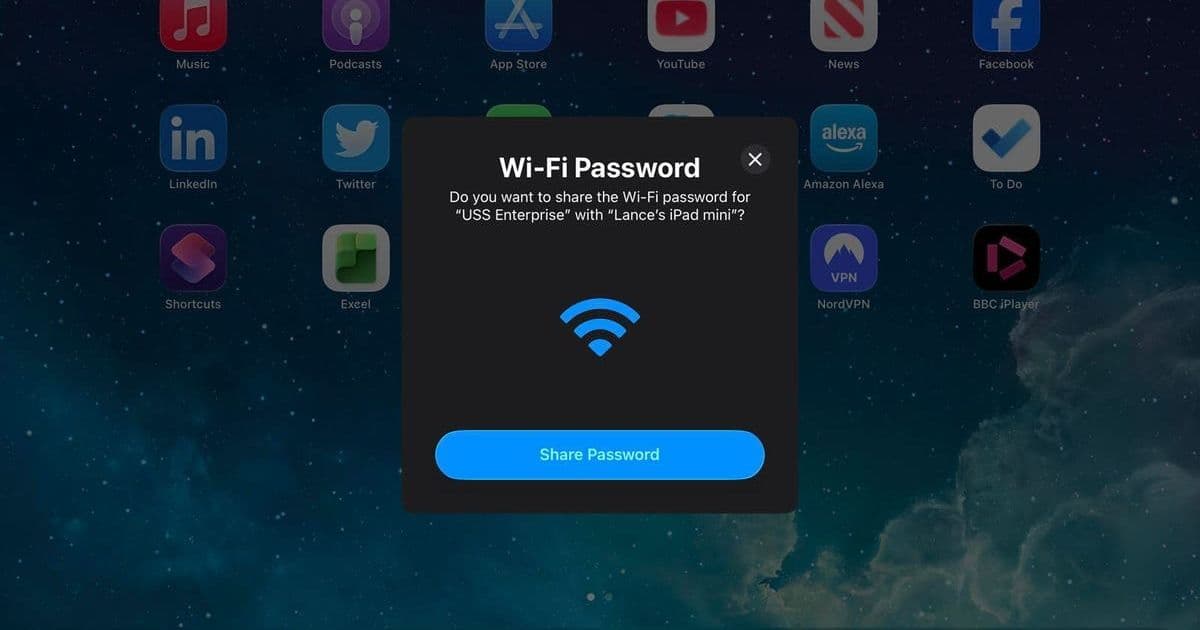
How Apple turned Wi‑Fi access into a trust handshake
On Apple platforms, Wi‑Fi sharing looks deceptively simple:
- A device (iPhone, iPad, or Mac) that’s already connected to the network sits near the new device.
- On the new device, the user selects the target Wi‑Fi SSID in Settings.
- The trusted device prompts its owner: “Share Password?”
- With a tap, the new device is provisioned and joins automatically.
This works cross-device within the Apple ecosystem—iPhone to iPad, Mac to iPhone, etc.—with two subtle but important constraints:
- The device owners must be in each other’s Contacts.
- It doesn’t bridge Apple ↔ Android.
Those constraints matter. They encode a social trust graph (Contacts) into the technical trust decision, reducing the risk that a random device nearby can siphon credentials.
Is this perfect security? No. But compared to reading your passphrase off a router label, it’s a meaningful upgrade:
- The user of the already-connected device stays in control of approvals.
- The joiner never needs to see or store the raw password.
- Password complexity can be high without adding user friction.
For power users and admins, Apple’s model is an instructive UX design: strong defaults, minimum ceremony, socially aware trust, and no unnecessary revelation of secrets.
When you must reveal the key (and how to leak less)
Sometimes, you have to surface the actual Wi‑Fi password—for smart TVs, older consoles, IoT devices, or cross-ecosystem setups.
On iOS/iPadOS, ZDNET notes the supported path:
- Go to Settings → Wi‑Fi.
- Tap your connected network.
- Tap the password field; authenticate with Face ID, Touch ID, or passcode.
- The password is revealed and can be copied or read out.
This flow re-centers secrets behind device-level authentication. It’s a small but crucial guardrail: only someone with physical access and unlock rights can exfiltrate the credential.
For developers, that’s a clear pattern worth emulating in your own apps and admin tools:
- Never show sensitive values in plaintext by default.
- Gate explicit reveals behind local, strong authentication.
- Make copying easy to reduce shoulder-surfing and retyping errors.
Android’s answer: Quick Share and QR codes as secure channels
Android’s ecosystem adds its own twist via Quick Share and QR-based provisioning.
From ZDNET’s walkthrough:
- On a connected Android device, open Wi‑Fi settings.
- Select the current network → Share / Share Network.
- Either:
- Use Quick Share to push credentials directly to a nearby device; or
- Display a QR code that another device can scan to auto-join.
Both flows encapsulate the password rather than humanizing it. The QR approach, in particular, is a pragmatic bridge for:
- Smart home gadgets with cameras or pairing apps.
- Laptops and phones in mixed BYOD environments.
When viewing the password directly, many Android devices (e.g., Samsung) follow the same pattern as Apple: tap an eye icon or Share, authenticate biometrically or via PIN, then reveal the secret.
Again, the lesson for system designers:
- Use machine-readable provisioning (QR/NFC/deep links) instead of forcing humans to handle raw secrets.
- Ensure every reveal or share operation is auditable and gated by local authentication.
 )
)
What this means for people who build systems
If you’re designing Wi‑Fi onboarding for offices, co-working spaces, or device-heavy homes—or architecting any authentication flow—these native patterns are more than consumer tips. They’re a blueprint.
Key takeaways:
Treat access as delegatable, not copyable.
- Let a trusted, authenticated entity grant access without exposing the underlying secret. This is conceptually similar to issuing short-lived tokens instead of sharing API keys.
Bind trust to relationships and context.
- Apple’s Contacts requirement is a simple instance of this. In enterprise scenarios, that might map to your IdP, MDM enrollment, or group policies.
Authenticate before reveal.
- Both ecosystems assume that revealing a password is a privileged act, not a default UI state. Copy that—literally.
Prefer ephemeral or revocable paths.
- Features like QR sharing are ideal when combined with guest networks and separate VLANs. Guests get connectivity; your core network stays segmented.
Design for the edge case where users will screenshot or paste.
- The more painful your official flow is, the more users will bypass it via screenshots, notes apps, or Slack DMs. Smooth UX is a security control.
Beyond your living room: a quiet standard for secure onboarding
These “simple phone tricks” hint at a future where onboarding is less about memorizing secrets and more about controlled, contextual delegation. For home users, that means finally retiring the router-sticker ritual. For developers, IT teams, and product designers, it’s a living case study in how to merge user experience with practical security.
The next time someone asks for your Wi‑Fi, how you respond isn’t just a party courtesy. It’s a small expression of how you think about trust—and a reminder that good security often starts with the details we’re now able to hide in plain sight.
Source: Original how-to reporting and screenshots from ZDNET, “Need to share your Wi‑Fi password? Do it instantly with this simple phone trick” (Nov. 12, 2025).
Comments
Please log in or register to join the discussion