Security expert Micah Lee reveals how U.S. agencies like ICE are weaponizing mercenary spyware and device exploitation tools against citizens, while tech giants enable censorship. Learn critical defenses including Lockdown Mode, encrypted backups, and the urgent need for security culture.
The Age of Technofascism: Mercenary Spyware, Device Searches, and Platform Censorship

At the BSidesPDX conference, security researcher Micah Lee delivered a stark warning: The U.S. has entered an era of "technofascism" where government agencies like ICE are deploying invasive surveillance tools previously reserved for foreign targets against domestic populations. Private spyware firms and tech giants have become willing collaborators in this new landscape.
Mercenary Spyware Goes Mainstream
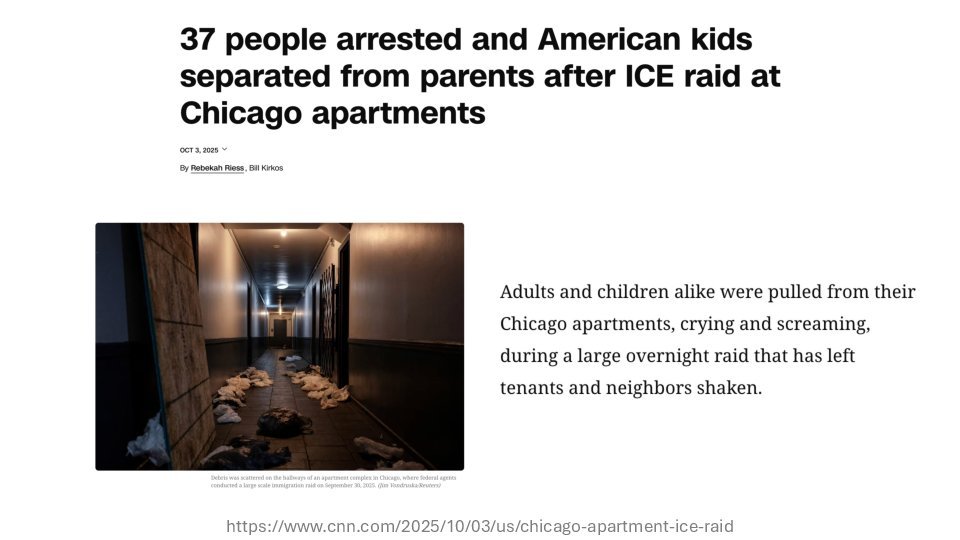
"Under Trump, the American disregard for human rights has turned inward," Lee stated. ICE recently activated an $11 million contract with Paragon Solutions (now U.S.-owned via REDLattice) for its Graphite spyware. Marketed as an "ethical alternative" to NSO Group's Pegasus, Graphite specifically targets encrypted messaging apps like Signal and WhatsApp via zero-click exploits.

Evidence shows Graphite was already abused against European journalists, exploiting vulnerabilities like CVE-2023-41064 in iMessage. Disturbingly, American investors recently acquired NSO Group itself, signaling further normalization of these tools.
Critical Defenses:
- Update Relentlessly: Zero-day exploits cost millions; patched vulnerabilities are free. Delay = vulnerability.
- Enable Lockdown Mode (iOS/macOS): No documented bypasses exist. Disables high-risk vectors like complex web fonts.
- Activate Advanced Data Protection (iCloud) or Android Advanced Protection: Prevents cloud backups from becoming government backdoors.
- Upgrade to iPhone 17+: Its Memory Integrity Enforcement hardware blocks entire exploit classes via memory tagging.
Device Searches: The Physical Threat
ICE's $11 million Cellebrite contract enables mass device exploitation during arrests. Cellebrite tools brute-force passcodes, bypass lock screens via vulnerabilities, and extract full device contents. Recent cases in Hong Kong and Russia show devices returned after seizure often contain implanted spyware.
Survival Strategies:
- Power Off at Checkpoints/Protests: Full shutdown strengthens disk encryption protection.
- Ditch Biometrics: Use long alphanumeric passcodes (10+ characters). Biometrics can be forcibly applied.
- Secondary Devices: Carry wiped phones with minimal apps/Signal contacts for high-risk situations.
- Minimize Data Retention: Enable disappearing messages in Signal. Delete non-essential data routinely.
Platform Collaboration: The Censorship Pipeline
Tech platforms actively assist censorship campaigns. Apple removed the ICEBlock app—which crowdsourced ICE sightings—after the DOJ requested it, falsely classifying ICE agents as a "targeted group." Google banned similar app Red Dot, while Meta deleted an 80,000-member "ICE Sighting" Facebook group. Even Eyes Up—a web app documenting ICE abuses—was banned from Apple's App Store.
Resistance Tactics:
- Build Web-First Tools: Websites resist app store takedowns (e.g., EyesUpApp.com remains live).
- Abandon WhatsApp: Its metadata is vulnerable to warrants. Use Signal with Sealed Sender enabled.
- Prepare for Censorship: Study circumvention tools from repressed regions (Tor, Snowflake, decentralized hosting).
The Imperative: Security Culture
"Individual hardening isn't enough," Lee emphasized. "Fascists target communities. Our defenses must be collective." Key recommendations:
- Educate Your Network: Help others enable Lockdown Mode, Advanced Protection, and strong passcodes.
- Contact Access Now's Helpline if devices are seized or compromised.
- Build In-Person Networks: Digital tools will be targeted; real-world community bonds are resilient.
"When they come for your neighbors, the worst response is to stare at your phone. We need solidarity and shared security practices now," Lee concluded, stressing that in the age of technofascism, community protection is everyone's responsibility.
Source: Micah Lee's BSidesPDX keynote and accompanying article

Comments
Please log in or register to join the discussion