Discover how secret dialer codes can reveal hidden menus, diagnostic tools, and carrier features on your iPhone or Android device. From checking IMEI to enabling call forwarding, these hacks offer power users new ways to interact with their tech—but some come with serious risks.

Your smartphone holds more secrets than you might realize. Beyond the familiar settings menus lie hidden features accessible through simple codes entered directly into your phone's dialer. These sequences—often starting with *# or ##—unlock engineering dashboards, carrier tools, and diagnostic panels typically reserved for technicians or developers. While some provide everyday utility, others wield enough power to erase your entire device with a single tap.
I recently explored these hidden pathways on both iOS and Android, testing codes compiled from industry sources and ZDNET's investigative work. What I found is a fascinating glimpse into the layered architecture of modern mobile devices—and a reminder that with great power comes great responsibility.
What These Codes Reveal
Here’s a breakdown of the most useful and intriguing codes, based on hands-on verification:
*#06#: Instantly displays your device’s IMEI (International Mobile Equipment Identity) and EID for eSIMs—critical for theft reports or carrier unlocks. Works on iPhone and Android.*3001#12345#*: Opens iPhone’s Field Test Mode (FTM) Dashboard, showing real-time network data like signal strength in dBm, carrier details, and cell tower connections. iPhone only.*#*#4636#*#*: Accesses Android’s testing panel with deep diagnostics for battery, network, and app usage. Ideal for developers troubleshooting connectivity. Android only.*#67#or*#21#: Checks call-forwarding status (e.g., when busy or for all calls). Carrier-dependent, but invaluable for managing workflows. Works on both platforms where supported.*21[number]#: Forwards all calls to another number instantly—no settings menu needed. Carrier-dependent on iPhone/Android.#225(Verizon),*225#(AT&T),#225#(T-Mobile): Texts your current bill balance. A quick alternative to app logins. Carrier-specific.
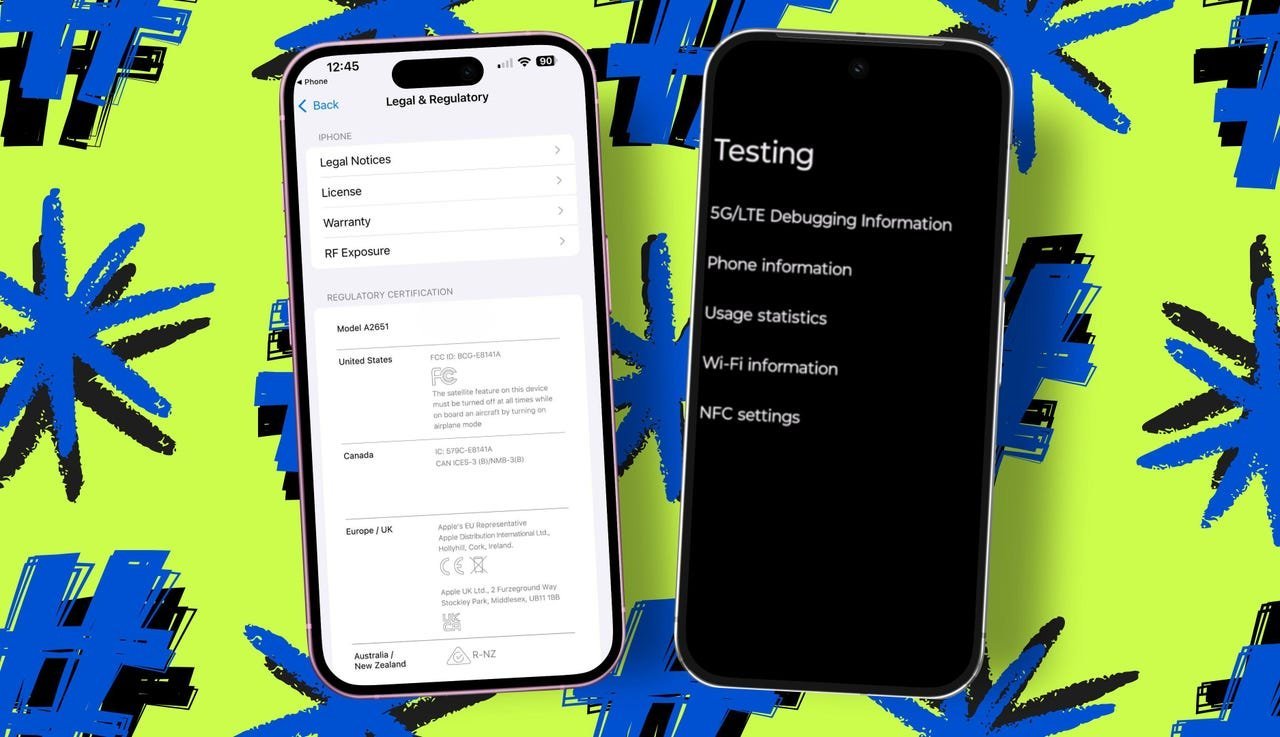 Image: Elyse Betters Picaro / ZDNET demonstrating secret code access.
Image: Elyse Betters Picaro / ZDNET demonstrating secret code access.
Proceed with Caution
Not all codes are benign. *2767*3855# triggers an immediate factory reset on Android devices—no confirmation prompts. I avoided testing this for obvious reasons, but it underscores why these tools demand respect. Similarly, *5005*25370# disables emergency alerts on iPhones, which could have serious safety implications if misused.
Why This Matters for Tech Professionals
For developers, codes like Android’s #*#4636#*#* offer raw access to system metrics that aid in optimizing app performance or diagnosing network issues. Security teams should note how easily features like call forwarding (*21[number]#) can be manipulated, posing risks if a device is compromised. Meanwhile, the carrier-specific nature of many codes highlights the fragmented control networks wield over device functionality—a pain point for engineers advocating for standardized APIs.
Carrier limitations also reveal broader industry tensions. As one network engineer told me, "These codes are remnants of telecom’s walled gardens. They remind us that true device autonomy remains elusive."
The Delicate Dance of Discovery
Exploring these hidden menus feels like uncovering buried treasure, but it’s not without peril. While checking your data usage via #3282 (Verizon) is harmless, venturing into engineering modes could inadvertently alter settings. Always back up your device before experimenting, and remember: if a code seems obscure, it’s likely meant for specialists, not casual users.
In a world where smartphones feel increasingly locked down, these codes are a rare portal to the machinery beneath the glass. They empower us to tweak, troubleshoot, and take control—but only if we wield them wisely.
Source: ZDNET article by Elyse Betters Picaro, September 8, 2025.

Comments
Please log in or register to join the discussion