Security researchers have discovered significant vulnerabilities in current RISC-V CPU implementations, including a critical memory bypass flaw and multiple denial-of-service vulnerabilities, challenging the perception that RISC-V's open architecture inherently provides better security than x86_64.
Security researchers at Germany's CISPA Helmholtz Center for Information Security have delivered a sobering reality check for RISC-V enthusiasts, revealing that current CPU implementations fall significantly short of security expectations despite the architecture's open-source pedigree.
The Security Gap Between Theory and Practice
While RISC-V advocates often tout the architecture's open nature as inherently more secure than proprietary x86_64 designs, Fabian Thomas and Lukas Gerlach's research demonstrates that implementation matters more than specification. Their findings, presented at FOSDEM 2026 in Brussels, expose a troubling pattern of insecure defaults and unvalidated extensions across commercial RISC-V processors.
Critical Vulnerabilities Discovered
The researchers uncovered several alarming security flaws:
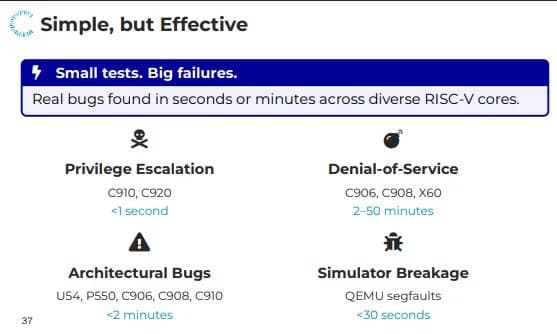
GhostWrite Vulnerability: A critical bug in T-Head's XuanTie C910 processor that allows unprivileged code to write directly to physical memory, completely bypassing virtual memory isolation. This represents a fundamental breakdown of one of computing's core security boundaries.
Cache+Time and CycleDrift Attacks: Novel side-channel attacks exploiting unprivileged access to instruction-retirement counters and cache-timing leakage, demonstrating that even "simple" in-order designs suffer from powerful microarchitectural vulnerabilities.
"Halt-and-Catch-Fire" Sequences: Multiple denial-of-service vulnerabilities that allow userspace code to crash entire CPUs, potentially enabling widespread disruption in shared computing environments.
The RISCover Framework: Automated Vulnerability Discovery
To address the scalability limitations of manual security analysis, the researchers developed RISCover, an open-source differential fuzzing framework that automatically discovers architectural vulnerabilities across closed-source RISC-V CPUs. By comparing instruction behavior across eight commercial CPUs from three different vendors, RISCover found vulnerabilities that manual analysis missed, highlighting the systematic nature of these security shortcomings.
Implementation Choices Undermining Security
The research reveals a concerning pattern: while the RISC-V specification provides strong security primitives like Physical Memory Protection (PMP) and cleaner privilege separation, implementations consistently choose insecure defaults. Vendors are shipping undocumented vendor extensions like XTheadVec without proper validation, leaving unprivileged timing sources enabled, and omitting features to limit speculation.
Linux Kernel Spectre Patch Lag
Adding to the security concerns, Linux kernel Spectre patches for RISC-V are only now making their way to mainline, years after similar mitigations were implemented for Arm and x86 processors. This delay leaves RISC-V systems vulnerable to well-known speculative execution attacks that have been addressed in other architectures.
The Inflection Point
The researchers emphasize that RISC-V is at a critical juncture. The architecture is still young enough to fix these fundamental security issues, but adoption is accelerating rapidly. The decisions vendors make today—insecure defaults, unvalidated extensions, missing mitigations—will be baked into billions of chips that cannot be patched later.
Implications for the Ecosystem
These findings challenge the narrative that open-source architectures inherently provide better security. The research demonstrates that transparency alone doesn't guarantee security; rigorous implementation, validation, and secure defaults are equally crucial. As RISC-V moves from enthusiast hardware to mainstream adoption in everything from embedded systems to data centers, addressing these security gaps becomes increasingly urgent.
For those interested in the technical details, the full FOSDEM 2026 presentation, including video recording and slide deck, is available at FOSDEM.org. The research serves as a crucial wake-up call for the RISC-V ecosystem, highlighting that security must be a priority from the ground up, not an afterthought in the rush to market.
Comments
Please log in or register to join the discussion