Shocking research by Modat reveals over 1.2 million healthcare devices globally are exposed on the open internet, leaking sensitive patient MRI scans, X-rays, bloodwork results, and PHI. Misconfigurations, default passwords, and unpatched systems create pathways for data theft, fraud, and ransomware attacks, turning cybersecurity into a critical patient safety issue. This systemic failure underscores the urgent need for healthcare providers to reassess network security fundamentals.
Imagine undergoing an MRI, trusting your sensitive health data remains confidential, only to discover strangers could access your brain scans and diagnosis online—potentially before your doctor reviews them. This isn't dystopian fiction; it's the chilling reality uncovered by cybersecurity firm Modat. Their research exposes a massive global failure: over 1.2 million healthcare devices and systems are accessible on the open internet, leaking protected health information (PHI) and personally identifiable information (PII) of patients worldwide.
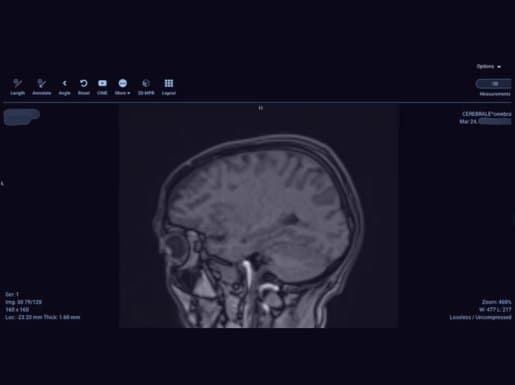
 Figure 1: Example of exposed PHI – A skull X-ray accessible online (Source: Modat)
Figure 1: Example of exposed PHI – A skull X-ray accessible online (Source: Modat)
Using their Modat Magnify platform—a tool designed to fingerprint and catalogue internet-connected devices via unique 'device DNA'—researchers identified these vulnerable systems through a HEALTHCARE tag query. The findings are alarming:
- Exposed Data Types: Confidential MRI scans, X-rays (dental, chest, skeletal), optical exam results, bloodwork (including vitals and biometrics), all often stored alongside patient names, diagnoses, and scan dates.
- Geographic Spread: Devices were found globally, with the highest concentrations in the United States (174,000+), South Africa (172,000+), Australia (111,000+), Brazil (82,000+), Germany (81,000+), Ireland (81,000+), Great Britain (77,000+), France (75,000+), Sweden (74,000+), and Japan (48,000+).
 Figure 4: Global map showing geographic distribution of exposed healthcare devices (Source: Modat)
Figure 4: Global map showing geographic distribution of exposed healthcare devices (Source: Modat) - Direct Access: Researchers demonstrated access to clickable lists of patient scans and records, including systems allowing editing capabilities, showcasing the terrifying ease of exploitation.
Why Is This Happening? A Triad of Failures
The root causes are depressingly familiar yet critically unaddressed in many healthcare environments:
- Misconfigurations & Insecure Settings: Complex network setups often lead to devices being unnecessarily connected directly to the internet. Administrators may apply default 'connect everything' strategies without considering the specific security needs of medical equipment like MRI scanners. As Modat CEO Soufian El Yadmani states:
"The question we should be asking is: Why are there MRI scanners with internet connectivity that lack proper security measures?"
- Default or Weak Credentials: Many devices ship with factory-set passwords (
admin,demo,123456), which are frequently never changed. Shared defaults across device models create widespread risk if one is compromised. Weak, easily guessable passwords are also commonplace. - Unpatched & Legacy Systems: Patching critical vulnerabilities in medical systems is notoriously difficult due to operational constraints and fear of downtime. Many exposed devices run outdated firmware or software with known, exploitable flaws, or are end-of-life systems receiving no security updates.
Beyond Data Theft: Critical Infrastructure at Risk
The exposure goes far beyond privacy violations. These misconfigured devices act as potential entry points for devastating cyberattacks:
- Ransomware Gateway: Attackers specifically target healthcare knowing hospitals cannot afford prolonged downtime. A vulnerable internet-facing medical device is a perfect foothold to launch ransomware across the entire network, crippling patient care.
- Data Manipulation: While theft is bad, the potential for altering medical records or scan results poses an even graver threat to patient safety and treatment outcomes.
- Blackmail & Fraud: Access to sensitive diagnoses (e.g., cancer, mental health conditions) creates opportunities for extortion and financial fraud against vulnerable individuals.
Errol Weiss, Chief Security Officer at Health-ISAC, emphasized the gravity:
"This research reinforces the urgent need for comprehensive asset visibility, robust vulnerability management, and a proactive approach to securing every internet-connected device in healthcare environments... cybersecurity is inextricably linked to patient safety and operational continuity."
The Path to Securing Healthcare's Digital Backbone
Modat engaged in responsible disclosure with organizations like Health-ISAC and Z-CERT (Netherlands) to notify affected entities. Their findings point to essential remediation steps:
- Radical Reduction of Attack Surface: The primary lesson is stark: if a device doesn't absolutely require internet access for a critical clinical function, it shouldn't be exposed. Network segmentation and strict access controls are non-negotiable.
- Proactive Asset & Vulnerability Management: Maintain a real-time, comprehensive inventory of all network-connected devices (IoMT - Internet of Medical Things). Continuously scan for misconfigurations, exposures, and vulnerabilities.
- Rigorous Credential Hygiene: Mandate strong, unique passwords for all devices and systems. Eliminate default credentials immediately upon deployment.
- Prioritized Patching & Legacy Mitigation: Establish feasible, risk-based patching protocols for critical systems. Develop mitigation strategies for legacy or unsupported devices that cannot be patched, prioritizing their isolation.
Wim Hafkamp, Director of Z-CERT, highlighted the value of external research:
*"These extra sets of eyes help us keep Dutch healthcare digitally secure. Thanks to their findings we have been able to inform and advise several healthcare organizations."
The exposure of 1.2 million devices isn't just a statistic; it's a systemic failure with human consequences. Securing these systems isn't merely an IT task—it's fundamental to upholding the oath to protect patients. As medical technology advances, the foundational security practices protecting it must advance with equal urgency. The integrity of diagnoses and the sanctity of patient trust depend on it.
Source: Modat Research Report - "Over 1.2 Million Healthcare Devices and Systems Available on the Open Internet"
Comments
Please log in or register to join the discussion