Internet-wide scans reveal 7.8 million censorship systems that violate TCP protocol rules to inject block pages, creating potent DDoS amplifiers with amplification factors exceeding 2 million times.
Content filtering infrastructure deployed by governments and ISPs introduces critical vulnerabilities in global network security. When middleboxes designed for censorship bypass TCP protocol requirements to inject block pages, they inadvertently create powerful DDoS amplification vectors. Recent internet-wide scans reveal how these systems enable TCP reflection attacks at unprecedented scale.
Protocol Violations as Attack Enablers
TCP inherently resists spoofed reflection attacks through its three-way handshake requirement. Censorship middleboxes break this fundamental security property by injecting responses without validating session state. When presented with invalid TCP traffic containing a blocked hostname (e.g., wikileaks.org), these devices immediately inject a block page response. This design shortcut violates RFC 9293 requirements for TCP session establishment.
If networks permit source address spoofing—still prevalent in many regions—attackers can:
- Spoof victim IP addresses in TCP packets
- Send malformed requests to censorship systems
- Trigger block page injections reflected to victims
The amplification effect occurs because injected block pages (typically 5-50KB) significantly exceed attacker request sizes (77-79 bytes).
Scale and Behavioral Analysis
Scan results from February 2026 demonstrate alarming scale:
| Blocked Domain | Distinct Reflectors | Max Amplification | Avg Packets per Reflector |
|---|---|---|---|
| youporn.com | 7,800,378 | 1,131,487x | 1.79 |
| wikileaks.org | 6,761,041 | 2,160,868x | 2.01 |
| telegram.org | 6,713,687 | 103,255x | 1.11 |
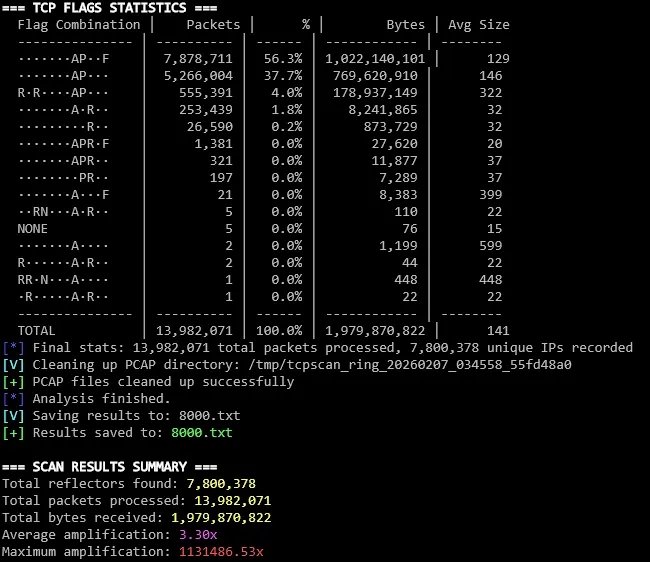 Terminal output showing scan results for pornography-blocking infrastructure
Terminal output showing scan results for pornography-blocking infrastructure
Key behavioral differences emerge based on content category:
- Pornography blocks: Widest attack surface (7.8M IPs) due to global blocking prevalence
- Whistleblower sites: Higher retransmission rates (2.01 packets/reflector) indicating state handling flaws
- Communication apps: Larger response sizes (avg 172 bytes/packet) with branded block pages
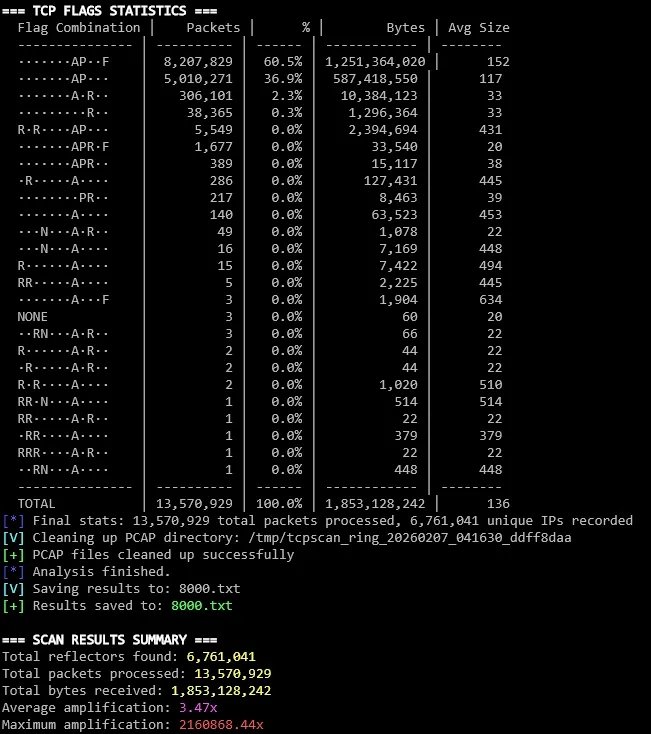 wikileaks.org scan showing extreme amplification patterns
wikileaks.org scan showing extreme amplification patterns
Amplification Mechanics
