Despite advances in multi-factor authentication and zero-trust frameworks, compromised credentials remain responsible for nearly half of all breaches. This deep dive explores why password vulnerabilities persist in hybrid environments and outlines actionable strategies for implementing intelligent password controls that adapt to human behavior and evolving threats.

In January 2024, Russian state-sponsored hackers breached Microsoft's fortified infrastructure by exploiting a fundamental weakness: passwords. This incident underscored a harsh reality that security teams globally confront—despite sophisticated security stacks, credentials remain the primary pivot point for 44.7% of breaches (Verizon DBIR). As environments grow more complex with hybrid cloud, legacy systems, and remote work, password security demands more than checkbox compliance.
The Password Paradox: Ubiquity vs. Vulnerability
Modern IT ecosystems resemble buildings with countless forgotten entrances:
- Legacy accounts in Active Directory and deprecated systems act as unlocked doors
- Password fatigue drives predictable patterns (e.g.,
Summer2024!→Summer2025!) - Users manage ~170 credentials, leading to recycled variations attackers easily weaponize
"These passwords may look tough, but they're about as secure as a paper lock," notes the original analysis. Hackers leverage credential stuffing attacks where one leaked password compromises multiple systems.
Beyond Complexity: Intelligent Control Frameworks
Dynamic Blocklists & Pattern Recognition
Basic dictionary bans are obsolete. Effective solutions must:
- Block 4+ billion known compromised passwords
- Detect company-specific variants (e.g.,
CompanyName2024) - Identify subtle patterns through algorithmic analysis
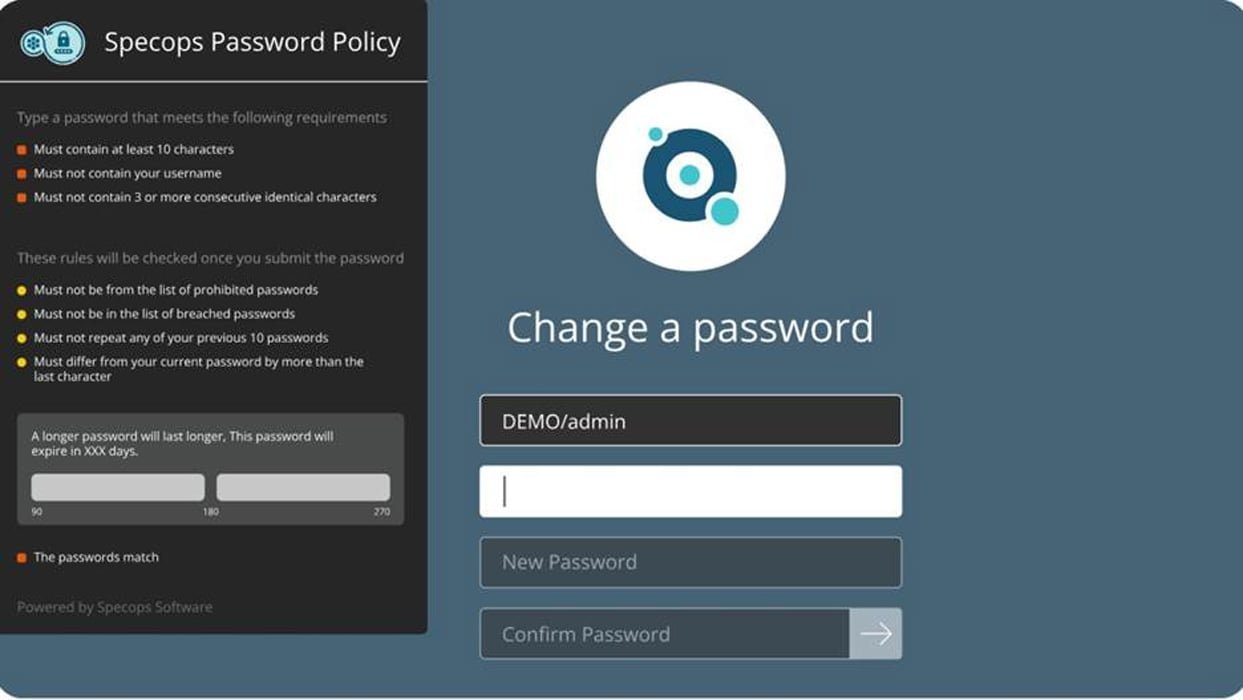 Specops Password Policy exemplifies real-time blocking of noncompliant credentials
Specops Password Policy exemplifies real-time blocking of noncompliant credentials
Human-Centric Design Principles
- Length over complexity: Passphrases (
CorrectHorseBatteryStaple) outperform cryptic strings (P@$$w0rd!) - Staged enforcement: Gradual rollout with user education reduces friction
- Risk-based authentication: Context-aware challenges (location, device, behavior)
The 90-Day Password Resilience Blueprint
| Phase | Actions | Key Metrics |
|---|---|---|
| Days 1-30 | Audit privileged accounts; scan password vulnerabilities; baseline complexity | % of banned passwords detected |
| Days 31-60 | Pilot new policies; train users on passphrase creation; implement MFA for admins | Reduction in reset tickets |
| Days 61-90 | Full rollout; integrate risk-based auth; automate compromised credential monitoring | Mean time to remediate vulnerabilities |
Why Passwords Endure as Critical Infrastructure
Passwords remain the fallback for biometrics and hardware keys—and thus the last line of defense. Organizations treating them as dynamic assets rather than static requirements can transform credentials from liabilities into adaptive shields. As authentication landscapes evolve, continuous password strategy refinement isn't just prudent; it's existential.
Source: BleepingComputer (Sponsored by Specops Software)

Comments
Please log in or register to join the discussion