The Kimwolf IoT botnet has been disrupting the I2P anonymity network by flooding it with hundreds of thousands of infected devices, causing widespread outages and highlighting the vulnerability of decentralized networks to Sybil attacks.
The massive "Internet of Things" (IoT) botnet known as Kimwolf has been disrupting The Invisible Internet Project (I2P), a decentralized, encrypted communications network designed to anonymize and secure online communications. For the past week, I2P users have experienced significant service disruptions as tens of thousands of infected routers suddenly overwhelmed the network, preventing legitimate users from communicating with nodes.
Kimwolf, which surfaced in late 2025, has quickly infected millions of systems, turning poorly secured IoT devices like TV streaming boxes, digital picture frames, and routers into relays for malicious traffic and abnormally large distributed denial-of-service (DDoS) attacks. The botnet's operators began relying on I2P to evade takedown attempts against the botnet's control servers, inadvertently causing widespread network disruptions in the process.
Understanding the I2P Network
I2P is a decentralized, privacy-focused network that allows people to communicate and share information anonymously. According to the I2P website, "It works by routing data through multiple encrypted layers across volunteer-operated nodes, hiding both the sender's and receiver's locations. The result is a secure, censorship-resistant network designed for private websites, messaging, and data sharing."
On February 3, I2P users began complaining on the organization's GitHub page about tens of thousands of routers suddenly overwhelming the network. Users reported a rapidly increasing number of new routers joining the network that were unable to transmit data, and that the mass influx of new systems had overwhelmed the network to the point where users could no longer connect.
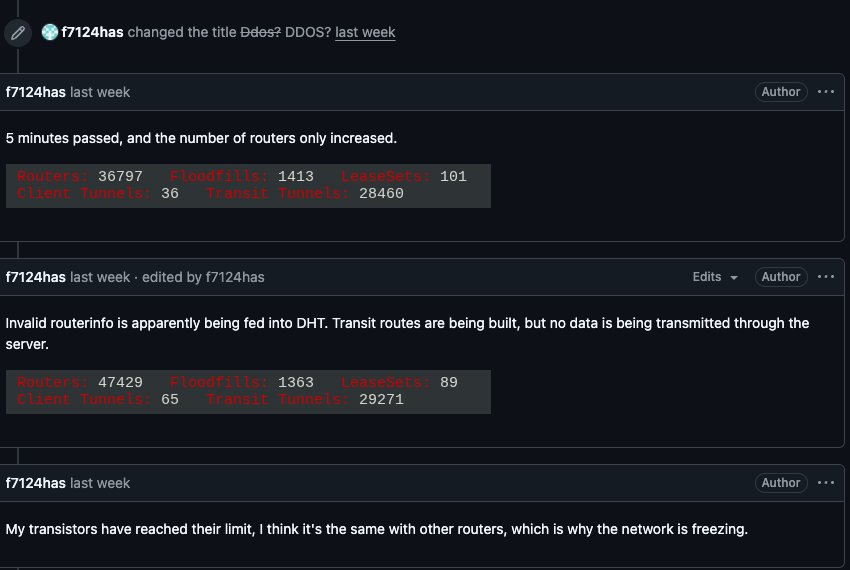
When one I2P user asked whether the network was under attack, another user replied, "Looks like it. My physical router freezes when the number of connections exceeds 60,000."
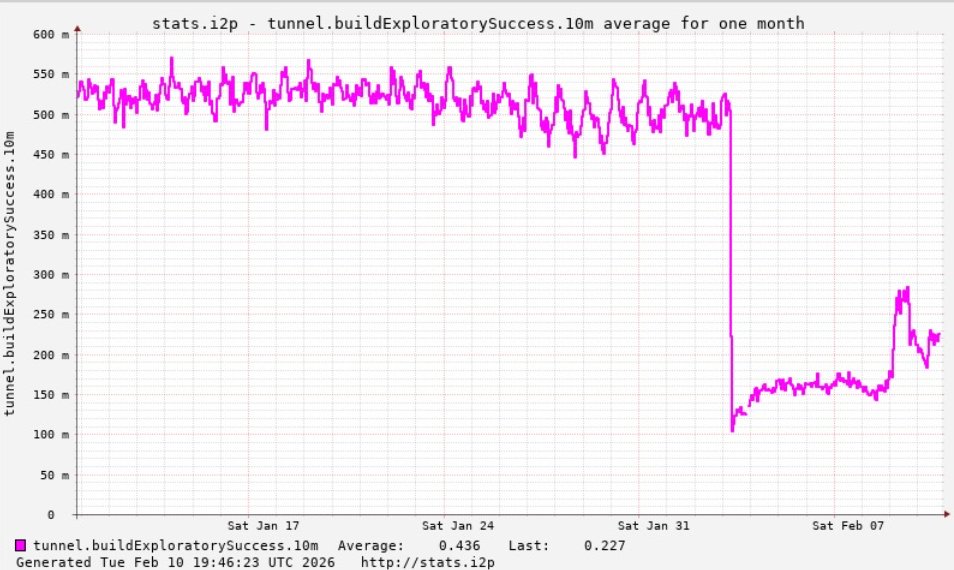
A graph shared by I2P developers showed a marked drop in successful connections on the I2P network around the time the Kimwolf botnet started trying to use the network for fallback communications.