The worst-case amplification (over 2 million times) occurs via routing loops where injected packets re-enter filtering paths. This creates a feedback loop:
- Middlebox injects block page
- Packet traverses network path
- Another middlebox reprocesses the packet as new traffic
- New block page injected
This violates two core network principles:
- Protocol state consistency: Responses generated without session context
- Forwarding integrity: Improper TTL handling enables looping
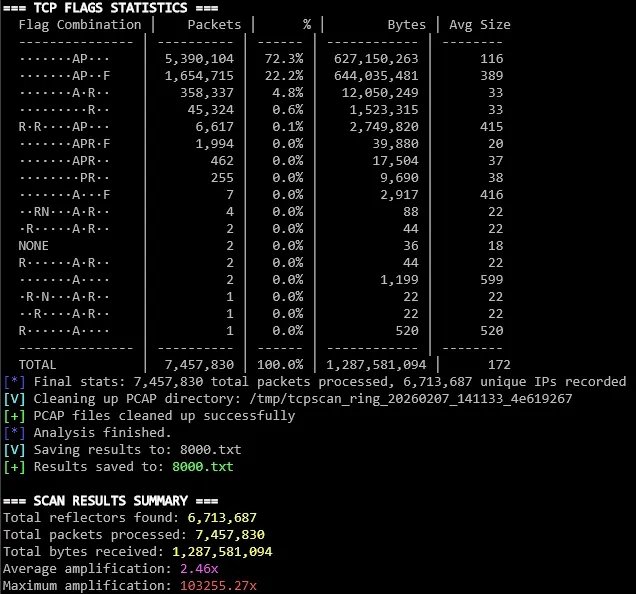 Telegram scan showing distinct response patterns
Telegram scan showing distinct response patterns
Attack Characteristics
Compared to UDP amplification, TCP reflection poses unique challenges:
| Characteristic | UDP Amplification | TCP Middlebox Reflection |
|---|---|---|
| Source legitimacy | Limited IP ranges | Millions of ISP/government IPs |
| Payload appearance | Easily identifiable | Mimics legitimate HTTP |
| Mitigation complexity | Known patterns | Requires deep packet inspection |
| Trigger mechanism | Fixed services | Content-dependent filtering |
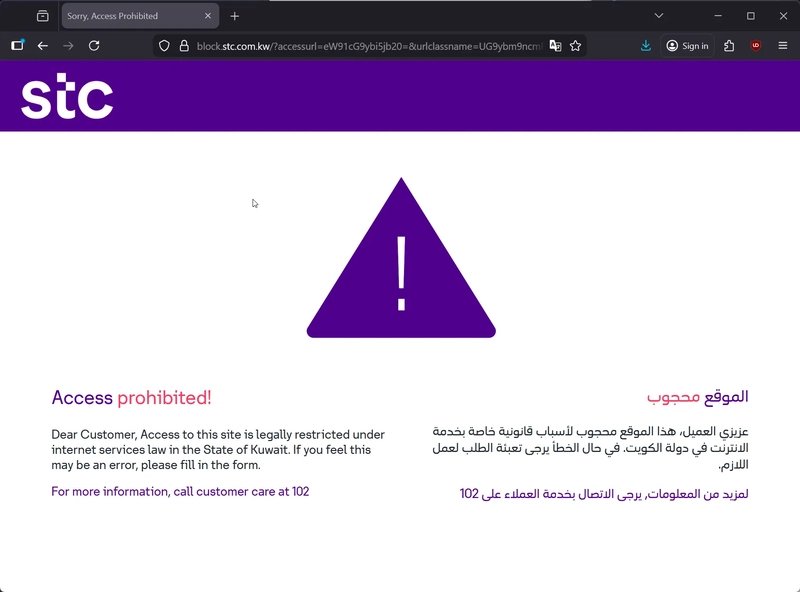 Kuwait STC block page example showing injected content
Kuwait STC block page example showing injected content
Systemic Trade-offs
Filtering efficacy directly correlates with attack potential:
- Basic blocking (TCP RST): Minimal amplification but easily circumvented
- Rich block pages: High user compliance but creates potent amplifiers
- Stateful inspection: Better security but higher resource requirements
Nations face impossible choices: Effective censorship requires protocol violations that create attack vectors exploitable by both external threat actors and internal dissidents.
Mitigation Pathways
Network Operators:
Middlebox Developers:
- Enforce full TCP handshake before injection
- Implement strict TTL validation
- Adhere to RFC 9293 session states
Governments:
- Accept that censorship efficacy inversely correlates with network security
- Audit systems for routing loop vulnerabilities
Protocol Integrity vs Content Control
This vulnerability represents a fundamental systems trade-off: Content filtering requires violating protocol-layer security guarantees. As national filtering systems expand, they create increasingly dangerous attack surfaces. The 7.8 million reflectors found in 2026 demonstrate how security shortcuts in distributed systems create internet-scale risks far beyond their intended purpose.
Prior Research:
- Bock et al. USENIX Security 2021 (Distinguished Paper Award)
- Akamai 2022 Attack Analysis
- Shadowserver Vulnerability Scan
Comments
Please log in or register to join the discussion