The Accidental Disruption
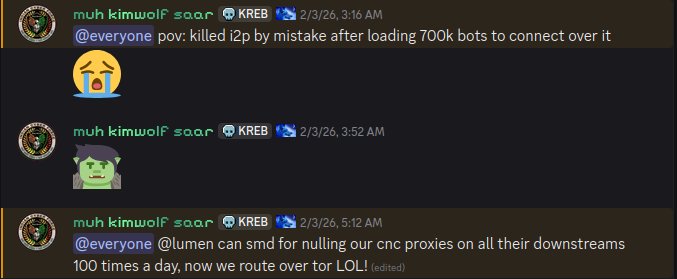
The same day that I2P users began noticing the outages, the individuals in control of Kimwolf posted to their Discord channel that they had accidentally disrupted I2P after attempting to join 700,000 Kimwolf-infected bots as nodes on the network.
This incident represents what's known as a "Sybil attack," a threat in peer-to-peer networks where a single entity can disrupt the system by creating, controlling, and operating a large number of fake, pseudonymous identities. The number of Kimwolf-infected routers that tried to join I2P this past week was many times the network's normal size.
According to Lance James, founder of the New York City-based cybersecurity consultancy Unit 221B and the original founder of I2P, the entire I2P network now consists of between 15,000 and 20,000 devices on any given day, despite Wikipedia listing the network at roughly 55,000 computers distributed throughout the world.
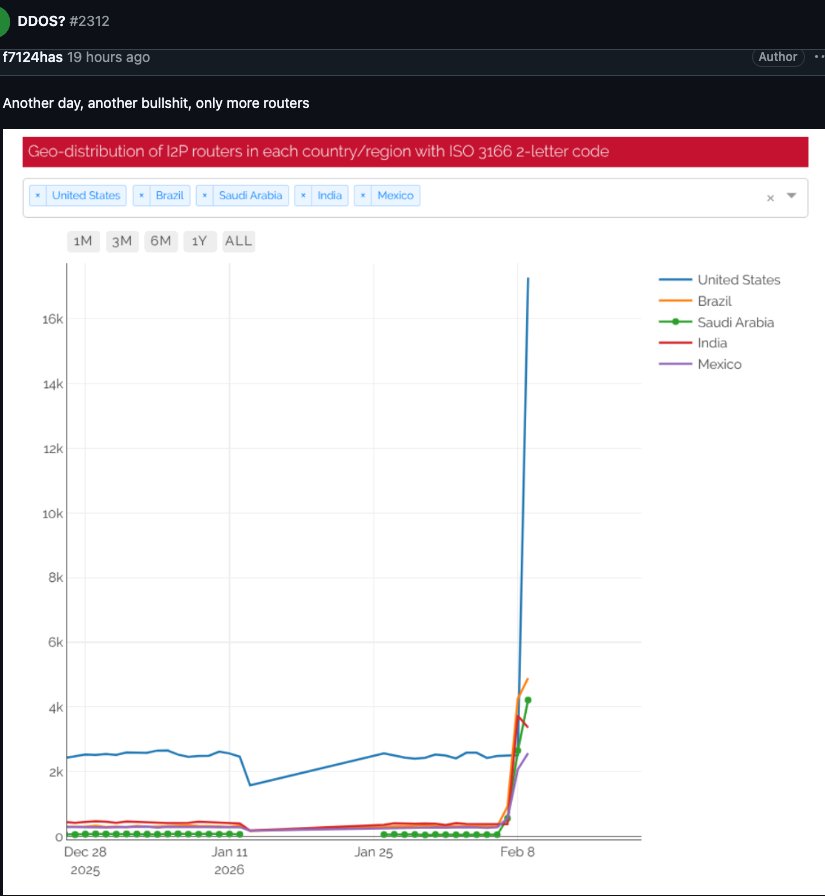
An I2P user posted a graph on Feb. 10 showing tens of thousands of routers—mostly from the United States—suddenly attempting to join the network.
Botnet Operators' True Intentions
Benjamin Brundage, founder of Synthient, a startup that tracks proxy services and was the first to document Kimwolf's unique spreading techniques, suggests the botnet operators' goals may be misunderstood. "I don't think their goal is to take I2P down," he said. "It's more they're looking for an alternative to keep the botnet stable in the face of takedown attempts."
The Kimwolf operator(s) have been trying to build a command and control network that can't easily be taken down by security companies and network operators working together to combat the spread of the botnet. Brundage said the people in control of Kimwolf have been experimenting with using I2P and a similar anonymity network—Tor—as a backup command and control network, although there have been no reports of widespread disruptions in the Tor network recently.
Broader Implications and Network Recovery
Kimwolf has created challenges for other services as well. Late last year, the botnet began instructing millions of infected devices to use Cloudflare's domain name system (DNS) settings, causing control domains associated with Kimwolf to repeatedly usurp Amazon, Apple, Google, and Microsoft in Cloudflare's public ranking of the most frequently requested websites.
James said the I2P network is still operating at about half of its normal capacity, and that a new release is rolling out which should bring some stability improvements over the next week for users.
Interestingly, Brundage noted that the botnet's overlords appear to have recently alienated some of their more competent developers and operators, leading to a rookie mistake this past week that caused the botnet's overall numbers to drop by more than 600,000 infected systems. "It seems like they're just testing stuff, like running experiments in production," he said. "But the botnet's numbers are dropping significantly now, and they don't seem to know what they're doing."
The Kimwolf incident serves as a stark reminder of the vulnerabilities that exist in decentralized networks and the potential for even accidental disruptions to cause significant service degradation. As IoT devices continue to proliferate with minimal security considerations, the potential for similar incidents to affect other critical infrastructure and privacy-focused services remains a growing concern for the cybersecurity community.
Comments
Please log in or register to join the discussion